First April SSTIC challenge
Posted on 02 Apr 2015 in Security • 5 min read
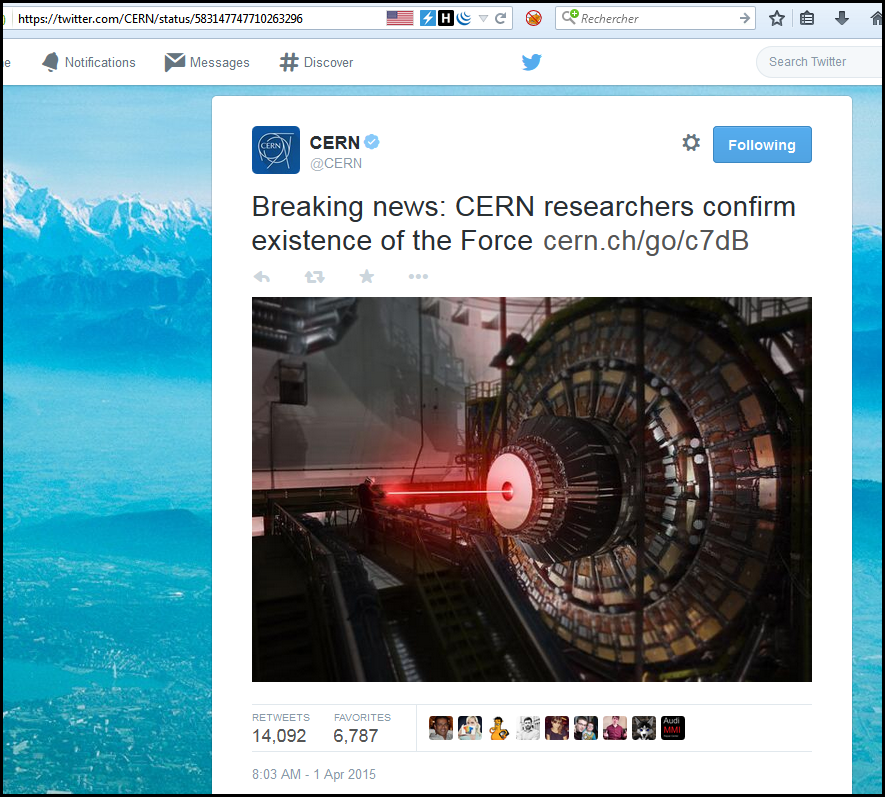
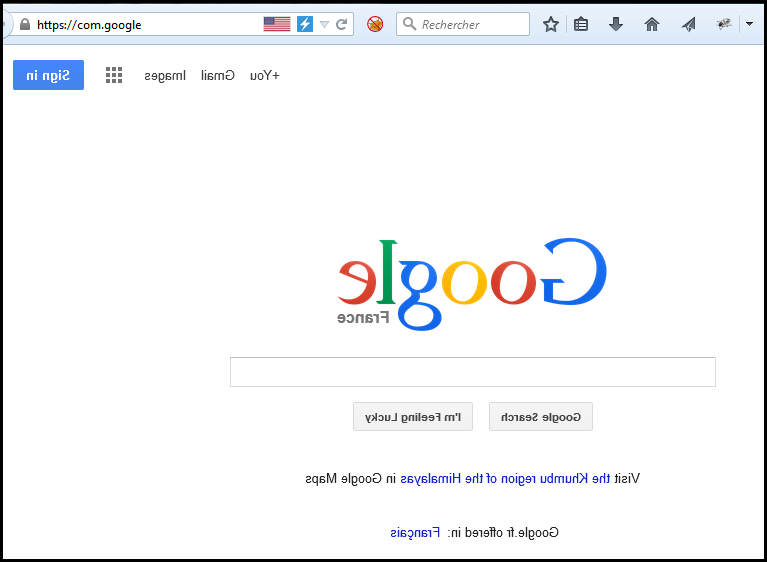
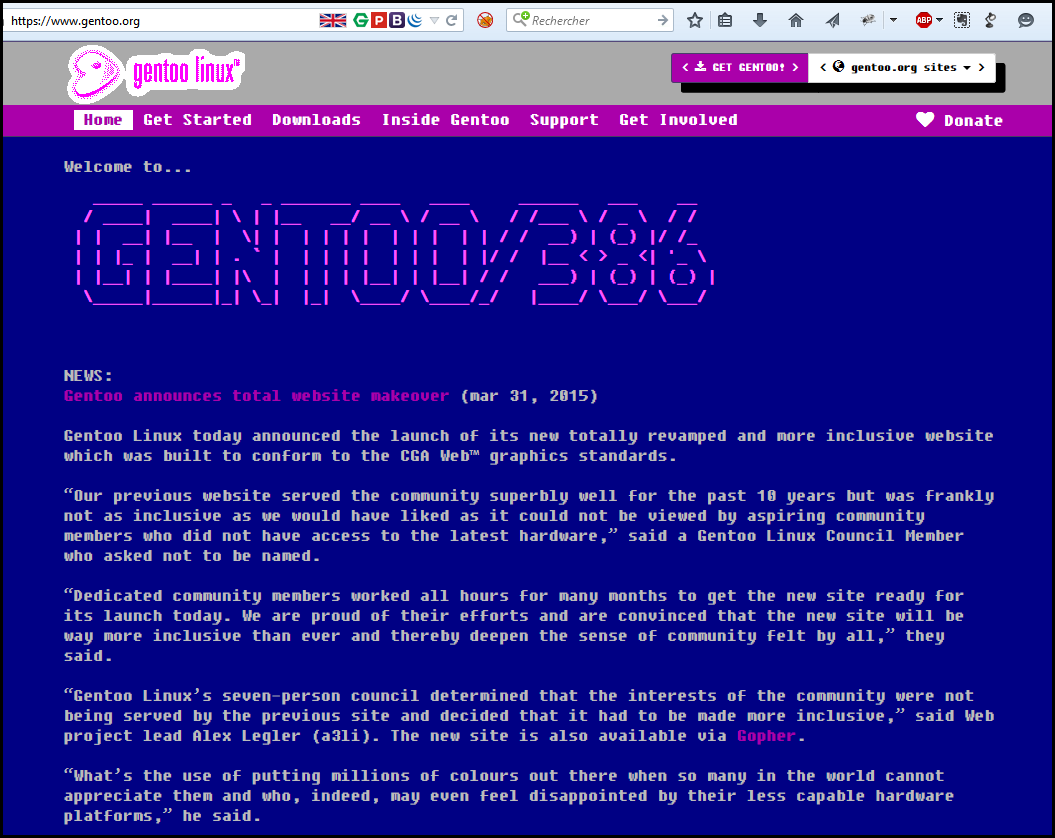
The first of April is always the occasion for some great pranks. 2015 was a great year, as the CERN confirmed the existence of the Force, Google published a mirroring website and gentoo an old fashion one. In France we got a security event call SSTIC for which the tickets are very rare therefore the SSTIC challenge allows the ones with the flag to reserve a ticket. An April prank challenge was post yesterday.
April Pranks
The first of April is always the occasion for some great pranks:
- Google do some mirroring trick(deadlink):
SSTIC Challenge
But one of them was released by the SSTIC an French security event which give every year a difficult challenge that grant automatically a place to the event (tickets are sold out in approximately one minute) for the winners.
We download the challenge here.
Strings
Let's try something like strings to see what appends:
