Vault
Posted on 08 Feb 2020 in security • 4 min read
"Secure, store and tightly control access to tokens, passwords, certificates, encryption keys for protecting secrets and other sensitive data using a UI, CLI, or HTTP API."
Presentation
Install
Just go on the download page and get the package adapted to your system. Once you extract the downloaded zip, you will get a binary. Execute it without any option to get the help menu.
$ ./vault
Usage: vault <command> [args]
Common commands:
read Read data and retrieves secrets
write Write data, configuration, and secrets
delete Delete secrets and configuration
list List data or secrets
login Authenticate locally
agent Start a Vault agent
server Start a Vault server
status Print seal and HA status
unwrap Unwrap a wrapped secret
Other commands:
audit Interact with audit devices
auth Interact with auth methods
debug Runs the debug command
kv Interact with Vault's Key-Value storage
lease Interact with leases
namespace Interact with namespaces
operator Perform operator-specific tasks
path-help Retrieve API help for paths
plugin Interact with Vault plugins and catalog
policy Interact with policies
print Prints runtime configurations
secrets Interact with secrets engines
ssh Initiate an SSH session
token Interact with tokens
Getting started
Running dev server and exporting the vault address
The dev server is a built-in, pre-configured server that is not very secure but useful for playing with Vault locally.
$ ./vault server -dev
$ export VAULT_ADDR='http://127.0.0.1:8200'
We can get the server status with the status command. The server is
initialized and unsealed.
$ ./vault status
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 1
Threshold 1
Version 1.3.0
Cluster Name vault-cluster-f6bdd069
Cluster ID 14ded467-9ad3-3fc4-4403-bea46156b766
HA Enabled false
This article will not describe the vault's tutorial. If you want to manipulate vault: vault's getting started.
Vault for pentesters
What is really interesting is how to steal vault's secrets and maybe escalate your privileges. For the following we simulate a situation where we compromised a GNU/Linux box and get a user shell.
Detecting the vault
First of all we need to know of vault is running on the machine. For that we can
run a simple ps.
$ ps aux | grep vault
root 2442 0.0 3.3 69564 68136 ? SLsl 06:56 0:01 vault server -config /vault/config/config.hcl
Login
Then we need to login on the vault in order to get some information. Vault allow sixteen login methods. Here we will present only two of them:
- token: the default method, a token is use to identify the user.
- username: "classical" username/password authentication method
In order to use a non default method you need to use the --method option for
instance:
$ vault login -method=userpass username=my-username
Password (will be hidden):
For more information about vault's authentication methods.
In order to get a foothold on the vault instance we will need some credentials: enumerate!
Root policy
Once login on the vault we can list our permission if we are in the "root" policy we get a root access to the vault and can access every secret.
$ vault login
Token (will be hidden):
Success! You are now authenticated. The token information displayed below
is already stored in the token helper. You do NOT need to run "vault login"
again. Future Vault requests will automatically use this token.
Key Value
--- -----
token f1783c8d-41c7-0b12-d1c1-cf2aa17ac6b9
token_accessor 1dd7b9a1-f0f1-f230-dc76-46970deb5103
token_duration ∞
token_renewable false
token_policies ["root"]
identity_policies []
policies ["root"]
If you do not have access to the "root" policy, you will still have access to some secrets, maybe only with the right permissions.
Either ways, you should enumerate and see what you can do from there.
Enumerating the secrets engines
It is quit simple to list the available secrets engine (for a more detailed
output you can add the -detailed parameter):
$ vault secrets list
Path Type Description
---- ---- -----------
cubbyhole/ cubbyhole per-token private secret storage
secret/ kv key/value secret storage
sys/ system system endpoints used for control, policy and debugging
Enumerating the secrets for an engine
Once you know which secrets engines are running you will be able to list the secrets from them.
Here we will list the secret from the basic kv (key-value) secrets engine.
If the vault is accessible with HTTP, open your browser and login to list graphically the available information.
