Advent of Code 2023
Posted on 02 Jan 2024 in programming • Tagged with adventofcode, challenge • 5 min read

I participated in the first few days of advent of code 2023. Here are my though. Solutions are available on GitHub.
Continue reading
Posted on 02 Jan 2024 in programming • Tagged with adventofcode, challenge • 5 min read

I participated in the first few days of advent of code 2023. Here are my though. Solutions are available on GitHub.
Posted on 17 Nov 2023 in programming • Tagged with spotify, music • 2 min read
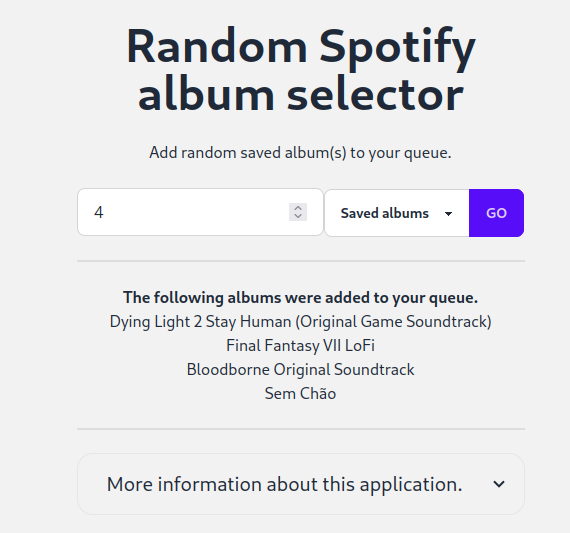
tl;dr: go to Spotify_RAS. A tool that choose Spotify albums from your saved ones and add them to your playing queue.
I listen to music all day. Mostly Video game music and I have been collecting albums for years. As a result I have around 400 albums saved in Spotify (and still growing), so every morning choosing my soundtrack of the day was a complex task and I end up listening a lot to the same albums.
Posted on 25 May 2023 in security • Tagged with security, CVE-2022-44268, ImageMagick, SSTIC • 7 min read
As each year the French Security conference SSTIC release a security challenge prior to the conference.
This year the challenge seemed "easier" than the previous year as the stage 1 got 135 validations versus 86 validations in 2022.
This article will detail my solution for the step 0 and the step 1.
Posted on 02 May 2023 in security • Tagged with security, ctf, web, SSTI • 7 min read
Posted on 22 Oct 2022 in security • Tagged with security, XSS • 3 min read
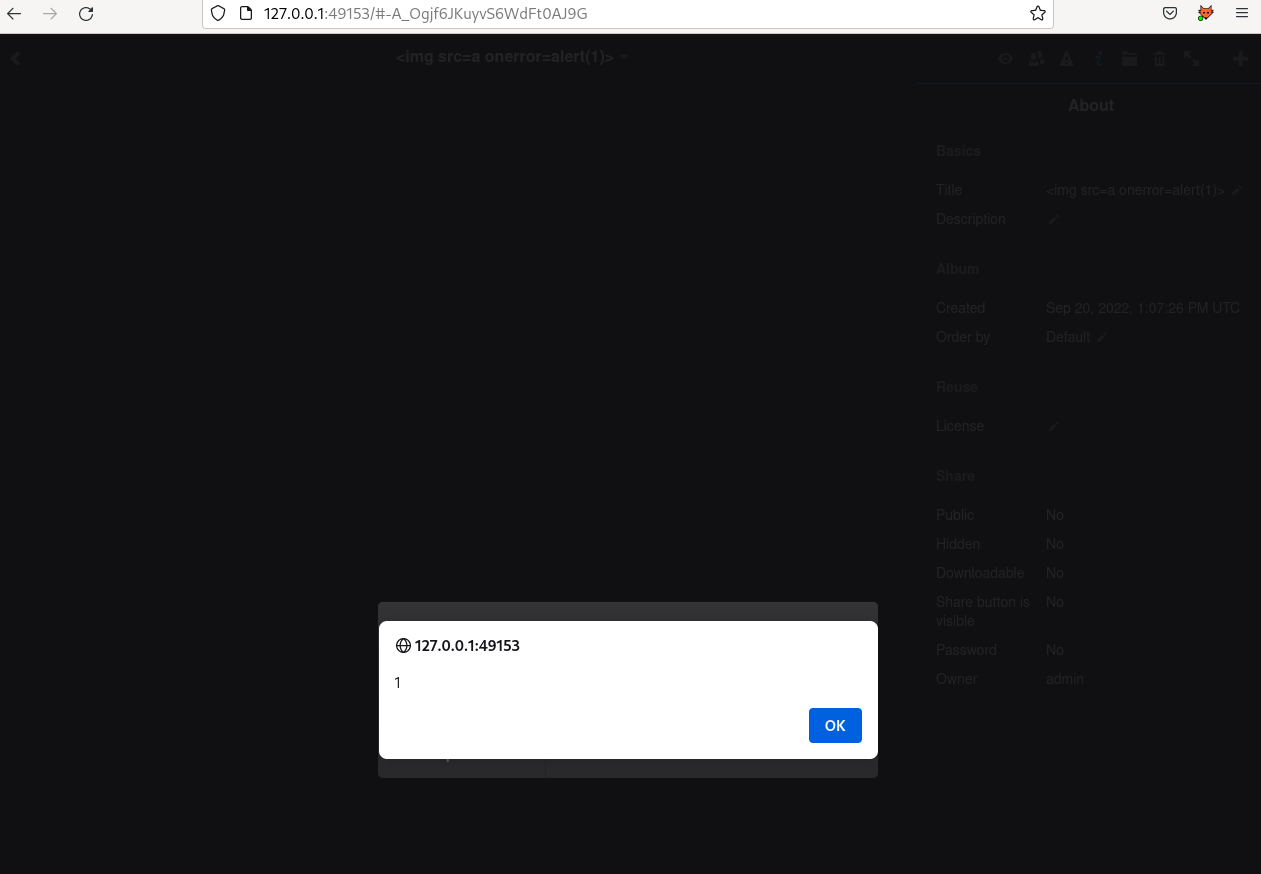
Lychee is a self-hosted photo-management and gallery. I am using the Lychee application for my personal usage (mostly sharing pictures with the family).
The application has been greatly improved since the last update of my instance. I fired up a docker and start taking a look at the application for new features. It was not long before I found a few XSS, one of them could allow unauthenticated users to to gain logged access to the platform by creating a new account.