maggick@debian:~/work/sstic$ strings chlg-2015 | wc -l
10797
maggick@debian:~/work/sstic$ strings chlg-2015 | head
Salted__D
8'<K
vKRbn
vKRbn
vKRbn
vKRbn
K5G--9S
%Pz$
vKRbn
vKRb
No chance coming from here.
Hexview
We use radare2 to see the hexcode:
[0x00000000 0% 1008 chlg-2015]> x
- offset - 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
0x00000000 5361 6c74 6564 5f5f 4419 80b6 425f d4ff Salted__D...B_..
0x00000010 1e5c 83a1 c4d7 24f5 4697 9aac 2571 5f8e .\....$.F...%q_.
0x00000020 64e2 52ad 8947 119e c4ad 929b 6505 4de2 d.R..G......e.M.
0x00000030 ff44 0add d438 273c 4b8d 760d 416d c883 .D...8'<K.v.Am..
0x00000040 290e 8014 1ce7 88a2 b6c7 cd00 d8e9 98bd )...............
0x00000050 e40c cb76 4b52 626e 0ee0 c966 b1c8 c24b ...vKRbn...f...K
0x00000060 e40c cb76 4b52 626e 0ee0 c966 b1c8 c24b ...vKRbn...f...K
0x00000070 4915 cd03 153c 5210 abe7 c68f c882 f198 I....<R.........
0x00000080 f153 28d9 ef43 0ecc d38a 8cc7 7cff 5351 .S(..C......|.SQ
0x00000090 ad07 b6ef c462 dffe ad31 8a95 01a1 4390 .....b...1....C.
