Flare-on Challenge 2018
Posted on 07 Oct 2018 in security • 4 min read
The fifth edition of the FireEye's Flare-on reverse challenge take place this year between august 24th and the 5th octobe with a total of 12 challenges centered on Windows binaries.
Minesweeper Championship Registration
Welcome to the Fifth Annual Flare-On Challenge! The Minesweeper World Championship is coming soon and we found the registration app. You weren't officially invited but if you can figure out what the code is you can probably get in anyway. Good luck!
We download the 7z and after extraction we got the jar.
We start jd-gui and load the jar.
The InviteValidator class is the following:
import javax.swing.JOptionPane;
public class InviteValidator
{
public static void main(String[] args)
{
String response = JOptionPane.showInputDialog(null, "Enter your invitation code:", "Minesweeper Championship 2018", 3);
if (response.equals("GoldenTicket2018@flare-on.com")) {
JOptionPane.showMessageDialog(null, "Welcome to the Minesweeper Championship 2018!\nPlease enter the following code to the ctfd.flare-on.com website to compete:\n\n" + response, "Success!", -1);
} else {
JOptionPane.showMessageDialog(null, "Incorrect invitation code. Please try again next year.", "Failure", 0);
}
}
}
We directly got the challenge flag GoldenTicket2018@flare-on.com.
Ultimate Minesweeper
