HTB: Swagshop
Posted on 29 Sep 2019 in security • Tagged with security, boot2root, HTB, linux, mangento • 6 min read
This article is a writeup about a retired HacktheBox machine: Swagshop This box was suppose to be an easy one. Turns out it wasn't. I struggle a lot in wrong direction and finally found a path to root this magento box.
This article presents the different methods which failed on the box as well as the solution to root it.
Continue reading
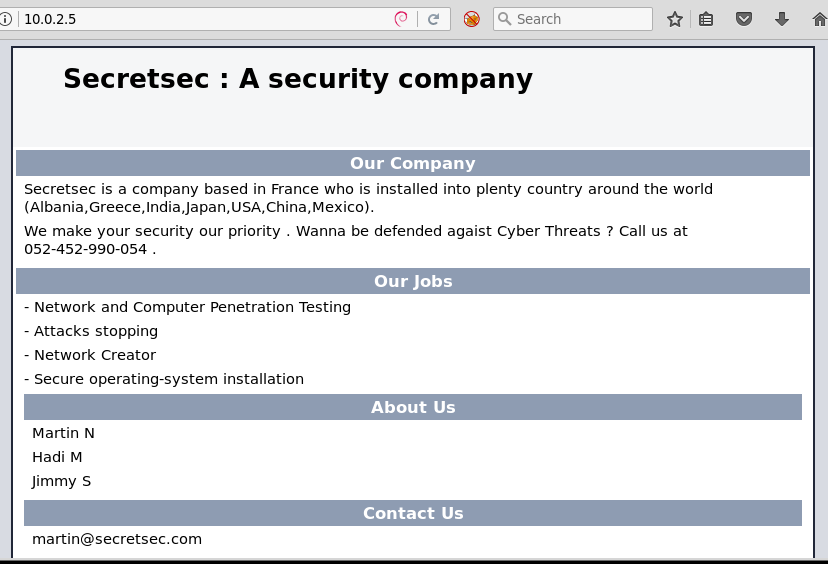
 A few days ago, I installed a new pentesting box based on Arch Linux with Kali
A few days ago, I installed a new pentesting box based on Arch Linux with Kali