0x000000a0 ad07 b6ef c462 dffe ad31 8a95 01a1 4390 .....b...1....C.
0x000000b0 ad07 b6ef c462 dffe ad31 8a95 01a1 4390 .....b...1....C.
0x000000c0 ad07 b6ef c462 dffe ad31 8a95 01a1 4390 .....b...1....C.
0x000000d0 ad07 b6ef c462 dffe ad31 8a95 01a1 4390 .....b...1....C.
0x000000e0 ad07 b6ef c462 dffe ad31 8a95 01a1 4390 .....b...1....C.
0x000000f0 ad07 b6ef c462 dffe ad31 8a95 01a1 4390 .....b...1....C.
0x00000100 ad07 b6ef c462 dffe ad31 8a95 01a1 4390 .....b...1....C.
0x00000110 ad07 b6ef c462 dffe ad31 8a95 01a1 4390 .....b...1....C.
0x00000120 ad07 b6ef c462 dffe ad31 8a95 01a1 4390 .....b...1....C.
0x00000130 ad07 b6ef c462 dffe ad31 8a95 01a1 4390 .....b...1....C.
0x00000140 ad07 b6ef c462 dffe ad31 8a95 01a1 4390 .....b...1....C.
0x00000150 ad07 b6ef c462 dffe ad31 8a95 01a1 4390 .....b...1....C.
Yeah that a message encrypt with open ssl and salt. But we do not have any idea about the key nor the salt. Shall we take a look at the code itself:
[0x00000000 0% 315 chlg-2015]> pd $r
0x00000000 53 push ebx
0x00000001 61 popal
0x00000002 6c insb byte es:[edi], dx
,=< 0x00000003 7465 je 0x6a ;[1]
| 0x00000005 645f pop edi
| 0x00000007 5f pop edi
| 0x00000008 44 inc esp
| 0x00000009 1980b6425fd4 sbb dword [eax - 0x2ba0bd4a], eax
| 0x0000000f ff1e lcall [esi]
| unk()
| 0x00000011 5c pop esp
| 0x00000012 83a1c4d724f. and dword [ecx - 0xadb283c], 0x46
| 0x00000019 97 xchg eax, edi
| 0x0000001a 9aac25715f8. lcall 0x648e:0x5f7125ac ;[2]
| 0x0000648e()
,==< 0x00000021 e252 loop 0x75 ;[3]
|| 0x00000023 ad lodsd eax, dword [esi]
|| 0x00000024 894711 mov dword [edi + 0x11], eax ; [0x11:4]=0xc4a1835c
|| 0x00000027 9e sahf
|| 0x00000028 c4ad929b6505 les ebp, [ebp + 0x5659b92]
|| 0x0000002e 4d dec ebp
,===< 0x0000002f e2ff loop 0x30 ;[4]
|| 0x00000031 44 inc esp
|| 0x00000032 0add or bl, ch
|| 0x00000034 d438 aam 0x38
|| 0x00000036 27 daa
|| 0x00000037 3c4b cmp al, 0x4b ; 'K'
|| 0x00000039 8d760d lea esi, [esi + 0xd] ; [0xd:4]=0x1effd45f
|| 0x0000003c 41 inc ecx
|| 0x0000003d 6d insd dword es:[edi], dx
|| 0x0000003e c883290e enter 0x2983, 0xe
|| 0x00000042 80141ce7 adc byte [esp + ebx], -0x19
|| 0x00000046 88a2b6c7cd00 mov byte [edx + 0xcdc7b6], ah ; [0xcdc7b6:1]=255
|| 0x0000004c d8e9 fsubr st(1)
|| 0x0000004e 98 cwde
|| 0x0000004f bde40ccb76 mov ebp, 0x76cb0ce4
|| 0x00000054 4b dec ebx
|| 0x00000055 52 push edx
|| 0x00000056 626e0e bound ebp, qword [esi + 0xe]
|| 0x00000059 e0c9 loopne 0x24
|| 0x0000005b 66b1c8 mov cl, -0x38
