Forgot username?
Posted on 11 Jun 2022 in security • 4 min read

While browsing on the Internet,
I founded a strange functionality forgot username?. Everyone know about the forgot password one that
often imply to input the user email address and get a link to reset ones password. So what is that
forgot username? thing?
Disclaimer: This was discovered in 2020 and was forgotten on my computer since then. The attack vectors described bellow might have changed.
Taking over old accounts
Yahoo!
While browsing on the Internet,
I founded a strange functionality forgot username?. Everyone all know about the forgot password one that
often imply to input the user email address and get a link to reset ones password.
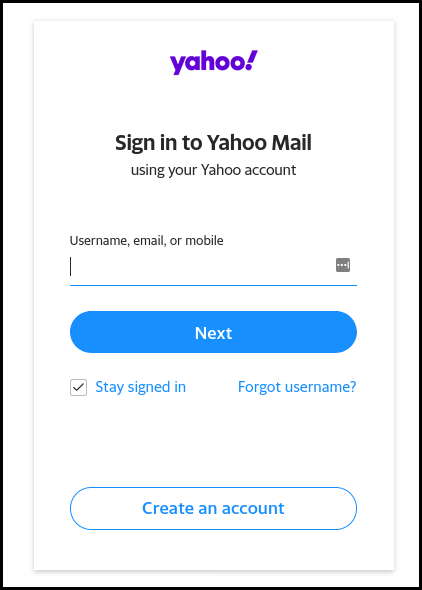
When clinking on the link, the user was prompted to either put its email address - its username right? - or a phone number.
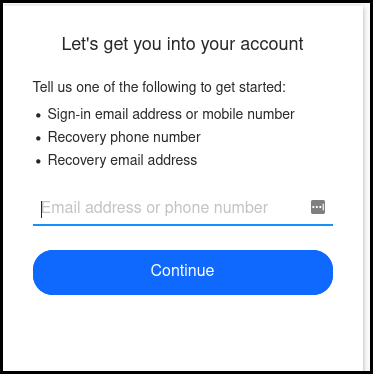
When putting a phone number there were two outputs cases:
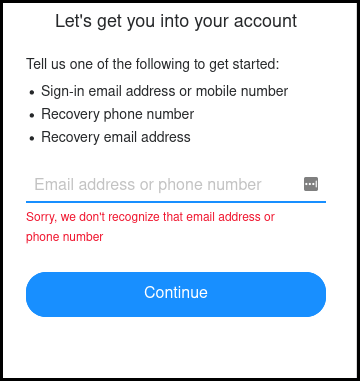
One: the phone number was not recognized and the page display it as an error message.
Two: the phone number was in the database and Yahoo! would ask if I wanted to get a password
reset code on the phone number.
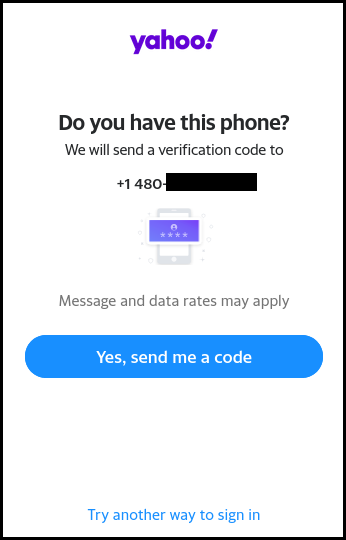
Obviously when clicking yes a text message was sent to the phone number and I was able to
reset its account's password and access the profile data - I only connected that on accounts I owned for ethic and legal reasons.
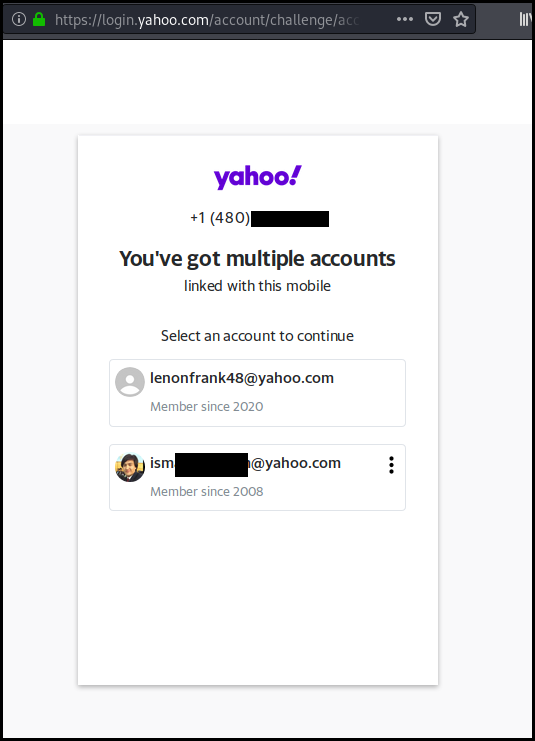
A weird case scenario that happened was triggered when the phone number was linked to two accounts. In this case, it was possible to reset both account's passwords.
On the picture below lenonfran48 was my account but the other one, starting with ism, was not.
