HTB: Jerry
Posted on 12 Sep 2019 in security • Tagged with security, boot2root, HTB, windows • 3 min read
I started to work on Hack The Box machines in 2018. This is a writeup for the retired Jerry machine.
Continue reading
Posted on 12 Sep 2019 in security • Tagged with security, boot2root, HTB, windows • 3 min read

I started to work on Hack The Box machines in 2018. This is a writeup for the retired Jerry machine.
Posted on 07 Oct 2018 in security • Tagged with security, reverse • 4 min read
The fifth edition of the FireEye's Flare-on reverse challenge take place this year between august 24th and the 5th octobe with a total of 12 challenges centered on Windows binaries.
Posted on 20 Nov 2017 in security • Tagged with security, vulnhub, boot2root, linux • 5 min read
Posted on 10 Nov 2017 in security • Tagged with security, vulnhub, hash, boot2root, linux • 5 min read
At the moment I have some times to work again on Vulnhub virtual machine. So here I picked the first one at the moment: Bulldog: 1 A simple boot2root machine by Nick Frichette.
Posted on 01 Aug 2017 in security • Tagged with security, cryptography, code review • 3 min read
I recently did a code review assessment on an application for one of my client. The best part of the application was their own cryptography algorithm.
Moreover, the application was written in PHP and PHP do some strange things with string, characters and XOR operations. It only needed a few lines of python in order to break it.
TL;DR : please do not write your own crypto!
Posted on 22 Jan 2017 in security • Tagged with security, ctf • 8 min read
This week-end was the insomnihack teaser CTF. I participated with the team The Half Crunchy.
The theme was "RISE OF THE MACHINES" with rogue webserver and flawing cat robot.
We finished 42th with 550 points flagging 5 challenges:
[TOC]
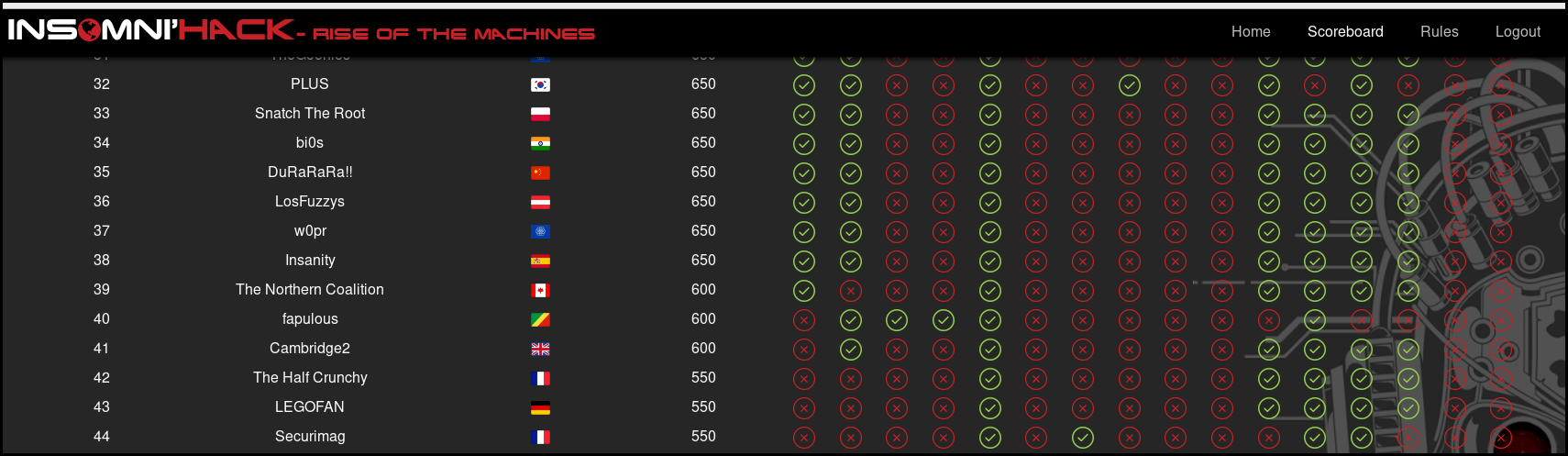
Many thanks to the organisation! It was a really nice CTF.
Thanks to all team members who participated.
Posted on 27 Dec 2016 in security • Tagged with programming, SSL, let's encrypt, security • 3 min read
Let's encrypt provide free and easy SSL certificates. Nevertheless it need to verify that you own the machine. In order to do that we usually use HTTP verification with the .well-known directory.
But sometime our servers are not reachable from the internet. Therefore the HTTP validation is not possible. Hopefully there is another way the acme challenge can be validated: DNS validation.
In this post we will see how we can generate Let's encrypt SSL certificate for offline machine with DNS validation for domains hosts by OVH.
Posted on 26 Dec 2016 in security • Tagged with programming, security, chrome, kiosk • 3 min read
Building a Kiosk where Google Chrome is running in full screen and user interaction with the system are reduced to the minimum.
Posted on 11 Dec 2016 in security • Tagged with cve, security, exploit • 2 min read

Dirty COW (CVE-2016-5195) is a privilege escalation vulnerability in the Linux Kernel. "A race condition was found in the way the Linux kernel's memory subsystem handled the copy-on-write (COW) breakage of private read-only memory mappings. An unprivileged local user could use this flaw to gain write access to otherwise read-only memory mappings and thus increase their privileges on the system." (Source: Red Hat)
Posted on 23 Jul 2016 in security • Tagged with cve, security, exploit • 2 min read
The 13th if July a new wild CVE appeared (Yes, Pokemon Go is still a buzz for the moment).
The CVE 2016-6210 allow a user enumeration on an SSH server by comparing request time between non existing user and allowed ones. This vulnerability target OpenSSHD with a version of 7.2p2 or inferior.
That means with a good dictionary you may know which user are present on the server with an SSH access.
This post just demonstrate how to exploit this vulnerability with a simple example.