I reported the issues to the project and we created a Github Security Advisory: https://github.com/LycheeOrg/Lychee-front/security/advisories/GHSA-cr79-38hg-27gv.
Posted on 22 Aug 2022 in security • Tagged with security, boot2root, HTB, SSTI, SUID, OCR • 3 min read
This article is a writeup about a retired HacktheBox machine: Late publish on April 23, 2022 by kavigihan. This box is rated as an easy machine. It implies an OCR function, a SSTI and a SUID binary.
Posted on 22 Aug 2022 in security • Tagged with security, boot2root, HTB, SMB, LAPS • 6 min read
This article is a writeup about a retired HacktheBox machine: Timelapse publish on Mars 2022 by d4rkpayl0ad. This box is rated as an easy machine. It implies a SMB share, a encrypted zip archive, a certificate, a password in a shell history and LAPS.
Posted on 19 Jun 2022 in security • Tagged with security, boot2root, HTB, Wordpress, CVE-2019-17671 (wordpress), CVE-2021-3560 (polkit) • 5 min read
This article is a writeup about a retired HacktheBox machine: Paper publish on February 05, 2022 by secnigma. This box is rated as an easy machine. It implies a verbose header, a vulnerable WordPress a rocket chat bot and the PolKit exploit.
Posted on 12 Jun 2022 in security • Tagged with security, boot2root, HTB, subdomain, exiftool, ImageMagick, neofetch • 4 min read
This is a writeup about a retired HacktheBox machine:
Meta publish on
January 22, 2022 by
Nauten.
This box is rated as a medium machine. It implies subdomain enumeration, a
vulnerability in exiftool, another on in ImageMagick and a too permissive
sudo command.
Posted on 11 Jun 2022 in security • Tagged with security, osint, phone number • 4 min read

While browsing on the Internet,
I founded a strange functionality forgot username?. Everyone know about the forgot password one that
often imply to input the user email address and get a link to reset ones password. So what is that
forgot username? thing?