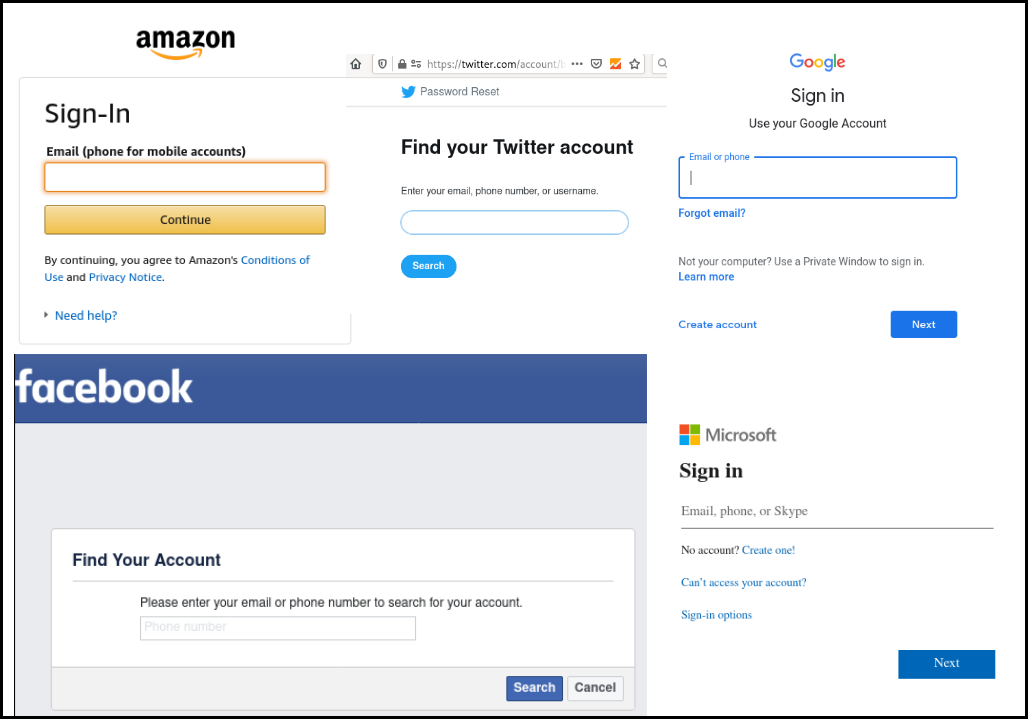
GAFAM
Yahoo! was not alone out there and a most of the GAFAM offered this function - Apple allowed to retrieve ones Apple ID but using its First name and Last name and email address:
Twitter specifics
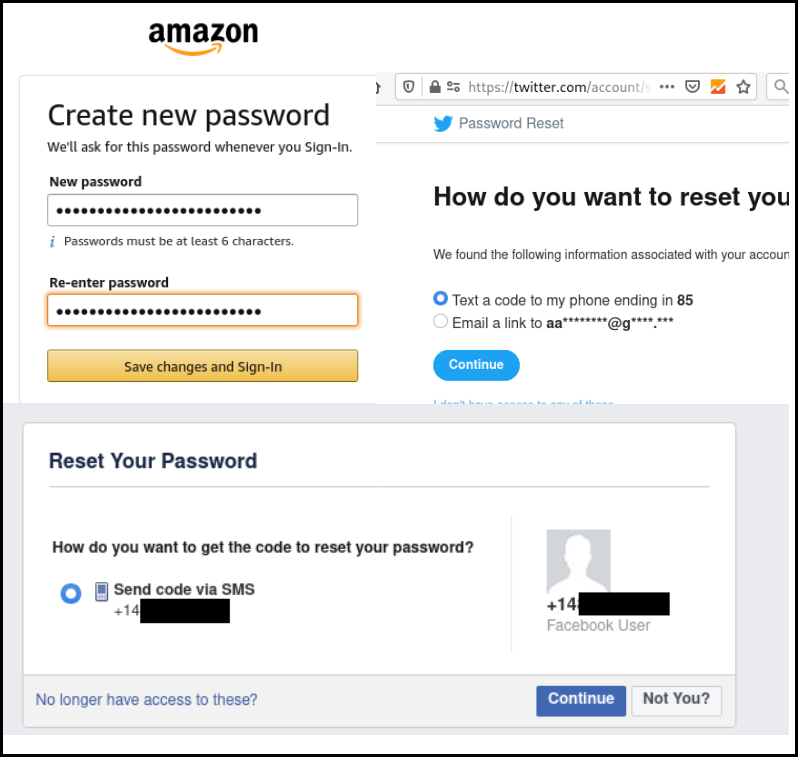
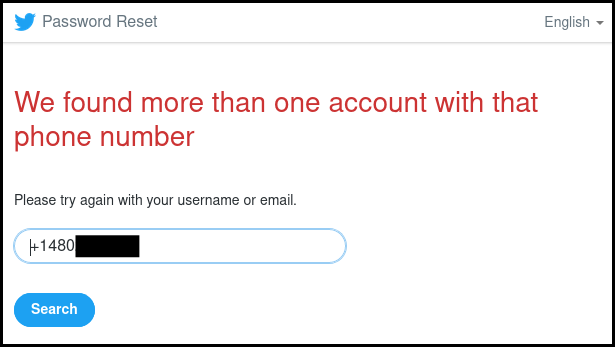
If there were two accounts link to a phone number, Twitter would not allow the user to reset its password using the phone number and asked to use the username or email address.