You hacked your way into the Minesweeper Championship, good job. Now its time to compete. Here is the Ultimate Minesweeper binary. Beat it, win the championship, and we'll move you on to greater challenges.
Once unzip the file is a 32bits executable binary. $ file UltimateMinesweeper.exe UltimateMinesweeper.exe: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
When executed the program is similar to every Minesweeper execpt there is a LOT of mines! Only 3 squares of the 900 are not mines. The goal is to reveal this 3 squares with exploding on a mine.
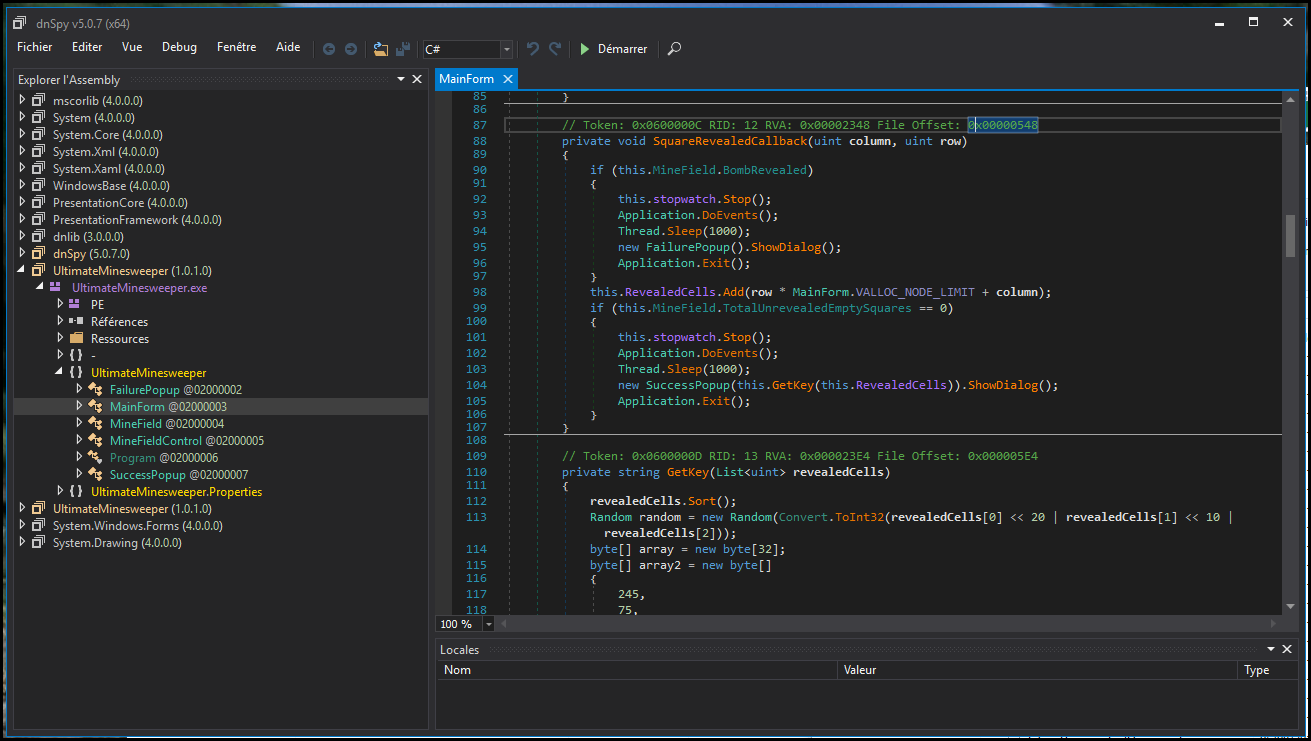
We can use a tool like DnSpy to decompile the .NET and access the source code.
We can even recompile the code. Nevertheless , the line 156 will fire a compilation error. In order to fix it, we need to convert the value to byte:
array3[(int)num2] = (byte)(array3[(int)num2] ^ array[(int)num]);
We can for instance disable the failure when revealing a mine by changing the
code of the BombRevealed function and make it always return false:
public bool BombRevealed
{
get
{
int num = 0;
while ((long)num < (long)((ulong)this.Size))
{
int num2 = 0;
while ((long)num2 < (long)((ulong)this.Size))
{
if (this.MinesPresent[num2, num] && this.MinesVisible[num2, num])
{
return false;
}
num2++;
}
num++;
}
return false;
}
}
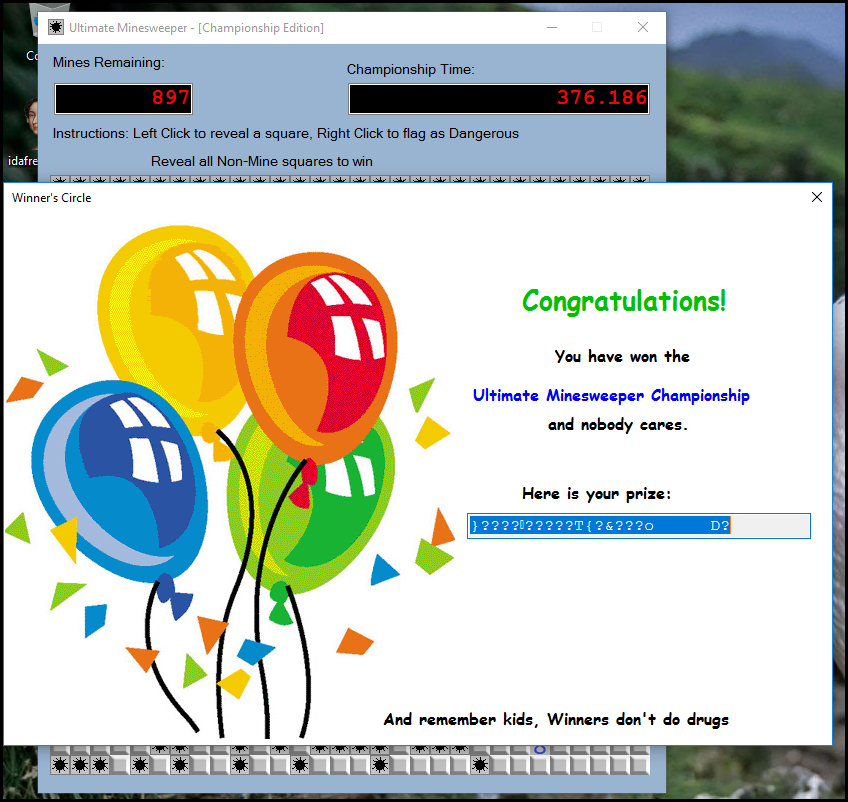
Then we can clic on every square and get the Success message.