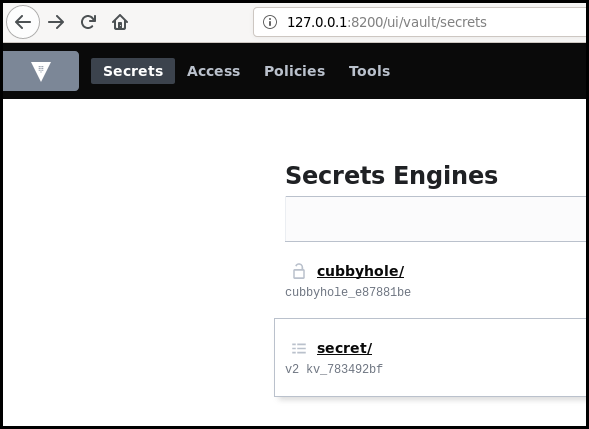
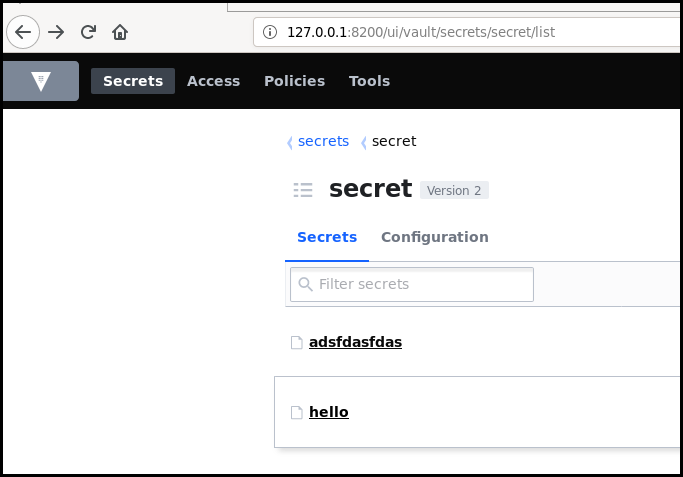
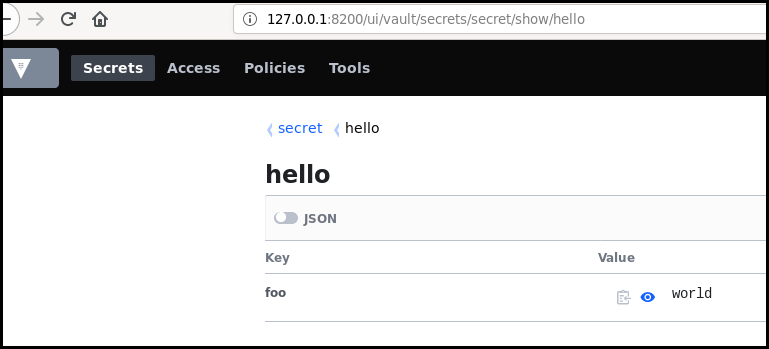
If you do not have access to a web interface, you can list the secret using the CLI.
$ ./vault kv list secret/
Keys
----
adsfdasfdas
hello
$ ./vault kv list secret/
Keys
----
adsfdasfdas
hello
$ ./vault kv get secret/hello
====== Metadata ======
Key Value
--- -----
created_time 2019-11-15T14:10:00.428186002Z
deletion_time n/a
destroyed false
version 2
=== Data ===
Key Value
--- -----
foo world
SSH
Vault allow to store other object than key:value couples. For instance it is possible to configure Vault to provide a one time password to connect with ssh to a remote server (with the contribution of an ssh-helper client side. More information on how to install this: documentation OTP SSH)
Once installed and configured it allow to connect to "remote" host:
user@vm:~$ vault ssh -mode=otp -role=root_otp root@127.0.0.1
Vault could not locate "sshpass". The OTP code for the session is displayed
below. Enter this code in the SSH password prompt. If you install sshpass,
Vault can automatically perform this step for you.
OTP for the session is: 3ee17d0c-1eef-a286-fd6d-e50702c38c00
Password:
root@vm:~# id
uid=0(root) gid=0(root) groups=0(root)
This might allow you to pivot from the compromised host to another.
Short conclusion
This article just scratch the vault surface as there is eighteen secrets engine at the moment and I have not speak about sealing and unsealing the vault. This solution can resolve some authentication and secret sharing issues but it is crucial that the vault's authentication secrets are well keep.