|| 0x0000005e c24be4 ret 0xe44b
|| 0x00000061 0ccb or al, 0xffffffcb
,====< 0x00000063 764b jbe 0xb0 ;[5]
| || 0x00000065 52 push edx
| || 0x00000066 626e0e bound ebp, qword [esi + 0xe]
| || 0x00000069 e0c9 loopne 0x34
| | 0x0000006b 66b1c8 mov cl, -0x38
| | 0x0000006e c24b49 ret 0x494b
| | 0x00000071 15cd03153c adc eax, 0x3c1503cd
| 0x00000076 52 push edx
| 0x00000077 10abe7c68fc8 adc byte [ebx - 0x37703919], ch
| 0x0000007d 82f198 xor cl, 0x98
| 0x00000080 f1 int1
| 0x00000081 53 push ebx
| 0x00000082 28d9 sub cl, bl
| 0x00000084 ef out dx, eax
| 0x00000085 43 inc ebx
| 0x00000086 0e push cs
| 0x00000087 cc int3
| 0x00000088 d38a8cc77cff ror dword [edx - 0x833874], cl
| 0x0000008e 53 push ebx
| 0x0000008f 51 push ecx
| 0x00000090 ad lodsd eax, dword [esi]
| 0x00000091 07 pop es
| 0x00000092 b6ef mov dh, -0x11
| 0x00000094 c462df les esp, [edx - 0x21]
| 0x00000097 fe invalid
| 0x00000098 ad lodsd eax, dword [esi]
| 0x00000099 318a9501a143 xor dword [edx + 0x43a10195], ecx
| 0x0000009f 90 nop
| 0x000000a0 ad lodsd eax, dword [esi]
| 0x000000a1 07 pop es
| 0x000000a2 b6ef mov dh, -0x11
| 0x000000a4 c462df les esp, [edx - 0x21]
| 0x000000a7 fe invalid
| 0x000000a8 ad lodsd eax, dword [esi]
| 0x000000a9 318a9501a143 xor dword [edx + 0x43a10195], ecx
| 0x000000af 90 nop
| 0x000000b0 ad lodsd eax, dword [esi]
| 0x000000b1 07 pop es
| 0x000000b2 b6ef mov dh, -0x11
| 0x000000b4 c462df les esp, [edx - 0x21]
| 0x000000b7 fe invalid
| 0x000000b8 ad lodsd eax, dword [esi]
| 0x000000b9 318a9501a143 xor dword [edx + 0x43a10195], ecx
| 0x000000bf 90 nop
| 0x000000c0 ad lodsd eax, dword [esi]
| 0x000000c1 07 pop es
| 0x000000c2 b6ef mov dh, -0x11
| 0x000000c4 c462df les esp, [edx - 0x21]
| 0x000000c7 fe invalid
| 0x000000c8 ad lodsd eax, dword [esi]
| 0x000000c9 318a9501a143 xor dword [edx + 0x43a10195], ecx
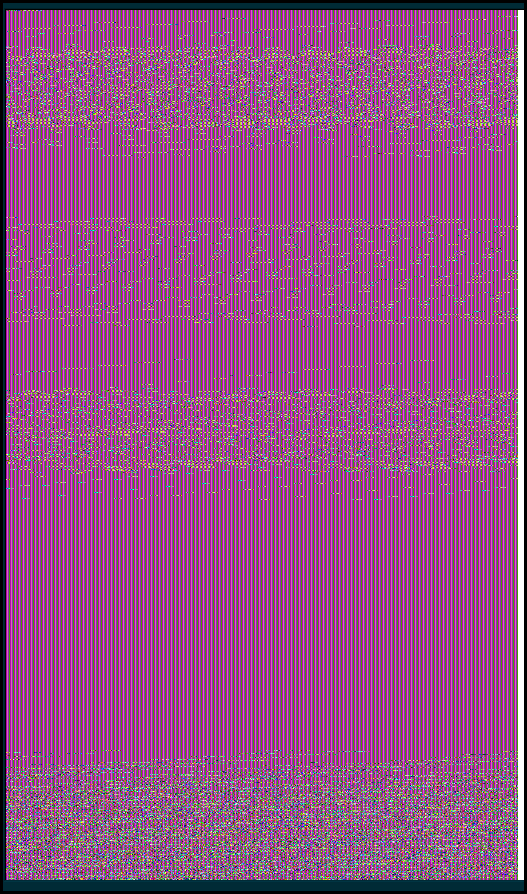
Pixel
There seems to be some repetition in this code, let's open it with the dff to
see if this is an
ECB image.
We launch the dff hex viewer and look at it as a pixel image:
With the default resolution of 512 it does not look very pretty, let's variate the resolution a bit. With a resolution of 563 we got something that encourage us to persevere in this way:
At the resolution of 750 we got something pretty:
Got you !
We just need to open it, turn it upside down and mirroring it to get the final result:
Very much thanks to anyfun for the big help and the dff hints.