The flag seems to be encoded. When looking at the function GetKey we see that
the Random is build using a seed depending of the revealed cells.
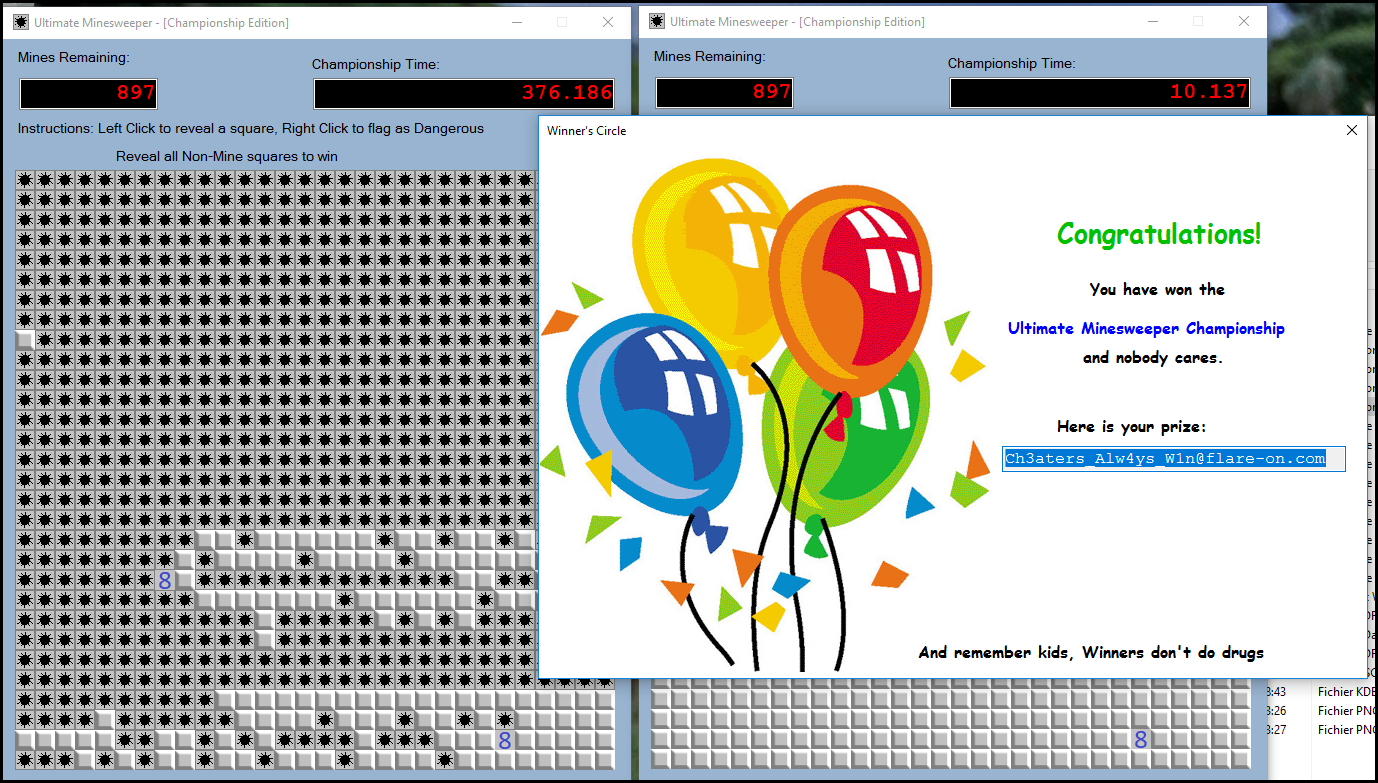
We then discover that the mines (and more importently the 3 empty squares) are always at the same place. So we can just found the position of every empty squares with our modified binary.