Google specifics
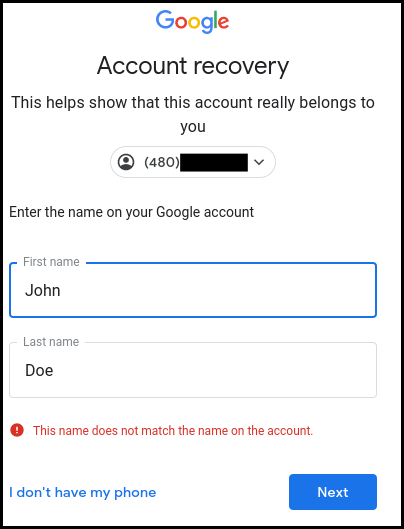
Google also allowed to use a phone number instead of an email to login and reset the account password. But, in order to show that the account really belonged to the person with the phone number, Google asks for personal information as the user First name and Last name.
Amazon specifics
As Google, Amazon was asking the credit card last number not before resetting the user password, but when accessing the "personal" section or putting an order.
Automation

Finding phone number
I needed a large input of phone number. For that I used three sources:
- Internal phone number: I extracted the phone number from my company as reaching a coworker on our internal chat to ask him to send me a text code is perfectly fine (after explaining the situation obviously)
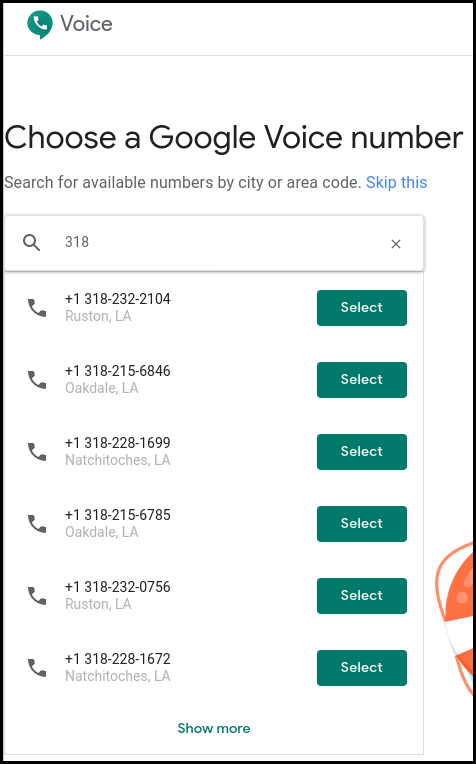
- Burner and Google voice: these services allowed to buy a temporary phone number and let you choose from a list allowing to test the number against the applications and buy the interesting numbers.
Scripting
A little bit of python or even using Burp intruder allowed to quickly retrieved the valid
phone numbers for each platform.
For instance, the python code to validate a phone number against Twitter was the following:
def check_number_twitter(phone_number):
s = requests.Session()
r = s.get(twitter_url, verify=False)
authenticity_token=''
soupe = BeautifulSoup(r.text, 'lxml')
for elem in soupe.find_all('input'):
if elem.get('name') == 'authenticity_token':
authenticity_token=elem.get('value')
payload = {'authenticity_token': authenticity_token, 'account_identifier': phone_number}
s.post(twitter_url, data=payload, verify=False)
r = s.get('https://twitter.com/account/send_password_reset', verify=False)
if 'a code to my phone ending' in r.text:
print('Twitter num found: {}'.format(phone_number))
else:
print(r.text, file=sys.stderr)
print('-------------------------------', file=sys.stderr)
print('', file=sys.stderr)
Results
The following table present the raw results obtained by running the collected number.
We see that Burner and Google Voice were not interesting sources in term of phone number. The reason is probably that the number were not really use by users as recuperation device.
Company phone number however were really interesting as they tend to be reuse phone number.
| Source | numbers | Yahoo | Amazon | |
|---|---|---|---|---|
| Company phones | 303 | 77 | 111 | 12 |
| Burner | 299 | 0 | 6 | 0 |
| Google Voice | 152 | 0 | 0 | 2 |
| TOTAL | 754 | 77 | 117 | 14 |
Fix
User side
A few recommendations for the end user:
- Renew your phone numbers.
- Keep an inventory of your phone number usage and update them as needed.
Application side
A few recommendations for the applications:
- Use an anti-brute force mechanism.
- Try to show the same message whether the phone number is link to an account or not.
- As Google and Amazon were doing ask for personal information before sending the email.
Conclusion
There is no real vulnerability here as this was mostly a user bad habit. Nonetheless, GAFAM could implement some simple fixes to protect their users from this kind of "attacks".