And then just reveal this three squares in order to get the Success message with the flag.
FLEGGO
When you are finished with your media interviews and talk show appearances after that crushing victory at the Minesweeper Championship, I have another task for you. Nothing too serious, as you'll see, this one is child's play.
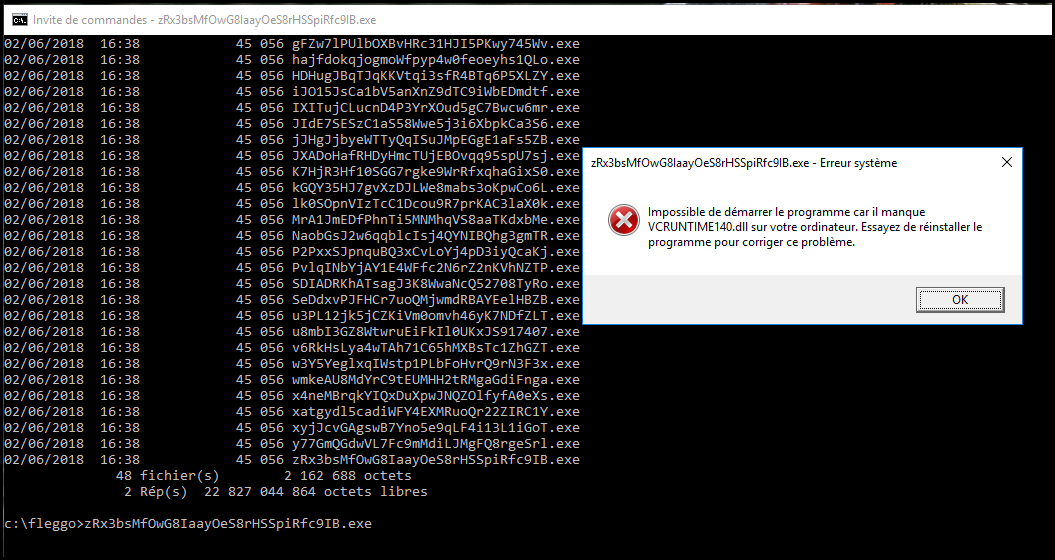
Once extraxted we get 48 executables. Each binary is a 32bits executable.
$ file ./*
./1BpnGjHOT7h5vvZsV4vISSb60Xj3pX5G.exe: PE32 executable (console) Intel 80386, for MS Window
When launching any of the executable we get an error about the VCRUNTIME140 DLL missing.
To fix this you just need to install Visual Studio Community Edition.
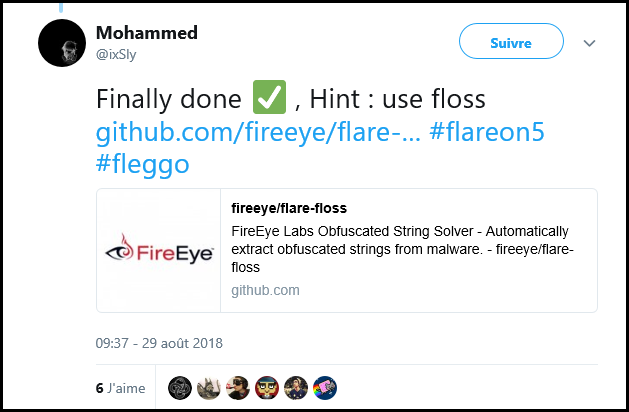
After a few try using IDA and OllyDBG, I found a hint on twitter:
FLOSS static UTF-16 strings
@BRICK
%s\%s
IronManSucks
Oh, hello Batman...
I super hate you right now.
What is the password?
%15ls
Go step on a brick!
Oh look a rainbow.
Everything is awesome!
%s => %s
BRICK
ZImIT7DyCMOeF6
FLOSS decoded 0 strings
FLOSS extracted 0 stackstrings
Finished execution after 2.266808 seconds
The binary password is given just after the BRICK string.
root@kalili:~/work/fleggo# wine 1BpnGjHOT7h5vvZsV4vISSb60Xj3pX5G.exe
000f:err:service:process_send_command receiving command result timed out
What is the password?
ZImIT7DyCMOeF6
Everything is awesome!
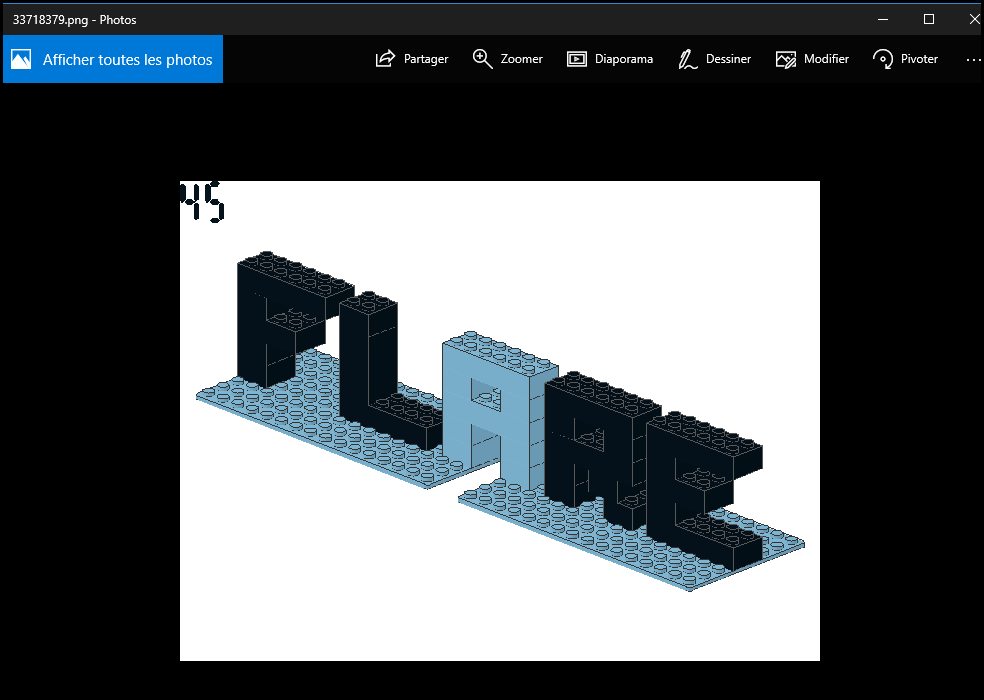
65141174.png => w
An image is created associated to a character.
We can automatized this for the 48 binary:
root@kalili:~/work/fleggo# for f in *exe; do wine $f <<< `./floss $f | grep '^BRICK' -A 1 | grep -v BRICK` ; done
000f:err:service:process_send_command receiving command result timed out
What is the password?
Everything is awesome!
65141174.png => w
000f:err:service:process_send_command receiving command result timed out
What is the password?
Everything is awesome!
85934406.png => m
<SNIP>
A simple redirection allow to keep the information in a file. In the corner of each image is the position of the associated charactere. (for instance the image 85934406.png is associated to the letter "m" and the number in the right corner is 35 so the "m" is in the 35th position).
We might use tesseract in order to automaticaly detect the number in the corner. But I manualy identify them and got the order of the flag:
mor3_awes0m3_th4n_an_awes0me_p0ssum@flare-on.com
binstall
It is time to get serious. Reverse Engineering isn't about toys and games. Sometimes its about malicious software. I recommend you run this next challenge in a VM or someone else's computer you have gained access to, especially if they are a Firefox user.
Once unzip we get a simple executable.
$ file binstall.exe
Downloads/binstall/binstall.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows
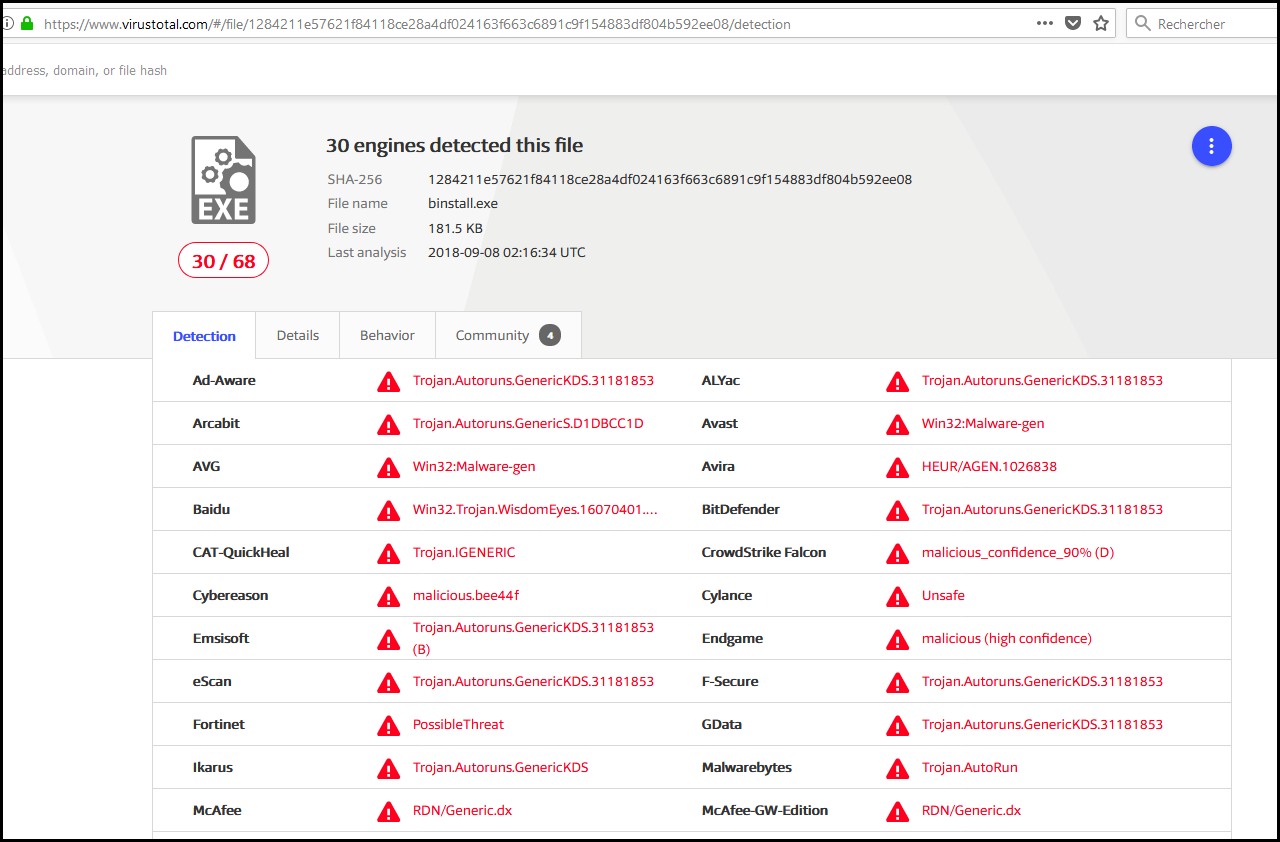
As said in the descritpion this file is a malware and a lot of AV detect it as someone uploaded it on virus total.
I didn't get a lot of time to work on this challenge and didn't solve it.
Contest ending
The contest is now over and fireEye realse the solution for all challenges.